One of the most critical threats to your organization’s security posture might come from a source that you’re overlooking: burnout among cybersecurity teams. You probably spend a lot of time protecting your estate against external threats, like malware attacks or phishing attempts, but how often do you look at how overextended your own internal security team is as a source of security risk? In 2023, cybersecurity teams are almost universally understaffed and overworked. NIST states that a shortage of 3.4 million cybersecurity professionals exists globally, and Forrester has cited that 66% of cybersecurity team members have significant levels of stress at work.
The World Health Organization (WHO) describes burnout as “a syndrome” that results from “chronic workplace stress that has not been successfully managed.” Symptoms for your team member include exhaustion and mental distancing. For the organization, this means reduced efficacy. When your security team members are overstretched, overstressed, and burnt out, mistakes happen—and these mistakes can result in breaches. Any member of an organization is susceptible to burnout, but for security teams who are regularly “under fire and under pressure,” burnout is becoming an increasing concern. That’s why it’s critical that you invest in security solutions that protect your organization while reducing operational complexity for your security team.
In this edition of our privileged access management (PAM) innovation series, we explore our latest releases – Privilege Management for Windows and Mac 23.6 and 23.7 – to demonstrate how our newest features and enhancements are helping to prevent cybersecurity burnout in security teams, along with its security risks for the organization.
How Privilege Management for Windows and Mac 23.6 & 23.7 can help prevent cybersecurity burnout
BeyondTrust is constantly innovating Privilege Management for Windows and Mac to deliver our customers market-leading protection for their estates with streamlined operations that reduce complexity for security teams. To ensure we are offering the highest level of protection, we are always listening to our customers, following the latest threat trends, and working to incorporate the features and capabilities that can help our customers the most.
BeyondTrust is pleased to announce the availability of Privilege Management for Windows and Mac releases 23.6 and 23.7. Our sixth and seventh releases of 2023 include new features and enhancements that streamline operations for security teams and provide straightforward access to actionable user behavior data, all in the name of making security implementation and management more streamlined to eliminate cybersecurity burnout and security team fatigue.
Read on to learn how our new features—like the application details view in Analytics v2, which gives you visibility into how a certain application is being used in your estate—are helping our customers by introducing effective security without overworking their security teams. You can also follow these links to see the full release notes for versions 23.6 and 23.7.
Automated Computer Archiving (New Feature)
Managing an estate of computers can be messy. You often end up with old or unused computers that are disconnected from Privilege Management for Windows and Mac but are still clogging up your Computers list in the Privilege Management Console. Historically, you could only remove one of those computers by manually deactivating it, severing its connection with Privilege Management for Windows and Mac. If you happened to need to reconnect it again, you would need to do so manually. In the fast-paced, constantly changing environment of many IT and security teams, these manual processes can consume too much valuable time.
That’s why, in release 23.7, we’ve introduced automated computer archiving. You can now automatically move computers to an archived state based on configurable rules, including but not limited to:
- How long a computer has been disconnected from Privilege Management for Windows and Mac
- Which computer group it’s a part of
- The operating system that its running
- Whether it has a duplicate hostname.
From the archived state, computers can then be deleted or moved back into the active pool, either manually or automatically based on configurable preferences. Archive and deletion rules can be created and managed through the new Management Rules module, accessible via the new lightbulb icon in the left panel of the Privilege Management Console. Automated computer archiving gives you the tools to reduce complexity in the day-to-day management of your estate, allowing your security teams to focus on the computers that matter without being overburdened by disconnected computers.
Analytics v2 Updates (New Feature)
At the end of 2022, we introduced Analytics v2, an upgraded version of the analytics and reporting functionality in Privilege Management for Windows and Mac. Built on next-generation technology, Analytics v2 surfaces deep insights from your user behavior data and turns them into actionable policy refinements to help you protect your estate.
Since that initial release, we’ve released five Privilege Management for Windows and Mac releases in 2023 alone, and in each of those releases, we’ve introduced new features and enhancements to expand the capabilities of Analytics v2. Thanks to all of those new features and added functionalities, Analytics v2 now provides you with more intuitive insights about your users’ behavior, as well as a streamlined path to turn those insights into actionable policy updates that keep your organization protected without adding to your security team’s workload.
