Protect against phishing, ransomware, and malware attacks with least privilege and application control that deploys in hours and keeps your workers productive.
Today, BeyondTrust announced our industry-leading Privilege Management for Windows & Mac solution is now available as SaaS (software-as-a-service). Our SaaS-based solution empowers organizations to eliminate admin rights quickly and efficiently across Windows and Mac endpoints, without disrupting user productivity. With BeyondTrust PAM SaaS solutions, customers get the best of both worlds, removing the burden of managing their infrastructure, while enjoying the feature-richness of the cloud and the flexibility of a subscription-based model.
According to BeyondTrust’s Microsoft Vulnerabilities Report 2020, of the 192 Critical Microsoft vulnerabilities reported by Microsoft, 77% could be mitigated by removing local admin rights from users. BeyondTrust Endpoint Privilege Management deployments protect over 50 million endpoints across the globe, including for the most demanding security and compliance-driven environments across government and industry. Our solutions are built to effectively protect under the most challenging scenarios and broadest range of edge use cases to help organizations ensure their entire universe of privileges is secure.
Why Cloud-Based Endpoint Privilege Management, & Why Now?
The trend toward increased reliance on SaaS solutions has been well underway for IT security and has only accelerated due to the COVID-19 pandemic. For instance, social distancing has necessitated remote work, and sometimes BYOD, suddenly and at great scale. While these challenges, along with the recent growth spurt of shadow IT, are themselves drivers for endpoint privilege management and application control, they also benefit from the agility and flexibility of the Cloud. Thus, it’s unsurprising that we’re seeing an increased push toward SaaS deployments and to privilege management and application control solutions. Today, more than 3,000 customers leverage full management capabilities of BeyondTrust solutions in the Cloud.
Privilege Management for Windows & Mac, along with BeyondTrust’s Secure Remote Access and other privilege management solutions, is strongly poised to help organizations rapidly and effectively address the urgent needs of today’s environment, and well beyond.
Key Capabilities and Benefits of SaaS Privilege Management for Windows & Mac
The SaaS deployment of BeyondTrust’s Privilege Management for Windows & Mac solution provides the same robust features and capabilities as the on-premises deployment. Privilege Management for Windows & Mac securely enables the precise level of privileged access end users need to perform their daily roles, without giving them full administrative rights. The solution dynamically enforces true least privilege – enabling just enough access and just-in-time access.
Here are some of the cloud-based solution’s key features and benefits:
- Removes admin rights and enforces least privilege policies across Windows desktops/servers and MacOs quickly
- Protects desktop and server endpoints from malicious attacks like phishing, malware, and ransomware
- Achieves rapid time-to-value with SaaS deployments and Quick Start policies for immediate risk reduction
- Empowers employees with the access to applications they need for maximum productivity
- Minimizes costs from IT staff and infrastructure
- Reduces the burden on IT and Service Desk teams
- Monitors, controls, and audits sessions
- Addresses rigorous compliance initiatives with in-depth reporting available at your fingertips
- Ensures employees have the tools they need for maximum productivity
What Differentiates BeyondTrust Privilege Management for Windows & Mac Versus Competitor Solutions
BeyondTrust not only offers a more complete endpoint privilege management solution than competitors, but also one that can be deployed overnight and at scale. Our solution also complements the traditional privilege elevation and delegation capabilities expected of an endpoint privilege management solution with advanced application controls capabilities. Working together, these capabilities dramatically lower your attack surface, while also boosting business and operational productivity.

Beyond privilege elevation and delegation, here are some powerful features unique to our solution:
QuickStart Templates: These flexible workstyle templates for Windows & Mac devices enable overnight policy implementation across all users or groups of users to immediately—from Day 1—reduce the risk of unmanaged endpoints.
Application Control: This encompasses allow listing, block listing, and greylisting. Leverage a flexible policy engine to set broad rules, choose automatic approval for advanced users - protected by full. audit trails, or even utilize challenge-response codes.
Trusted Application Protection (TAP): Building on the foundation of privilege management and application control, TAP provides pre-built templates that stop malware and living off the land attacks in Windows systems. Trusted Application Protection adds context to the process tree, allowing restriction of common attack chain tools, such as PowerShell and Wscript that are spawned from commonly used applications, such as browsers or document handlers (Word, PowerPoint, Excel). TAP does not rely on reputation or signatures.
Power Rules: Business rules for Windows systems decide which applications are safe, speed decisions on whether to allow an application to run, or allow it to run with admin rights, by automating the integration of third-party intelligence sources. Based on PowerShell, organizations can simply write a script and embed it in the policy itself. For example, when it runs, the PowerShell script can automatically trigger a service desk workflow, generating a helpdesk ticket that provides all of the information they require about the application or task. Another example would be for it to call out to a third party to check the hash, or to a vulnerability management system to check for CVEs on the application
Our cloud-based Privilege Management for Windows & Mac solution is rounded out by best-in-class privileged threat analytics, a wealth of free and customizable reports, and the industry’s best session auditing and management capabilities. Our solution’s unique capabilities, combined with our experience securing privileges for the largest number of endpoints, has benefitted our customers with a roll-out approach that gives them leaps in endpoint protection, risk reduction, and productivity from Day 1.

