I’m proud to share that, for the fifth consecutive year, BeyondTrust has been recognized as a Leader in the Gartner® Magic Quadrant™ for Privileged Access Management! This year, BeyondTrust was recognized as one of only three PAM Leaders and was also positioned highest in Ability to Execute.
In our opinion, this Gartner® recognition validates BeyondTrust's dynamic market adaptation, powerful product features, and the earned trust placed in us by a substantial and contented customer base. We believe receiving recognition for five years running as a PAM Leader in the Gartner® Magic Quadrant™ also reflects our commitment to innovation, deep understanding of evolving market needs, and relentless dedication to our customers.
Gain complimentary access to the report and read it for yourself anytime here.
Read on for our view on key takeaways from the 2023 PAM MQ™.
Our View: Key Takeaways from the 2023 Gartner® Magic Quadrant™ for Privileged Access Management
Gartner® Magic Quadrant™ research methodology provides a graphical competitive positioning of four types of technology providers in fast-growing markets: Leaders, Visionaries, Niche Players and Challengers. As companion research, Gartner Critical Capabilities notes provide deeper insight into the capability and suitability of providers’ IT products and services based on specific or customized use cases.
The BeyondTrust Platform addresses both established and transformational identity and security trends included in this year’s report.
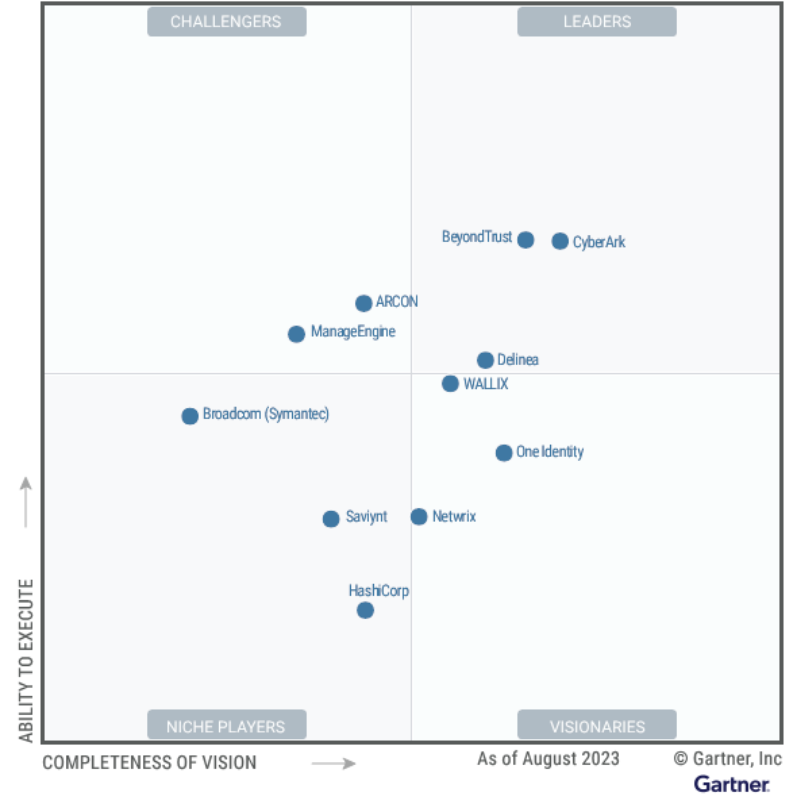
The 2023 Magic QuadrantTM for Privileged Access Management (PAM) has witnessed significant evolution, in part due to the growing involvement of cybersecurity insurers. These insurers are encouraging organizations to implement robust PAM strategies as a prerequisite for insurance coverage, thereby accelerating first-time PAM purchases.
Another notable trend is the rising interest in remote PAM use cases, spurred by the global shift to remote work and the outsourcing of core IT services. PAM solutions are broadening their scope to include remote vendors, contractors, and DevOps initiatives. Vendors like BeyondTrust are leading the way with specialized tools for remote PAM.
Get the full report to read deeper about the view of Gartner on these topics.
Why BeyondTrust Stands Out in Identity Security
As we’re consuming the report, here are a few reflections, on my part, on why we are a consistent Leader year over year.
Pioneering Protection Against Identity Threats
The digital landscape has grown increasingly intricate, due to factors like remote work and cloud adoption, making identity protection more challenging than ever. A majority of penetration tests reveal vulnerabilities related to over-privileged cloud identities, and attackers are now using advanced technologies like AI for more potent threats.