Our two latest releases are no different. Releases 23.6 and 23.7 have introduced four new enhancements to Analytics v2: additions to the application details view, the ability to identify local admin logons, and search functionality improvements. Let’s take a detailed look at each of these new enhancements to see how they can help prevent cybersecurity burnout by providing your security teams with both streamlined visibility into what’s happening in your estate and simplified workflows to execute necessary updates.
Application Details View
Over the last few releases, we’ve introduced the applications view in Analytics v2, a view that aggregates your user behavior data at the application level, giving you streamlined visibility of the applications your users are trying to install or run. Now, with release 23.6, you have access to the application details view. Where the applications view shows you an overview of all the applications being used in your organization, the application details view lets you dive deep into one of those applications. You’ll gain insight into how often an application is being run as well as the associated behavior at the end user level, such as how often that application was blocked, elevated, allowed, or cancelled over time, all through an easily digestible action line graph. You can also see which users are running the application, the reason given if one is required, and all associated events and metadata, including versions run, application type, and more.
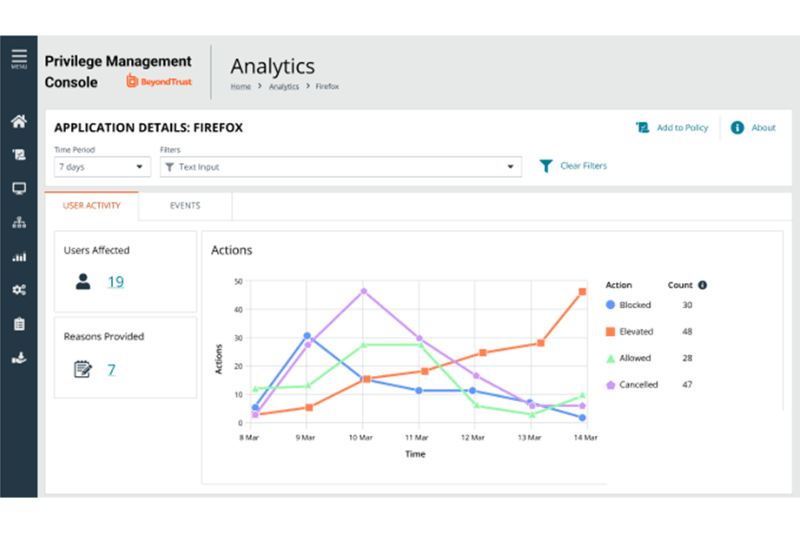
While an aggregated view of application usage data works in most scenarios, drilling down into the specific events associated with that application can sometimes be necessary. That’s why, in release 23.7, we introduced a new Events tab to the application details view. The new Events tab displays all of the events associated with the application that is being viewed, providing you with streamlined access to granular usage details on how the application is being used within your organization.

You can access the application details view by clicking any hyperlinked application name you see on the applications view page. The application details view allows you to see trend information about how a given application is being used in your estate as well as each of the events associated with it. Having simplified access to this information empowers your security team to quickly make an informed decision about whether or not to take action and/or update the policy, eliminating the stress from the equation.
