Over the past 18 months, organizations adapted to social distancing initiatives and other disruptions caused by the pandemic by "going remote" and by accelerating digital transformation initiatives. While remote work, BYOD, and WFH/WFA (work from home / anywhere) have been on the rise for years, the trend is considerably more pronounced now due to the pandemic. Rather than edge cases, these working modalities are now making up a significant share of the work landscape. The mobility of endpoints and identities is expected to continue to increase as hybrid workplaces take shape.
The technology adaptions and evolutions galvanized by the pandemic are creating productivity improvements that should endure long into the future. However, this time period has also been characterized by increases in ransomware and phishing attacks and a high volume of breaches, including attacks that disrupted critical supply chains and imperiled lives. Of course, these trends are closely related as remote work and digital transformation developments have expanded the attack surface, while security maturity has not kept apace.
The IT security concepts of zero trust and identity-centric security have risen to prominence in response to the challenges of an increasingly distributed, mobile, and perimterless digital world. Most cyberattacks today revolve around identities, and the credentials and privileges of those identities. A new study sponsored by the Identity Defined Security Alliance (IDSA) validates that a shift to identity-centric security and zero trust is clearly underway, and that organizations have momentum in implementing identity-based security outcomes. The IDSA report, titled 2021 Trends in Securing Digital Identities, is based on a survey conducted by Dimensional Research of over 500 security and identity professionals across the United States who worked at companies with more than 1,000 employees.
Let’s explore some key findings from the IDSA study.
2021 Trends in Securing Digital Identities – Highlights & Analysis
Some of the survey questions in the new IDSA study were repeated from a study the previous year, allowing the capture of some shifts in sentiment and trends. One change in sentiment that stood out was that the confidence in the ability to secure employee identities dropped from almost half (49%) of respondents to less than one-third (32%) over the past year. Wary of increasing cyber threats, IT security professionals recognize that they have yet to adequately adapt security posture to the demands of the new normal.
Part of the identity security challenges has to do with managing the surge in digital identities. In the IDSA study, 83% reported that remote work due to COVID-19 increased the number of identities. Much of this increase is driven by the increase in privileged identities, including non-human identities. In the Q4 2020 Forrester Wave: Privileged Identity Management, Forrester Research stated: “Our clients tell us that machine identities are growing at twice the rate of human identities.” A 2020 Forrester Consulting and BeyondTrust study found that privileged identities, the most important identities to protect, are also growing as a consequence of a number of factors, but most commonly:
1. Having to treat more employees as privileged users due to remote access infrastructure
2. An increase in workloads requiring access to sensitive systems data, among other factors.
While confidence has dropped in the ability to secure identities, 80% of respondents in the IDSA study say their organization has increased their focus on identity security following the pandemic-induced shift to remote work. With that said, most companies still have a long journey ahead to implementing identity-related security outcomes, as shown the figure below.
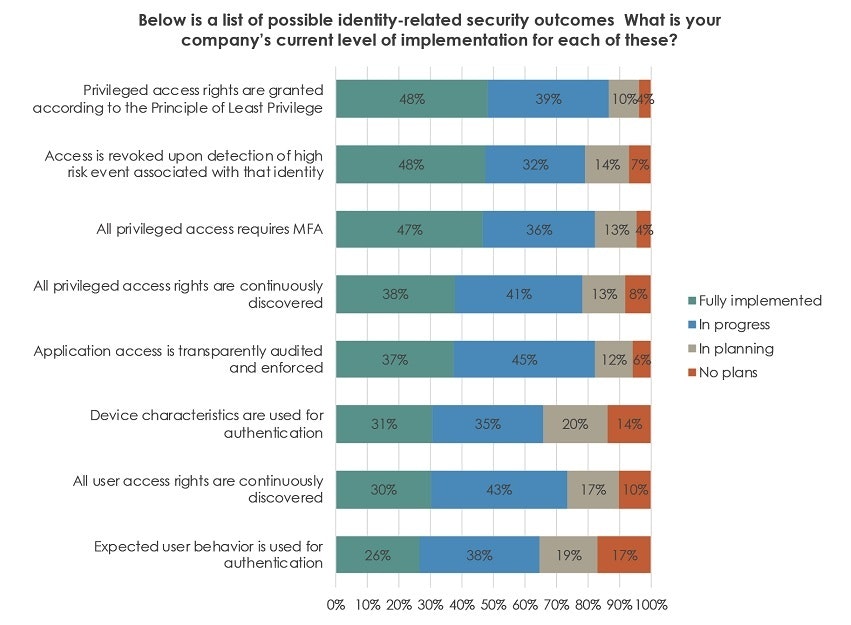
However, organizations are showing strong progress in implementing identity-related security outcomes. In the figure below, we can see the improvements going back three years, with a surge in activity in 2020, and continued momentum in 2021.