Our Identity Security Insights solution addresses these modern challenges head-on by integrating with trusted identity providers and cloud services. Offering real-time threat analysis, it provides a unified view of identities, entitlements, and privileged access, while suggesting actionable security enhancements.
Meeting Emerging Needs in Remote Access
Remote access has emerged as a key area of interest, accelerated by global remote working trends and the COVID-19 pandemic. Organizations are scrutinizing how to securely manage access for remote vendors, contractors, and technicians. These solutions now often include zero-trust features, providing far more than just VPN access, and they extend to specialized needs like cloud infrastructure access.
BeyondTrust provides robust and mature Vendor Privileged Access Management (VPAM) and Cloud Infrastructure Access capabilities as integral features of our Privileged Remote Access solution. Our VPAM functionality allows secure, streamlined access for trusted vendors, effectively eliminating the need for vulnerable VPNs and shared credentials. On the cloud infrastructure front, we empower your cloud developers and DevOps teams with seamless yet secure connectivity, bolstered by robust authentication and comprehensive audit trails.
Our Customers
But what truly speaks volumes? It's not just accolades, but the real-world impact we've had on our clients. With an impressive NPS score of +55 and a CSAT score exceeding 95%, it's evident that our efforts align with customer satisfaction and excellence.
Our Leadership placement in the MQ™ follows BeyondTrust having been recognized as a “Customers’ Choice” for both Privileged Access Management (PAM) and for Remote Desktop Software by Gartner Peer Insights. We believe a common thread between the Gartner MQ™ and this distinction is our customers and the trust they place in us. We're honored to work alongside visionary organizations that drive us to innovate faster to solve their hardest digital identity challenges.
Here are just a few recent customer stories that showcase how BeyondTrust helps organizations improve their identity security posture:
- Investec transitioned from a theoretical framework to practical Zero Trust
- ServiceNow enhanced system access and authorization security
- Norton Healthcare successfully achieved HIPAA Compliance with BeyondTrust
Looking Ahead
Though the Gartner® Magic Quadrant™ provides a thorough, expert-driven overview of the PAM vendor landscape, BeyondTrust’s dedication to innovation remains unwavering. Following the April 2023 cut-off date highlighted in the report, BeyondTrust has rolled out a series of notable product launches. Here are some more recent product enhancements:
- Privilege Management for Windows and Mac included Analytics v2 enhancements for intuitive data aggregation, Role-Based Access for APIs to ensure granular control over permissions, and DLL Control to easily block risky DLLs.
- Remote Support was updated to offer FIDO2/YubiKey support for passwordless authentication and API Cookbooks to streamline Jump Item management.
- Privileged Remote Access saw new features like FIDO2/YubiKey support for remote users, streamlined vendor onboarding via automation, and optimized Jump Clients for cloud assets.
- Password Safe received a major upgrade, including Terraform Integration for enhanced CI/CD workflows, an Azure DevOps Extension for secure secret retrieval, and OAuth 2.0 standard implementation for secure authentication. The update also included improved accessibility via the web portal and enhanced audit and compliance reporting capabilities.
Notably, we also expanded strategic Technology Alliance Program initiatives like ServiceNow integration for Password Safe and a partnership between BeyondTrust's Privileged Remote Access and PingOne DaVinci for streamlined least privilege access management.
These innovations collectively underscore BeyondTrust's commitment to providing comprehensive and secure solutions that address a range of user needs and regulatory compliance demands, enhancing both efficiency and security posture for organizations.
Thank you for an Incredible Year—More Awaits in 2024
2023 has been a monumental year for BeyondTrust. We released significant new solutions and saw incredible customer and community growth. There are many trends and capabilities to consider, but you don’t need to go it alone. We’re pleased to provide access to the 2023 Gartner® Magic Quadrant™ for Privileged Access Management to help you evaluate solutions against your unique objectives and requirements. Download your complimentary copy of the report.
Disclaimer: Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner and Magic Quadrant is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.

Natalie Blake, Director, Analyst Relations
As the Director of Analyst Relations at BeyondTrust since 2022, Natalie spearheads the strategy and execution of BeyondTrust's global analyst relations program, collaborating cross-functionally with diverse teams. Based in Denver, Natalie cherishes quality time outdoors with her three children, exploring all that her beautiful city offers. Natalie's commitment to excellence and family values guide her professional and personal journey.








