Last week was a busy one for the criminal hacking group Lapsus$, also known as DEV-0537. On Monday, Lapsus$ announced that it had gained access to a “super user” administrative account for identity as a service (IDaaS provider) Okta, via a third-party support engineer. On Thursday, seven purported members of Lapsus$—ages 16 to 21—were apprehended by City of London Police. An Oxford, England teenager is reported to be the mastermind of this group that has been rapidly gaining notoriety for their bold tactics. The cybercrime group has aclaimed to have successfully attacked a number of high-profile global enterprises.
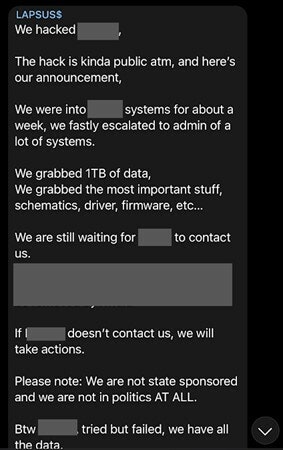
Read on for more BeyondTrust Labs insight on the Lapsus$ group, their modus operandi, and security practices you should implement to stay protected from Lapsus$-like attacks.
The Rapid Ascent of Lapsus$
In a world of criminal groups specializing in stealthy attacks and deploying ransomware, Lapsus$ has suddenly shaken up the landscape with a shock and awe campaign that revolved around extortion, destruction, and self-publicity.
The group quickly advanced from targeting smaller South American and UK businesses onto large global targets. From retail, media, and telco to government, healthcare, and technology, their targets are as varied as their tactics. Reports of Lapsus$ draining individuals’ cryptocurrency accounts sit alongside the public breaching and shaming of large companies.
While many have speculated about the motivations for the group, Lapsus$ stated in December 2021 the only goal is money:
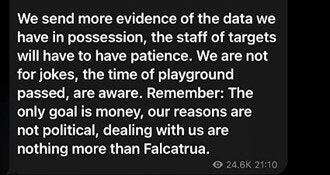
In an unusual move, the group operates a Telegram channel where they not only promote their exploits and dispute victim’s accounts of events, but also attempt to recruit insiders from organizations.

Their Telegram channel added 15 thousand followers over the last week, raising fears that the recruitment drive is working and more attacks are imminent.
Lapsus$ Tactics
The Lapsus$ group has appeared to be quite skilled at reconnaissance and social engineering. In the case of Okta, they targeted a third-party Technical Support Engineer who had privileged access to some Okta systems. In other instances, the cybercriminal group has succeeded in getting help desks to reset passwords and performed SIM swaps to bypass MFA. One of the group’s bolder tactics involves paying employees of large companies to run remote access tools or hand over credentials.
In some cases, they may target a user’s personal device first and deploy the Redline password stealer to gain access to corporate credentials used to login to email services. Once they have succeeded in compromising a user identity, they then pivot to access internet-facing systems. This would commonly be Remote Desktop Protocol (RDP) or Virtual Private Network (VPN) connections to gain direct access to the victim’s systems or network. To avoid triggering security alerts based on geo-location, the attackers will use NordVPN exit nodes in the same region in an attempt to fly under the radar.
Execution, Persistence, and Privilege Escalation
Once inside a system, Lapsus$ attacks will install (or get an insider to install) consumer-grade remote access software, such as AnyDesk to allow them to maintain access.

