Dialling in just the right amount of privileged access continues to be a challenge for many organizations around the world. The pandemic-driven changes of remote working and accelerated digital transformation have only served to magnify this challenge, leaving companies at risk of cyberattacks if the privileged access gaps aren’t identified and addressed. As we know, hackers are creatures of opportunity, and no time will be wasted to capitalize on such weaknesses.
SolarWinds, the NHS, Virgin Media, and Colonial Pipeline – all these high-profile breaches involved privileged access pitfalls. Cybercriminals do not discriminate when it comes to industry or company size. So, how exactly do you avoid falling victim?
In this blog, which is accompanied by a free whitepaper, we share some landmines to avoid when it comes to maintaining secure, but productive, privileged access in your organization.
Peril #1: The Speed of Digital Transformation
According to a recent study by Nominet, 93% of organizations are currently engaged in a digital transformation project. Cloud adoption and BYOD (Bring Your Own Device) policies are becoming essential and expected for almost every business, especially with the massive shift to remote working. However, the promises of digital transformation projects can often tempt companies to roll out new technologies without prioritizing their security strategies.
We cannot stress enough how foundation cybersecurity practices, most notably Privileged Access Management, are to underpinning your digital transformation journey. IT ecosystems are expanding, perimeters are evolving or dissolving, and privileged access is proliferating—all of which are contributing to the expansion of the attack surface. An identity-centric approach that ensures users, sessions and passwords across your network are controlled effectively is critical to reducing security exposures and risk in this environment.
Peril #2: Cloud Proliferation
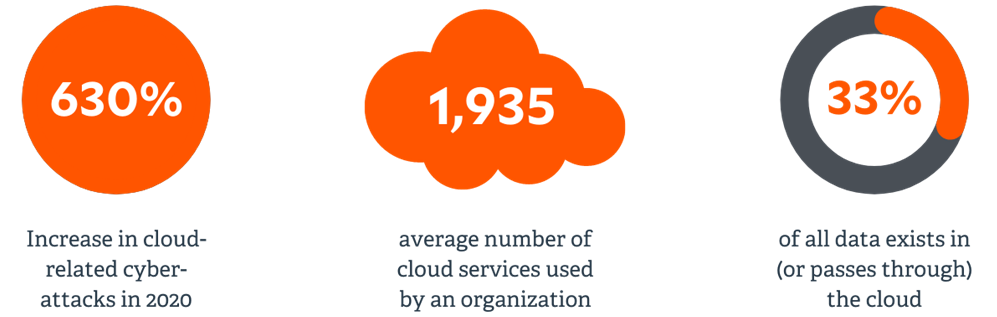
The days of organizations having ‘a’ cloud are long gone. With end users consuming dozens of different SaaS applications, multicloud environments continue to grow. And while this growth is enabling the success of remote working and digital transformation, it creates countless new attack vectors for hackers to explore.
In fact, last year, cloud-related cyber attacks were up a whopping 630% according to McAfee’s Cloud Adoption Risk Report. With most organizations now employing three or more public clouds, the risks are clear – but what should you do? Security practices that focus on cloud identities are vital to enforcing least privilege, managing cloud assets, and even securing your DevOps tools and CI/CD pipeline.
For more guidance on managing your cloud environments, you can download our free Guide to Multicloud Privilege Management.
Peril #3: Risky Password Practices
We’ve all been there when it comes to passwords, haven’t we? Trying to remember an obnoxiously long, case-sensitive combination of your third pet, first house, and meaningful numbers. Humans do not have the memories of elephants. For us, recalling multiple complex passwords for so many different systems is pretty much impossible.

According to a recent study by NordPass, the average person has around 100 passwords they need to remember. It’s overwhelming to say the least and is of little wonder that employees may store passwords insecurely or reuse them across multiple accounts. Instead of trying to overcome human nature, the solution is to solve their pain point. Insecure password storage and lack of rotation has been proven to lead to successful phishing attacks. A phishing attack relies on tricking a person into clicking a link or providing their credentials through convincing social engineering methods. But a user can’t compromise a password they don’t know, can they?
This is where the genius of credential injection steps in. A feature of leading remote access and password management solutions, credential injection enables users to simply select from a list of credentials to log in to the systems they are approved to access - eliminating the need to store and track shared credentials manually. Users are happy, and your organization is instantly more secure.
Wait There’s Much More…
You can discover even more detail on these three perils, plus FOUR more, exclusively in our new whitepaper. Download it now!

Jonathan Clarke, Content Marketing Manager
An experienced marketer, Jonathan has worked in numerous marketing functions over the last 10 years. From content writing, demand generation, graphic design, public relations and social media. Such roles have given him a unique holistic view of global marketing synergy, allowing him to execute with purpose, passion and efficiency. Jonathan also loves animals, and adores his three cats and German Shepherd, Simba.