We understand that some IT teams have had, a sub-optimal experience in rolling out alternative privilege management solutions. In some of the worst instances, these solutions become shelfware because they’re exasperatingly difficult to deploy and manage. BeyondTrust’s SaaS deployment of Windows and Mac endpoint privilege management is the closest thing to flipping a switch. The solution’s security features and QuickStart capabilities deliver rapid time-to-value. Here’s a simple visualization of what that timeline looks like:
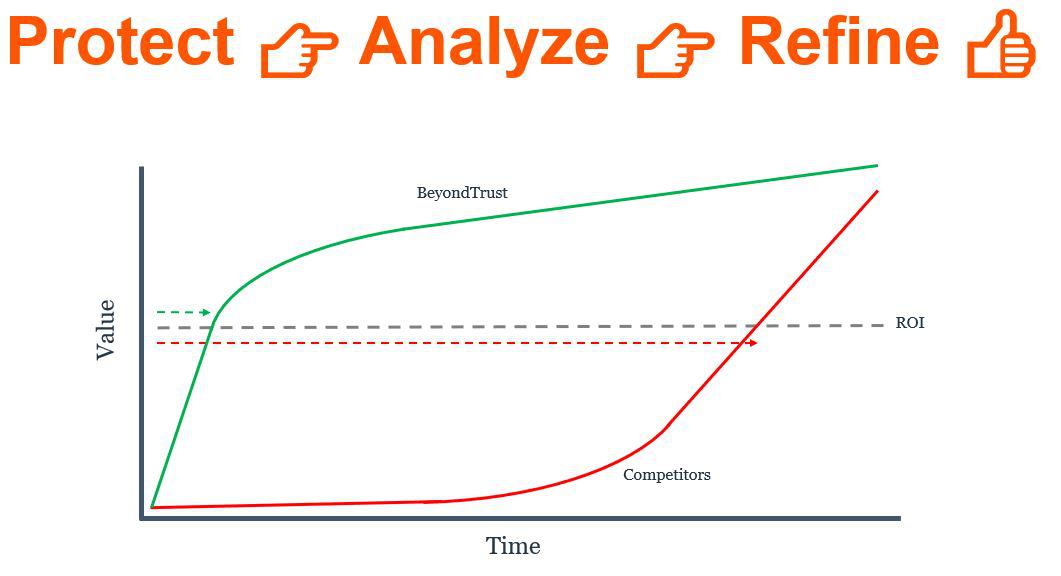
Unlike competitor privilege management products that can take months to properly configure, Privilege Management SaaS overnight policy implementation across all users or groups of users to immediately reduce the risk of unmanaged endpoints. Over time, you can continue to refine your deployment to reaping additional risk-reduction and enhanced productivity benefits.
Learn More about Privilege Management for Windows & Mac
Privilege Management SaaS is a core offering within BeyondTrust’s complete Privileged Access Management (PAM) portfolio.
Related Resources
A Guide to Endpoint Privilege Management (white paper)
Quick Start Privilege Management for Windows & Mac (data sheet)
Privilege Management for Windows and Mac (web page)
Privilege Management for Windows & Mac (Desktops) (data sheet)
Privilege Management for Windows & Mac (Servers) (data sheet)
Quick Guide: Enable & Secure Your Remote Force (white paper)

Peter Knight, Sr Director, Product Management
I have been working in a variety of product management roles since 2006 across diverse industries. I firmly believe in putting the customer at the heart of what I do, and that delivering quality solutions and products is based on a deep understanding of your customers’ world. As a senior product manager, I care about the experience we deliver to our customers, not just the technology or functionality wrapped into a product. I always enjoy discussing issues and challenges with customers to get a clear picture of what we need to solve today, tomorrow, and into the future.








