Data Protection a Moving Target in the Work-from-Home (WFH) Era
The attacker’s path of least resistance (POLR) to corporate data and assets is shifting, thus, so too must our IT risk management calculus and defensive priorities. The defenses I’m talking about include physical security as well as cybersecurity technologies.
In this blog, we will explore how the attack surface is changing, why this is re-shaping the path of least resistance for attackers, what a recalibration of physical security and cybersecurity entails, and best practices for protecting identities, data, and corporate assets going forward.
Understanding Physical vs. Cybersecurity & the Attack Pathways
Physical security within corporate environments tends to be robust. It includes controls like key cards, biometric door locks, guard gates, camera systems, and more. For most attackers, this environment requires considerable effort to penetrate—especially without detection. Sure, there are heavily trafficked environments where an attacker could tailgate in—gaining access by a friendly, trusting employee holding open a door, or just slipping in behind an employee the instant the door has been opened via keycard or biometric authentication. But once inside a corporate office, there are still levels of physical and cyber access the intruder must typically navigate to gain system and data access, and during that time, they are exposed to humans and surveillance. Even malicious insiders looking to conduct cybercrimes would be cautious and deterred from acting illicitly onsite a corporate office environment with many eyes on them—both human and machine. Additionally, physical security penetration tests are effective at revealing potential flaws, helping provide a clear path to remediation to further tighten physical security.
Remote access, however, bypasses all the physical controls and potentially gives a threat actor direct access to the data. Over the past decade, most IT security breaches have been remotely perpetrated. Remote access has been the path of least resistance to the identities, access, and data that the threat actors seek. The small slice of data breaches that were committed on-premises typically did involve some form of insider threat and direct access to sensitive systems and data. But again, these latter on-premise breach instances are a statistical rarity. With that said, mobile device threats have been on the rise and responsible for a growing share of data breaches, most notably in the healthcare industry.
Largely, the physical security in corporate environments is working, and it’s the cybersecurity controls that have, in recent years, been the path of least resistance. If we broke breach data down further, we would see that the most glaring security deficiencies are around password management, securing privileged identities/access, and remote access.
Why a New Path of Least Resistance is Changing the Calculus for Cyber Attackers
So, with the “new normal” what specifically has changed, and consequently, how must risk management and security be recalibrated? I think the answers are interesting for CISOs and IT security professionals everywhere, and are three-fold:
1. The cybersecurity deficiencies noted above (insecure remote access, proliferation of unmanaged privileges and credentials, etc.), have only been exacerbated as more employees and vendors work from home, digital transformation accelerates, and as the cloud presence increases. In particular, the gaps in privilege management and remote access pathways have proliferated.
Almost every attack (malware, hacker, etc.) today requires privilege—either to execute and initially compromise an environment, and/or to move laterally within an organization’s systems. Human and machine privileges—long a security weak spot for organizations—have only gotten more challenging to find and control with the many planes of privileges being created at great scale due to the cloud, virtualized environments, and IoT. Remote workers pose many compounding risks as well. They commonly operate using insecure Wi-Fi networks and may even use personal devices (BYOD) that are not adequately hardened. Sometimes, these devices are even shared with others in the household.
Today, organizations are routinely stretching tools like VPN and RDP far beyond their safe and proper use cases. For instance, VPNs should never be used on personal devices and they cannot provide the granular access controls necessary for privileged sessions—whether they be for employees or vendors. And misused RDP is now the top attack vector for ransomware. McAfee reported that there was a 50% increase in Internet-exposed RDP ports in Q1 2020, and a separate study found that 52% of all ransomware attacks In 2020 leveraged publicly accessible RDP servers to gain initial access! Ransomware attacks themselves were up 150% across 2020.
VPN and RDP have their place, but too often, they are being recklessly applied rather than matching the right technology for the right remote access use cases—and attackers are actively exploiting these gaps. All remote access sessions are some form of privileged remote access and require proper controls, visibility, and auditing.
2. There is now a heightened physical security threat. However, this pertains not to corporate office environments and server rooms, but rather to remote endpoints, many of which access and store sensitive data and routinely perform privileged activities. These devices—laptops, smartphones, tablets, and more—may be in households shared with roommates. These endpoints may be housed in high-theft areas. And some of these devices may be personal devices used for work (BYOD). This means that, in addition to being in a location that is largely lacking the physical security and surveillance controls found in corporate offices and server rooms, it's likely that the device itself lacks adequate hardening and other basic security protections.