Looking at the screenshots the group published from the Okta breach, we can see they are using what appears to be a ThinScale remote access tool to access a thin client.
Once the attackers establish a foothold, they map out the users and groups within Active Directory to find other users or systems that could be used to gain higher levels of privilege. They will also explore communication channels, such as Slack, and internal wikis and collaboration platforms, such as SharePoint, to access information about the organization's structure and find additional credentials.
Tools such as Mimikatz are used for privilege escalation, with the goal of gaining domain admin access. In some cases, Lapsus$ attackers were able to access an organization’s cloud infrastructure and create privileged accounts, allowing them to lock legitimate users out of systems.
Exfiltration and Impact
Using VPN connections and/or attacker-created virtual machines joined to the network, Lapsus$ exfiltrates as much data as possible. Rather than encrypting data-at-rest, as many ransomware operators do, they will often begin deleting the compromised systems and resources.
In a truly unusual twist, the group uses their level of access to an organization’s systems to join and monitor incident response communications. By tapping into the victim’s monitoring, Lapsus$ can better understand the attack’s impact and, consequently, more effectively extort their victims.
Mitigating Controls against Lapsus$, and Lapsus$-like Attacks
While the tactics used by Lapsus$ are not completely unique, this group has seemed particularly adept at targeting and exploiting identities and access, so it's imperative to maintain a robust and continuous approach to protecting identities--particularly those identities with privileged access. Working together, the following controls provided a strong, blended approach to protecting against Lapsus& and similar threats, while also helping you enable a zero trust architecture.
- Discover and onboard all privileged identities. Having the ability to discover, manage, audit, and monitor privileged accounts and credentials—whether associated with humans, machines, employees, or vendors—means that you can take control before an attacker does. These controls can protect against account hijacking, privilege escalation, lateral movement, and other threat activities.
- Apply least privilege – across your entire environment. This encompasses everything from removal of local admin rights on desktops, to eliminating root on servers, and limiting and controlling entitlements in the cloud. A least privilege model vastly reduces the attack surface and opportunity for unwanted lateral movement and privilege escalation.
- Monitor MFA connections -- Understand where they originate from. Avoid using SMS-based methods vulnerable to SIM-jacking, and train users to report unsolicited prompts. Attackers will often flood users with MFA requests in the hope they approve one of them to stop the flood.
- Secure remote access – RDP and VPN connections often lack granular access controls and provide an easy point of entry for attackers with stolen credentials. They are also frequently the initial foothold in ransomware attacks. Using a secure remote access tool that can apply least privilege and audit sessions provides protection against abuse of stolen credentials, and prevents excessive access and lateral movement.
- Implement application control – If an attacker or malicious insider can easily install remote access and reconnaissance tools, then you will quickly find yourself breached. Many of the tools in the attacker’s arsenal are from legitimate companies, thus, they won’t get flagged by AV solutions. Implementing an application allow list with pragmatic exception handling can be a highly effective defense. When least privilege controls and application control are intelligently layered, as in leading Endpoint Privilege Management solutions, the risk-reducing impact can be synergistic.
- Unify management of cloud entitlements – With more of an organization’s workloads being hosted in the cloud across many different platforms, it is important to be able to discover and manage cloud entitlements to prevent privilege creep and consistently enforce least privilege in the cloud.
- Implement privileged password management – Ensure privileged accounts are properly secured and managed to protect against account hijacking, lateral movement, and other malicious activities. Enforce access policies and audit sessions for risky or unwanted activity. Having the ability to automatically rotate credentials for these accounts and audit privileged sessions limits an attacker’s ability to move laterally and elevate privileges. Moreover, the ability to automate password resets in response to change in context or threats helps minimize the window of time during which an attack could succeed vial a credential-based exploit.
Blended Protection from BeyondTrust
While Lapsus$ has grabbed the headlines with a string of high-profile attacks, there hasn’t been any evidence so far of zero-day exploits or new attack techniques. The group routinely exploits identities with access to privileges by using social engineering techniques or financial incentives to insiders. These attacks reinforce the need to secure privileges and manages access across the board, from on-premise assets to cloud workloads.
BeyondTrust provides blended protection that helps break attack chains, such as used by Lapsus$, at many different points. Our intelligent identity and access security platform combines comprehensive privileged access management (PAM) capabilities with cloud infrastructure entitlements management (CIEM) capabilities. Beyondtrust protection extends across your enterprise—from on-premise to the cloud—from humans to machine identities, and for employees, service desks, and vendors.
With the BeyondTrust solution you can:
- Extend privileged access security best practices beyond the perimeter to vendor and remote access as well. This includes managing and vaulting credentials, enforcing least privilege, and monitoring and managing every privileged session. This means you can pinpoint, pause and/or terminate suspicious activity in real-time.
- Replace or improve security around common remote access technologies such as RDP and VPN, ensuring all connections are outbound only.
- Combine least privilege and application control to restrict access to authorized users, applications, processes to perform only the proper activities within right context. BeyondTrust only elevates access/rights for the application, never for the end user, and access is only provide just-in-time to perform the authorized activity and then immediately deprovisioned. Importantly, application control also can prevent unwanted software (such as consumer-grade or unapproved remote access tools and other applications, from being installed).
- Protect and alert against fileless / living-off-the-land threats, with advanced context awareness
- Protect cloud tenants from inappropriate access by identifying all privileges and orchestrating the right-sizing of them across multicloud infrastructure.
If you want to learn more about how to take control of privileges before attackers do, contact BeyondTrust.

James Maude, Field Chief Technology Officer
James Maude is the Field Chief Technology Officer (FCTO) at BeyondTrust. With his broad experience in security research, both in academia and industry, James has spent the past decade analyzing cyber threats to identify attack vectors and trends in the evolving security landscape. He is an active member of the security community and hosts Adventures of Alice and Bob, a podcast that shines a light on the people making a difference in security. As an expert voice on cybersecurity, he regularly presents at international events and hosts webinars to discuss threats and defense strategies.










