Privilege management and audit are complementary capabilities for Active Directory (AD) security. In a recent webinar for BeyondTrust, I explained how cyberattackers leverage AD for recon to discover configuration or privilege vulnerabilities that enable lateral movement toward the ultimate target. I also discussed incidents where AD itself was compromised by ransomware, virtually bringing an entire enterprise to a halt.
And guess what? Most of these exploits involve exploiting privileged accounts. Fortunately, defenders can deploy AD privileged access management (PAM) and audit as a powerful one-two punch to reduce an organization’s attack surface and stop cyberattackers in their tracks.
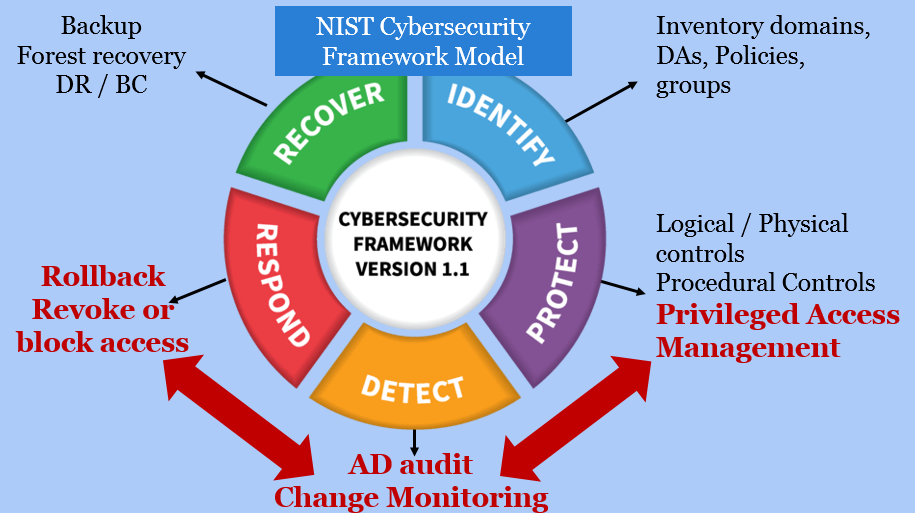
Controls
The NIST Cybersecurity Framework for AD graphic above depicts controls defenders should place around AD at a high level. “Protect” controls – such as multi-factor authentication for domain administrators (DAs), host-based firewalls for domain controllers (DCs), and DC configuration baselines – form the foundation for defense. “Detect controls” like Active Directory audit help enterprises can give the defense team a second chance even in the face of compromised privileged accounts.
Today, savvy customers are building the following controls trifecta:
- Protect: Privileged access management and procedural controls to tighten configuration of systems AND privilege
- Detect: AD audit and change monitoring to pick up on any violation of procedural controls, such as the unauthorized creation of new DAs, or other privileged accounts.
- Respond: Roll back the unauthorized change immediately upon detection.
Use Privileged Access Management (PAM) to Reduce Attack Surface
Privileged accounts are required to manage AD. They can be abused (or hacked into) to take advantage of configuration vulnerabilities present in many organizations’ deployments. Traditionally, customers’ DAs and privileged users have used the same account for both routine office work (think email, web surfing) and for AD administration. Too many privileged accounts are exposed in this way, and the privileges these accounts have are always-on, even when not in use.
No wonder PAM systems from BeyondTrust and others have been around for years to fill gaps in protecting privileged accounts, Unix/Linux root accounts, and other privileged OS accounts. The typical product provides a Credential Vault from which superusers must check out the privileged account username and password before beginning their admin session. “Just in time PAM,” or “JIT PAM” products, such as provided by BeyondTrust can also control privileges at a granular level, through privilege elevation features.
Procedural Controls Should Stipulate Use of PAM Capabilities
Whichever PAM product (or combination of products) you’re using, procedural controls are required. These controls must ensure that all DA or privileged access goes through the PAM product checkout or privilege elevation workflow.
Without procedural controls in an IT environment - such as a Windows forest - anything goes and customers cannot look at an anomalous log entry and tell whether it is a cyberattack or a legitimate (though perhaps misguided) IT activity that may be critical to the business.
Use AD Audit to Close the Loop
A malicious or policy-violating DA insider, or an attacker with DA privileges, can generally find a way to evade PAM controls. It is necessary to put PAM controls and procedural controls in place, but it is not sufficient.
Active Directory defense must include continuously monitoring AD for policy-violating changes by privileged users. Unfortunately, monitoring AD using AD-native tools alone is painful, involving many configuration settings and screens. Defenders should consider third-party tools to handle a lot of the grunt work involved in configuring, collecting, enriching, and alerting on AD events.
Some AD audit tools are configurable to generate alerts based on the occurrence of specific change events, such as the addition of a new just enough administration (JEA) privilege elevation script, or a new DA to the Domain Administrators group. Provided procedural controls are tight, the AD management suite can be relied to roll back the change without impacting legitimate business activity – just as shown in the figure at the beginning of this article.
Next Steps
AD audit is more important than ever, and AD privileges are in the cross-hairs. Use audit to identify issues (such as inactive accounts), monitor the operation of controls, and to detect malicious actions or policy violations against the directory.
For a deeper dive on this subject, check out my on-demand webinar: How to Audit Active Directory to Reduce IT Security Risks from Privileged Users.
Related Resources
Effectively Administer Windows without Domain Admin Privileges
Hybrid Active Directory Auditing: Same AD Security Challenges, Different Landscape

Dan Blum, Cybersecurity Strategist and Author
Dan Blum is an internationally recognized strategist in cybersecurity and risk management. He was a Golden Quill Award winning VP and Distinguished Analyst at Gartner, Inc., has served as the security leader for several startups and consulting companies, and has advised 100s of large corporations, universities and government organizations. He consults with clients on identity management, PAM, risk management, and other topics. He's made his new book Rational Cybersecurity for Business: The Security Leaders' Guide to Business Alignment freely available for Open Access via Apress, or on Amazon.