Yes, the theft and BYOD risk of mobile (smartphone, laptop, etc.) has existed and been rising for more than a decade, but today the scale is many multiples higher. An attacker can now assume that it is likely an employee’s corporate device will be at their home. While some devices could be stolen simply as part of a run-of-the-mill burglary that seeks any valuable items, there is also the real potential for nation-states and other organized threat actors to target the homes of privileged users as part of cyberespionage. Simply put, where there exists a high-value target and corporate physical security is high and the cybersecurity controls are moderate to high, exploiting physical security deficiencies at a remote employee’s residence may be the path of least resistance, at least in the threat actor’s estimation.
Arguably, if you have physical access to a device, it is only a matter of time, tools, and persistence before most security controls can be circumvented. If an ill-bent insider has access to a laptop, or the device has been stolen from someone’s residence, there is nothing stopping them from disassembling the device and removing critical components, such as a hard drive, or perhaps even adding malicious hardware. It is unlikely you would see a worker disassembling their laptop in an office. However, if the employee is at home, there is no one walking by their workspace and no additional physical office security controls to prevent this type of physical device manipulation.
While I want us to focus on numbers 1 and 2 above in this blog, there is a third area we should at least briefly explore.
3. The longer-term trend is for physical security at corporate environments to become modestly less important than it historically has been. This estimation is due to the decrease of sensitive data that is housed on-premises as more workloads, computing instances, and data is hosted off-site via third-party cloud providers. With cloud servers in highly secure facilities, for most organizations, servers are physically protected better than ever before.
Of course, one interesting wrinkle that may undermine this entire premise in the near-term is the prevalence of masks in today’s offices. Mask-wearing may persist for a prolonged time as the specter of coronavirus continues to haunt us. With many office workers wearing masks, it potentially creates cover for a threat actor to infiltrate an environment and perpetrate their nefarious activities, all while evading any visual surveillance alarms, such as cameras or facial recognition solutions. In addition, because the concept of social distancing is freshly ingrained in the brains and psyches of workers, they will be more likely to keep their distance from others and be less likely to confront suspicious activity than they might have been in the pre-COVID-19 past.
Top Steps to Recalibrate Endpoint Security for the New Normal
So, now that we’ve covered how the security paradigm is shifting, what information governance changes are needed to protect data and digital assets going forward? We’re going to focus on addressing numbers 1 and 2 from the section above, which are really two different endpoint security domains.
- Cybersecurity for Endpoints
- Physical Security for Endpoints
1. Cybersecurity for Endpoints (Technologies and Settings)
- Harden endpoints: Remove unnecessary software, applications, and privileges, close unneeded ports, and ensure endpoints have the latest firmware and patches. Ideally, this is done before an endpoint is ever allowed access to your network, and hardening activities should continue to be performed as needed throughout the device lifecycle. This is especially important as devices may be returning to the office after being at home during coronavirus quarantine. Please note, for the purposes of this blog, we will lump in vulnerability management activities as part of endpoint hardening since it’s so fundamental to ensuring device health. One area I also want to call attention to here is the BIOS (Basic Input / Output System), which is the computer firmware used to boot a system after the device is turned on. BIOS manages data flow between the computer's operating system and attached devices. BIOS settings can be altered to disable critical device security controls. Here are three security recommendations for securing the BIOS and leveraging the BIOS to better protect the device:
- Enable password protection for the BIOS and ensure the password is strong, complex, and most importantly, unique.
- Apply tamper protection. Note that this features is only available from certain vendors. Tamper protection is typically enabled in the BIOS and has a software component that is loaded onto the operating system. Tamper protection monitors the device for any evidence that the device case has been opened or physical components have been removed or changed. If the technology recognizes such tampering, the software alerts a management platform. While this is should be considered an essential technology for mobile devices used by remote workers, few organizations implement it. In the absence of tamper protection, consider running delta reports against hardware using your asset management systems to determine if any components have changed, or been removed or added. While this will not tell you if the case has been inappropriately opened, it will help determine if key components have been altered.
- Configure the Boot Device to only boot from the internal hard disk and not from any external media like a USB device. An external bootable device can be used to circumvent other security controls and even overwrite the operating system. Therefore, control how the device can boot up and remember to use a BIOS password to secure this setting. The BIOS password can be managed by an enterprise password manager.
- Secure remote access: Access to sensitive resources, control planes (cloud, virtualization, DevOps) or to perform privileged activities should be locked down and tightly monitored. VPNs and RDP are wholly inadequate for such use cases and jeopardize your environment. At a minimum, organizations need the ability to extend privileged access management (PAM) best practices beyond the perimeter to enforce least privilege for privileged access by employees, vendors, and help desk personnel and monitor, manage, and audit that access via screen recording, keystroke logging, and other technologies. For these sensitive remote access use cases, look for a solution that only requires outbound remote connectivity. And keep in mind, threats like ransomware can even compromise hypervisors, reinforcing the need to secure all remote access to any resource.
