The attack against Colonial Pipeline by the cyber-criminal gang DarkSide is the latest glaring example of just how vulnerable some critical systems and infrastructure are to attack. The attack has taken 45% of the fuel supplied to the U.S East Coast region completely offline since May 7th. Along the East Coast region, the public is experiencing long lines and fuel outages at many gas stations due to panic buying, with gas prices also running higher as a consequence. While public details of the actual attack chain remain scant, early speculation is that the attack may have started with a phishing attack, leading to widespread compromise of systems over weeks or months.
In a slightly unusual move, DarkSide actually apologized for the disruptions caused by the attack, saying “We are apolitical. We do not participate in geopolitics. Our goal is to make money and not creating problems for society. From today, we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
Of course, this apology doesn’t undo the damage or make the systems any more secure, and it’s certainly no legitimate justification for their past or future cybercrimes. This is not the first infrastructure attack executed by DarkSide. Earlier this year, the hacker group waged a ransomware attack on Copel, a Brazilian utility provider.
Diving into the DarkSide
BeyondTrust Labs has been tracking Darkside for months. Although DarkSide malware is not widely available, a few samples have appeared in various threat intelligence sharing platforms. The sample identified below is one of these and is the main ransomware payload that would typically be delivered after the group had widespread accesses to systems.
Darkside Ransomware v1.8.6.2
MD5: 9d418ecc0f3bf45029263b0944236884
SHA256: 151fbd6c299e734f7853497bd083abfa29f8c186a9db31dbe330ace2d35660d5
While the exact delivery mechanism is unclear, the sample is an unsigned binary that executes on the system. This means that application control should be one of the first lines of cyber defense—especially where critical systems are concerned. Application control can prevent unknown executables (that aren’t code signed by a trusted publisher) from running.
As with so many malware attacks, the DarkSide malware relies heavily on access to admin privileges and running in the context of an admin user. Once launched, one of the first things the malware does is call IsUserAnAdmin to check that the user it is running as an admin. Once it confirms the user is an admin, the malware will use a common UAC bypass technique (MITRE: T1548.002) exploiting ICMLuaUtil to silently escalate privileges by launching a copy of itself with a higher level of privilege on the system.
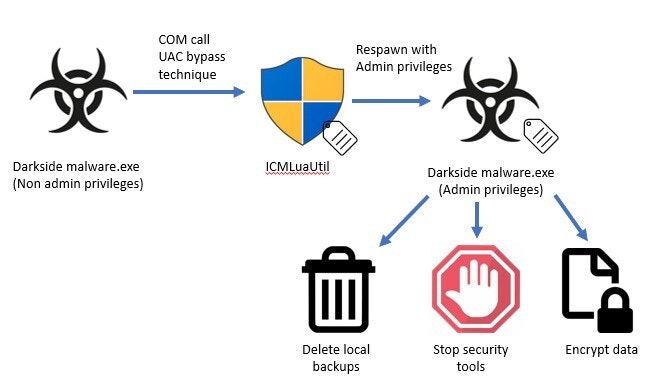
Once the malware is running with admin privileges, it starts to make changes to the system to prevent detection and recovery. It will use PowerShell scripts to delete local shadow copy backups of the file system to prevent the easy restoration of files and to inhibit system recovery (MITRE: T1490).
Within the malware, there is also a configured list of Services and Processes to kill (MITRE: T1489 & T1562.001). The malware leverages its new privileges to stop and delete any Windows Services in this list and calls TerminateProcess to kill off any unwanted processes. These “unwanted” process would typically be any AV, EDR, or security tooling running on the endpoint. This is a common tactic for malware to abuse privileges stolen from an admin user and to clear their attack path of defenses that may impede or detect the malware.
It’s worth pointing out that, with the DarkSide malware, disablement of security controls tends to be fairly limited compared to other malware. For instance, Trickbot malware (long used in ransomware attacks such as RYUK and others) will disable a wide range of group policy settings relating to Windows Defender as well as use a debugger key to disable AV and EDR Services.
With the groundwork set, the Darkside malware will begin to find files and folders to encrypt. In addition to encrypting local files, the malware can also target network shares. Once it has searched out all the possible local and network files it can access, encryption begins. While the encryption DarkSide applies is slower than that used by some other malware strains, it still manages to be quite effective.

Finally, the malware cleans up after itself by using CMD to delete the original payload that was dropped to disk and elevated, leaving behind encrypted files and a ransom note directing the victim to the DarkSide website on the dark web.
IT Security Mitigations for DarkSide Ransomware Attacks
Although this well-known example of malware shown above was submitted three months ago, some AV vendors are still unable to detect it as malicious. This is one of the key challenges with relying on reactive AV detection where attackers can vary and obfuscate code to evade detection.
In short, access and abuse of admin privileges sits at the heart of this threat actor’s modus operandi. Here’s how you can mitigate or prevent 4 different phases of the attack, and ultimately, withstand the attack altogether.
- An unsigned malware binary is allowed to run. Application Control could have been applied to easily prevent this.
- The DarkSide malware uses COM to perform a UAC bypass—this highlights the importance of Endpoint Privilege Management, which could have mitigated the attack by removing the user’s admin privileges.
- The unsigned malware binary is allowed to launch and elevate, leading to security tools being disabled, local backups deleted, and encryption of files. Application Control and Endpoint Privilege Management could have mitigated this by blocking execution and elevation of an unknown binary.
- PowerShell is launched with elevated privileges by the malware. Endpoint Privilege Management and Application Control could mitigate this by controlling execution and elevation at a granular level, for example preventing child process inheritance of privilege.
Again, if we look across the MITRE techniques used in this attack to elevate privileges, delete backups, and disable defenses, there is a common thread in that they all require Administrator or SYSTEM-level privileges. As such, the primary way to mitigates these techniques is removal of admin rights. When this is combined with granular application control, you can restrict an attacker’s ability to execute, persist, and elevate privileges, which are essential stages of the attack.
Today, the dual security controls of privilege elevation and delegation management (PEDM) and application control are found within the leading Endpoint Privilege Management solutions, such as BeyondTrust’s. Together, Endpoint Privilege Management, Secure Remote Access, and Privileged Password Management comprise a complete Privileged Access Management (PAM) approach
Attackers can always vary the tools and code they use in cyberattacks, but they cannot change the fact that they will need the code to execute and access privileges to succeed in total compromise. By taking a least privilege approach and controlling the execution and elevation of applications, rather than giving high-risk admin privileges to users by default, you can reduce your attack surface and mitigate the risk from most ransomware and other cyberattacks.
To learn more about how you can mitigate the Darkside attacks with BeyondTrust Endpoint Privilege Management, check out this demo I put together here.

James Maude, Field Chief Technology Officer
James Maude is the Field Chief Technology Officer (FCTO) at BeyondTrust. With his broad experience in security research, both in academia and industry, James has spent the past decade analyzing cyber threats to identify attack vectors and trends in the evolving security landscape. He is an active member of the security community and hosts Adventures of Alice and Bob, a podcast that shines a light on the people making a difference in security. As an expert voice on cybersecurity, he regularly presents at international events and hosts webinars to discuss threats and defense strategies.