Identify Local Admin Logons
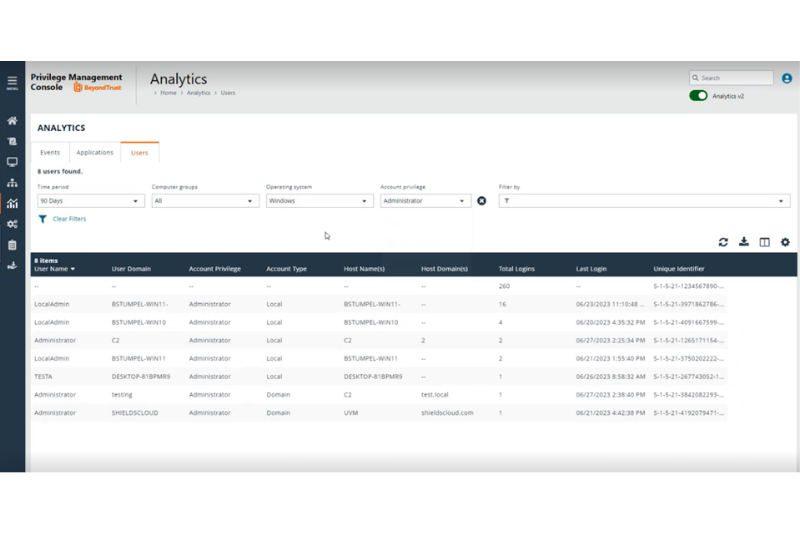
Analytics v2 now displays a new Users tab next to the existing Events and Applications tabs. The Users tab displays all user logons across your organization and includes detailed information on each one, such as:
- User name
- Account privilege
- Account type
- Host name
- Total number of logins
- Last login time, and more.
You can filter by account privilege for visibility into any logons with administrative privileges, enabling you to see where local admin rights still exist in your organization and take action to remove the need for them. This new visibility within Analytics v2 gives you the tools you need to achieve least privilege and keep your organization secure.
Search Functionality Improvements
Release 23.7 also brings enhancements to the search functionality in Analytics v2. Now, when you search for something via the search bar, you receive faster, more precise results, giving you more options to access the data you need quickly.
Windows Custom Tokens in the Web Policy Editor (Enhancement)
Historically, Privilege Management for Windows and Mac users have only been able to create Windows custom tokens in the Microsoft Management Console (MMC), not through the Web Policy Editor. With release 23.7, you can now use existing Windows custom tokens as templates. These templates can be configured to provide specific behavior, including integrity level, group membership, privileges, and process access rights, for a given application rule, on-demand application rule, or content rule through the Web Policy Editor. This enhancement provides Privilege Management for Windows and Mac users who utilize Windows custom tokens the ability to manage their policies solely from the Web Policy Editor. This eliminates a significant amount of administration time when it comes to updating policies and can significantly help reduce the burden on the security team.
New Parameters for macOS Messages (Enhancement)
Messages are a critical part of any successful Privilege Management for Windows and Mac deployment, serving as the primary end user interaction point with the solution. Well-crafted messages can preempt service desk tickets by providing end users with clear, actionable information. That’s why, in release 23.7, we’re introducing more parameters that can be used in messages on macOS endpoints. Added parameters include:
- [PG_PROG_NAME] - The program name of the application
- [PG_PROG_PATH] - The full path of the application file
- [PG_PROG_PROD_VERSION] - The product version of the application being run
- [PG_PROG_PUBLISHER] - The publisher of the application
- [PG_PROG_CMD_LINE] - The command line of the application being run
These new parameters make it easier to customize your end user messages, allowing you to communicate more clearly with your end users, adapt dynamically to more scenarios, and ultimately reduce the number of service desk tickets your IT teams will need to resolve.
Next steps: Start streamlining your security operations without overworking your security team
If you are ready to learn more about the best solution for achieving and dynamically enforcing proven endpoint security policies, like least privilege, without overburdening your security teams or contributing to cybersecurity, contact us today! Or, if you are already a BeyondTrust Privilege Management for Windows and Mac customer, here's how to get started with 23.6 and 23.7.
Be sure to stay tuned to our PAM Innovation Series to keep up-to-date as we continue to make the feature updates and enhancements that matter most to our users!

Alex Bauer, Product Marketing Manager, BeyondTrust
Alex Bauer is a Product Marketing Manager at BeyondTrust, focusing on Privilege Management for Windows and Mac. Prior to joining BeyondTrust in 2022, he worked in a variety of product marketing roles at Dyson and B2B ecommerce software startups, planning and executing launch, messaging, and positioning strategies for products like robot vacuums and air purifiers. Alex brings a consumer lens to the BeyondTrust Marketing team, working to convey complex cybersecurity concepts and features in easy to understand ways.