- Manage credentials: Credential theft continues to be a key element in most breaches. As much as possible, organizations must automate and centralize, the lifecycles for human and machine credentials, keys, and secrets. Password management solutions should consistently enforce password policy, such as complexity, uniqueness, etc. Privileged password management solutions, part of PAM platforms, should also provide additional capabilities for managing sensitive machine and human credentials. Such capabilities include password rotation or implementing one-time-passwords or dynamic secrets. Privileged password management solutions should also enforce just-in-time access to help eliminate standing privileged access. These solutions can also further obfuscate, and hence protect, credentials by injecting them directly into sessions—never revealing them to the end user—whether employee, vendor, or machine.
- Enforce least privilege: Removing local admin rights and granularly controlling privileges for all human and machine identities is one of the most powerful ways to prevent malware infection, protect against internal and external threat actors, and should any compromise occur, mitigate damage from a security incident. Endpoint Privilege Management (EPM) solutions, part of PAM platforms, can enforce least privilege across all endpoints (Windows, Mac, Unix, Linux, etc.) and protect against known and unknown (zero day) threats. The best of these solutions will also provide a variety of ways of implementing just-in-time access, giving access only for those finite moments it is needed, then revoking it immediately afterward to ensure the privileged threat window remains brief.
- Control applications: The typical organization has hundreds or thousands of different applications running across its networks and endpoints. Increasingly, many of these are SaaS applications that are responsible for driving the immense growth of shadow IT and its associated risks. Application control technologies can help organizations get visibility and control around these applications, ensuring only approved applications, and the allowed subfunctions within those applications, can run within the proper context. Often, application control is coupled with least privilege management within the leading Endpoint Privilege Management solutions. Such EPM solutions may also offer advanced protections that can even defend against fileless attacks / living off the land (LotL) threats, which have surged in the last year as part of advanced persistent threat (APT) campaigns in ransomware and other attacks (SolarWinds, etc.).
- Implement Disk Encryption, which is the best method to ensure that a threat actor cannot get access to sensitive data if the hard disk is removed. Even if the device is removed and mounted on an external rig, it still cannot be easily accessed since the encryption is typically paired with the original hardware. And, if the device is physically stolen, without a logon password, access is still denied. However, please take note that, for some devices, an administrator password or key is all that is needed to decrypt the disk and provide access.
- Leverage EMM (Enterprise Mobility Management) solutions for the remote configuration, monitoring, and automated response to a device operating in the field. These technologies have evolved from basic mobile device management (MDM) to include a full suite of capabilities for helping to ensure device health, providing visibility over status, and more. EMM can help IT manage a wide diversity of devices. EMM functionalities like geolocation and remote wipe can help organizations mitigate potential damage of a stolen or lost device. Consider expanding your EMM initiatives to assets within your distributed workforce so you can respond accordingly to physical threats. However, before leveraging GPS/geolocation services, you should first ensure your code of conduct and regional privacy laws permit this type of monitoring and surveillance.
- Protect against malware: While many of the above defenses provide strong protection against malware, there is still something to be said for having a dedicated anti-malware solution. Such a solution should, at minimum, protect against a huge breadth of known threats (by applying signatures), but may also incorporate machine learning and use neural pathway technologies to provide advanced threat protection.
Now that we’ve covered the top cybersecurity controls to emphasize in this ‘new normal’, let’s dig into #2 and look at the physical security controls to help address the device and data security of remote workforces.
2. Physical Security for Endpoints
- Distribute and require use of computer security cables to secure a device to a desk or table to prevent theft. Computer security cables consist of a cable, lock (combination or key), and a mounting clip that attaches to the asset to be protected using a standard size oval connector. Security cables are typically used in high-traffic areas or public locations, but also provide a legitimate layer of physical protection for home/remote offices. If the endpoint being used at an employee’s home has sensitive information, consider issuing security cables to the user to help prevent theft.
- Embedded hard disks: These are becoming more common to trim device costs and provide lightweight laptops and notebooks. This storage medium is not removable like a PCIe or SATA hard disk, but rather the microchips for SSD storage are physically soldered to the motherboard. This makes accessing the data externally very difficult and the storage medium itself non-removable. The downside is that this practice can make it more difficult to legitimately service a device or perform storage upgrades.