The Identity Defined Security Alliance (IDSA), of which BeyondTrust is a contributing member organization, developed a library of identity-based security approaches and outcomes, which can be found in detail on their site here.
Why is it important to drive towards these identity-related security outcomes? 93% of IDSA study participants who experienced a corporate breach say that better implementation of security outcomes could have prevented or minimized the breach.
The security outcome mostly frequently cited (50%) for its ability to have prevented a breach that occurred is timely reviews of privileged access. With privileged access a factor in most breaches—whether to execute a malware payload to gain an initial foothold, or to move laterally once within an environment, adequate control over privilege provisioning and de-provisioning is essential. Often, too much access is given by default, or the access is open-ended (standing privileges), when it should only be provisioned just-in-time when certain contextual parameters are met and then revoked when the task is completed or the context, the context has changed, or a certain amount of time has elapsed. Roles change or people leave the company, yet access and accounts frequently remain active, such as for cloud resources. By routinely re-examining access usage and roles, you can fine-tune provisioning to ensure the organization adheres to the principle of least privilege principle (PoLP). For instance, if an account with privileged access has been unused for a month, it’s possible it is no longer needed and can be removed, eliminating risk. Or, if the account is rarely used, and only for very highly privileged activities, it may make sense to incorporate additional workflows to grant usage for the account and to send alerts to others when the account is being used, so it receives closer surveillance.
Identity-defined, or identity-centric, security is clearly taking root. The evolution in mindset around identity has come along way. In the IDSA study, 90% of respondents agreed with the statement, “Identity management used to just be about access, now it is mostly about security."

Moreover, 93% of IT security pros in the study say zero trust is strategic to securing their organization and 97% agree identity is a foundational component of a zero trust security model.
Continuing Progress toward Identity-Defined Security and Zero Trust
The coronavirus pandemic altered the course of work, productivity, and security for the long term. Digital transformation initiatives promise tremendous upside, yet, organizations have their work cut out for them in closing the yawning security gaps created by the accelerated digital evolution over the past 18 months. However, it's promising to see that organizations are largely leaning into identity-defined security controls and zero trust principles to address the gaps in the expanding attack surface.
You can download and read the full 2021 Trends in Securing Digital Identities here. As part of Identiverse 2021, you can also tune into panelists from Intuit, Robert Half, Dimensional Research, and the IDSA as they discuss the report on Tuesday, June 22 from 8:30 – 9:20 a.m. MDT. For more information and to register, visit https://identiverse.com/idv2021/session/SES7EJAXRI3427G6L/.

Matt Miller, Director, Content Marketing & SEO
Matt Miller is Director, Content Marketing at BeyondTrust. Prior to BeyondTrust, he developed and executed marketing strategies on cybersecurity, cloud technologies, and data governance in roles at Accelerite (a business unit of Persistent Systems), WatchGuard Technologies, and Microsoft. Earlier in his career Matt held various roles in IR, marketing, and corporate communications in the biotech / biopharmaceutical industry. His experience and interests traverse cybersecurity, cloud / virtualization, IoT, economics, information governance, and risk management. He is also an avid homebrewer (working toward his Black Belt in beer) and writer.








