Despite so many organizations landing in a hybrid directory environment just by the act of deploying Office365 (which requires Azure Active Directory), surprisingly little attention has been paid to how one would audit that environment and ensure Active Directory security. In this blog, I’ll explore the issue, but if you’re craving more of a deep dive, I recommend checking out my on-demand webinar: Mastering Hybrid Active Directory Auditing.
A Hybrid World
Almost all businesses today are working in what we’d call a “hybrid IT” environment. These hybrid environments are comprised of at least some cloud-based systems, some on-premises infrastructure, and oh-so-surely do the twain meet in many a documented or undocumented interconnect or integration.
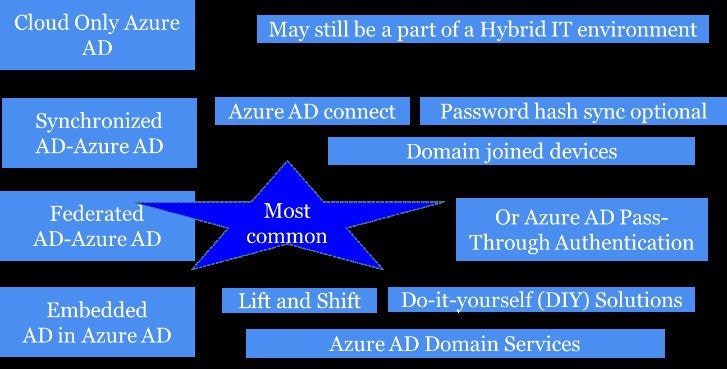
It’s the same way with hybrid Active Directory. Take a look at Figure 1 below where even the cloud-only Azure AD installation may still be part of a hybrid environment. All sorts of hybrid scenarios are emerging, including do-it-yourself (DIY) deployment of domain controllers sitting in an Azure (or Amazon Web Services (AWS)) virtual machine with a trust and a VPN tunnel to someone’s AD forest.
A Hybrid Kill Chain
What’s the risk? Hybrid AD topologies are just as much in the cyber kill chain as AD alone was when I wrote Active Directory Security Risk Factors and What to Do About Them (Part 1). Just by doing their job of listing information and answering queries, directory services become key information resources for hackers as well as cyber-defenders.
Imagine having a Google-like search tool that would automate the process of using legitimate directory queries to discover the paths of privilege through AD to the “crown jewel” IT assets. It exists. Tools such as PowerSploit and Bloodhound make it easy for an ethical hacker to find and close down weaknesses in access control – or for threat actors (using compromised accounts) to plan further steps in their cyberattack.
Figure 2 below illustrates some hybrid AD attack scenarios. The bad news is that cloud environments such as Office 365 / Azure are more vulnerable to brute force attacks since the login prompts are exposed to the Internet. Once an Azure AD account is compromised, an Office 365 user’s domain-joined machine could immediately put the on-premise AD environment at risk as well. From there, the figure shows how the rot could spread into AD, and back to Azure AD again, provided the attacker had some skills and exploit tools to work with.

The good news is that, up until this point, tools like Bloodhound and PowerSploit for Azure AD may be hard to find. But we must assume they, or something similar, could become available. Perhaps they would need to operate in a “low and slow” mode to fly under the radar of Microsoft’s security analytics, as well as master the enumeration and attack techniques unique to Azure AD.
The Big Gotcha – Revisited
More good news for hybrid AD defenders: As a managed service, securing Azure AD from attacks is easier than for AD. Many AD controls – like reducing the number of domain controllers (DCs) and deploying physical DC security, DC security baselines, and firewalls for DCs – are unnecessary for Azure AD. And once customers have multi-factor authentication (MFA) and Microsoft E5 subscription level security analytics, they can stop worrying about the brute force attacks so much.
However, as I wrote previously: “Many preventative controls are subject to The Big Gotcha: DAs create the rules in AD and can change them. A malicious or policy-violating DA insider, or an attacker with DA privileges, can override most of the preventative controls.”
Even in the Azure AD environment, customers must still protect against an attacker capturing an account with a privileged role in Azure AD, such as the Global Administrator (GA) Role. If that happens, all bets are off.
Deploy Procedural Controls
Just as in the AD environment, procedural controls to protect against mis-assignment or abuse of the privileged administrator roles in Azure AD are critical. Procedural controls should ensure that any change to these roles only occurs through well-established approvals that your monitoring / auditing solution can check for.
It is the combination of procedural controls to stabilize the directory environment, audit to check that controls are working, and a response or rollback capability that gives defenders a second chance. Audit and a second chance are just as important in the hybrid environment as they are in Active Directory itself.
For a deeper dive on this subject, check out my on-demand webinar, Mastering Hybrid Active Directory Auditing.
Additional AD Security & Auditing Resources
Active Directory Audit and Response: Giving Cyber Defenders a Second Chance (blog)
Active Directory Security Explained & 7 Best Practices (blog)
Real-Time Auditing and Recovery for Windows Environments (solutions page)
Active Directory Audit: Why and How (on-demand webinar)

Dan Blum, Cybersecurity Strategist and Author
Dan Blum is an internationally recognized strategist in cybersecurity and risk management. He was a Golden Quill Award winning VP and Distinguished Analyst at Gartner, Inc., has served as the security leader for several startups and consulting companies, and has advised 100s of large corporations, universities and government organizations. He consults with clients on identity management, PAM, risk management, and other topics. He's made his new book Rational Cybersecurity for Business: The Security Leaders' Guide to Business Alignment freely available for Open Access via Apress, or on Amazon.