- Seal the device: The screws that hold a device together can range from Phillips to Torx. Some sizes are standard and some are proprietary. As trivial as this sounds, if the threat actor does not have the tools to open a device, the less likely they are to gain access. This is especially true if their access to the device occurs during a short window of time. And, if the screws are sealed with glue or a bonding agent, they cannot be easily removed and make the device nearly disposable, in case of a fault. This is true for any device that the user may need to use while working remotely—from a laptop to hardware-based VPN. If the internals of a device represent a risk, and the risk, fault, and cost model warrants, considering permanently sealing the device from any access.
As a matter of simplicity, consider this basic mapping of security controls from physical to remote access. It should help you understand the methodology to securing resources from both perspectives.
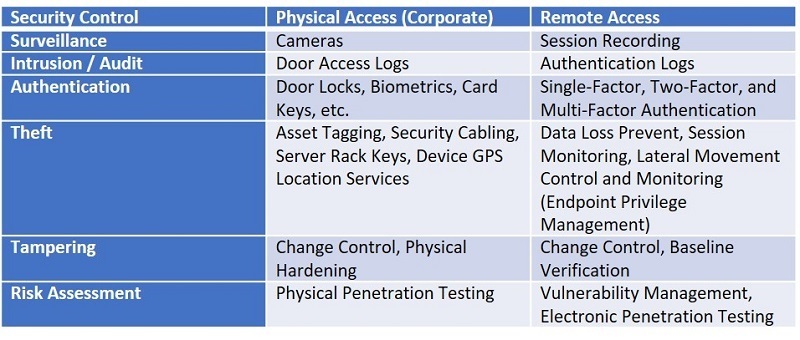
Recalibrating Enterprise Risk Management & Security for the New Normal
A distributed workforce forgoes much of the physical security provided within a corporate office environment. Information technology teams have no control over who can tamper with a device when it is out of the office. This was true for road warriors before COVID-19 and now we must learn from these policies and apply them to all users working remotely to support our new normal and a distributed workforce. This is on top of the cybersecurity controls we must strengthen or newly implement to address the different risks of users remotely operating and connecting.
If you embrace a proactive cyber risk management approach, you should be continuously asking - what is the threat actor’s path of least resistance and what can be done to prevent it from becoming an attack vector? Is it a new door lock or biometric system, or a secure remote access technology to assist with contractors, vendors, and remote employees accessing systems while out of the office?
Ultimately, you want a potential threat actor’s path of least resistance to be—another company/target. However, within your environment, you need to continue to reassess where your own paths of least resistance are, and the risk this poses to your organization. This assessment will help guide the judicious deployment of technologies or adjustment of settings and infrastructure in alignment with your risk appetite.
How can BeyondTrust Help?
BeyondTrust provides a complete Privileged Access Management platform that helps organizations nimbly address some of the most important areas of risk in this new normal. Our platform is comprised of the following three solutions—each one helps you gain security controls over your increasingly mobile and distributed environment while also reducing your attack surface.
Secure Remote Access: Enables organizations to apply least privilege and robust audit controls to all remote access required by employees, vendors, and service desks. Users can quickly and securely access any remote system, running any platform, located anywhere, and leverage the integrated password vault to discover, onboard, and manage privileged credentials. Gain absolute visibility and control over internal and external remote access, secure connectivity to managed assets, and create a complete, unimpeachable audit trail that simplifies your path to compliance.
Endpoint Privilege Management: Combines privilege management and application control to efficiently manage admin rights on Windows, Mac, Unix, Linux, and network devices, without hindering productivity. Elevate applications securely and flexibly via a powerful rules engine and comprehensive exception handling. Enforce least privilege and eliminate local admin rights with fine-grained control that scales to secure your expanding universe of privileges, while creating a frictionless user experience.
Privileged Password Management: Enables automated discovery and onboarding of all privileged accounts, secure access to privileged credentials and secrets, and auditing of all privileged activities. Security teams can instantly view any active privileged session, and, if required, pause or terminate it. Leverage threat analytics that aggregate user and asset data to baseline and track behavior and alert on critical risks. Video recording, keystroke indexing, full text search, and other capabilities make it easy to pinpoint data. Reduce the risk of compromised privileged credentials for both human and non-human accounts, while meeting compliance requirements.
You can deploy these solutions separately or together as part of our integrated platform, and benefit from cybersecurity and workforce productivity synergies that give your organization the security foundation to confidently embrace digital transformation and enable your work-from-anywhere workforce.
Contact BeyondTrust to learn more.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.










