
Sometimes being first to market is everything, and sometimes it is not. If you’re too far ahead of the market for adoption, a great product could die on the vine since no one is ready for it. If you get the timing right and your product is a world class leader – as demonstrated in the 2016 Forrester Privileged Identity Management Wave – you might be able to set the pace for the rest of the players in the field.
BeyondTrust is Setting the Pace
With the first and only privileged access and vulnerability management platform (BeyondInsight) available in the Amazon AWS Marketplace – for all businesses, application developers, and managed service providers – BeyondTrust is now the breakaway leader in privileged access management.
This solution is the first of its kind with Bring Your Own Licensing (BYOL) that can be used with:
- PowerBroker Password Safe – Complete management of passwords including workflow, session recording, API access, and analytics
- PowerBroker for Unix & Linux – Command elevation and delegation for Unix and Linux systems
- PowerBroker for Windows – Least privilege and application control with patented technology for Microsoft Windows desktops and servers
- PowerBroker for Mac – Least privilege application management for Mac OS X
- Retina CS – Vulnerability assessment, regulatory reporting, and remediation
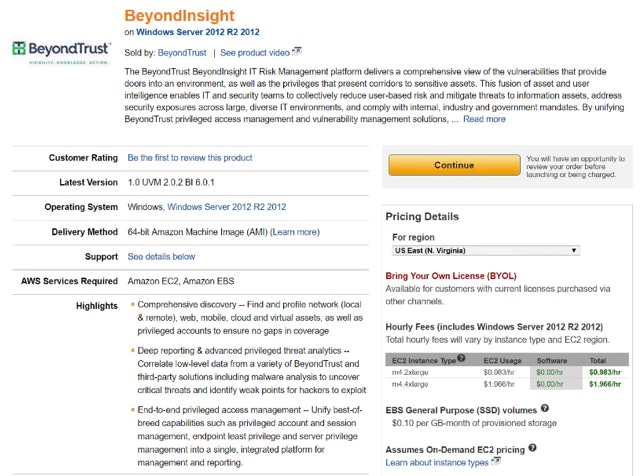
Announcement Enhances Cloud Strategy
While this announcement represents a new offering for BeyondTrust and our platform (currently also available as software, virtual and physical appliances), it significantly enhances our strategy in the cloud by providing the necessary resources to manage cloud instances, cloud services, and cloud applications. This means that customers can use our industry-unique cloud connectors for managing other cloud instances and passwords, and not only for Amazon. Cloud platform support includes:

Why This Announcement Matters to our Customers
For any business considering moving to the cloud, avoiding more on premise technology, or trying to manage a vast number of roaming laptops or remote employees, this offering is for you.
By enabling BeyondTrust’s privileged access management and vulnerability management solutions in the cloud, we can meet objectives for a rapid deployment, secure access, and a cost effective solution to eliminate the threats of excessive privileged access.
Get direct access to the Amazon AWS Marketplace and the BeyondInsight AMI, by visiting the Amazon Marketplace. To obtain new licenses for your AMI instance, please contact BeyondTrust Sales.
As Mel Brooks said in History of the World Part I, “It’s good to be the king”. For the benefit of our customers, it’s a great time to be the first to market.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








