In light of the recent high-profile social media account breaches, organizations are strategizing how to protect their own social media accounts (Twitter, LinkedIn, Facebook, Instagram, Tik Tok, etc.). from the next breach. While it is a hard truth that little can be done to protect an organization when the SaaS vendor and its employees are breached, there are myriad security best practices that can be enacted to mitigate the risks of a privileged attack vector and inappropriate account access.
If you follow a universal privilege management model for privileged access management (PAM), your security controls for any type of social media account can layer on session monitoring, session recording, and geolocation monitoring of access to ensure any login attempts and successful logons are appropriate and most importantly, authorized.
Improving Internal Security Controls around Twitter
To effectively augment the native Twitter security controls, let’s first consider the role-based architecture already provided by the social media company. Twitter for Business multi-user login allows for an administrator to grant access to other users for your Twitter Ads account. This is a clear distinction from a traditional Twitter account due to the paid nature of creating and publishing advertisements based on campaigns. A Twitter Ads account includes capabilities for granular access to control Tweet and promotional content. While this helps a business manage advertising campaigns securely among multiple team members, it does not provide security controls that are generally associated with privileged access management best practices.
Twitter Role-based Access Controls (RBAC) for Business Accounts
At a high-level, here are the native role-based access controls for various Twitter for Business accounts:
Account Administrator: Users have full access to ads.twitter.com, including the ability to manage Administrator and Ad Manager Accounts, make changes to advertiser campaigns, and view performance data. It is important to note that Account Administrators do have access to personally identifiable information, including credit card and contact information for the business. This is obviously a highly valued account for a threat actor to target and must be properly safeguarded using a universal privilege management strategy that secures access across every user, session, and endpoint.
Ad Manager: These users can access ads.twitter.com, make changes to campaigns, and review performance data. Ad Managers cannot grant users access to the ads account or publish Tweets. This account represents a high-valued power user in the Twitter ecosystem. Thus, this account should have the same protections as an Administrator Account because, if it is compromised, a threat actor could publish an embarrassing campaign or delete existing content on behalf of the organization.
Creative Manager: Users can access ads.twitter.com to manage advertisements, but cannot manage campaigns. The risk posed by this account is on par with that of an Ad Manager, but also consider that the content could be published, deleted, or modified under an existing campaign, which would represent a liability to the organization.
Campaign Analyst: Users can access ads.twitter.com and only view performance data. They have no other role-based access to Twitter Business functions. Unless the performance data is sensitive in nature, this account is a low risk to the business.
Organic Analyst: User can access analytics.twitter.com and view analytics. They have no other access to paid campaigns. Unless the analytic data is sensitive or proprietary in nature, this account is a low risk to the business.
Partner Audience Manager: Users can manage Tailored Audiences through the Twitter API. Audience Partner Managers will be required to obtain authorization in order to update or deliver new audiences to an ads account. They have no other role-based access and the API should be protected from misuse through technology like a CASB.
Best Practices for Addressing Twitter Security Gaps around Access Controls
One important attribute regarding the Twitter RBAC model is that Account Administrators and Ad Managers do not have the capability to compose and publish Tweets by default. This permission must be assigned separately and cannot be assigned to either of the analyst roles.
While Twitter’s account model provides granularity for business users, it lacks the necessary best practices to enforce a strong security model. Therefore, to properly apply these settings, consider the following recommendations:
- Do not use personal accounts for Twitter for Business functions. Keep personal accounts used for tweeting and business advertising management separate to ensure an insider threat does not become a liability to the business and a personal attack does not lead to a business security incident.
- Create dedicated business accounts for each user assigned to each role and do not make every user an administrator, even though this may seem convenient. Follow the model of least privilege access and role-based delegation when assigning privileges.
- Ensure the password used for any of these accounts is unique and not shared with any other resources in the business, or by an individual for their personal accounts.
- Use native Twitter Two-Factor Authentication to secure each account to ensure compromised credentials alone do not result in a breached account.
- Review the Twitter access logs for authentication attempts and review successful logins from known sources to verify appropriate activity.
However, even with all of these important controls properly in place, organizations still cannot enforce security best practices for privileged access management. Fortunately, the problem has a simple solution and can actually be applied to other social media solutions and SaaS applications to increase an organization’s security posture for privileged accounts in the cloud.
While Twitter for Business does provide controls for role-based access and two factor authentication (2FA), it does not:
- Obfuscate credentials
- Allow for one-to-many account access without sharing credentials
- Enforce an IP-based access control list (ACL)
- Provide session monitoring or session recording
Twitter’s simple deficiencies in these areas runs contrary to privileged access management best practices. To implement these security controls for your Twitter accounts, consider using BeyondTrust’s Privileged Remote Access.
Privileged Remote Access lets you control access to critical systems on premise or in the cloud without hindering the work privileged users need to perform. The solution natively allows organizations to define how users connect, monitor sessions in real time, and record every session for a detailed audit trail to enforce regulatory and PAM best practices.
In addition, the solution eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault or you can leverage BeyondTrust’s Password Safe solution to automatically retrieve the current credentials for the desired account. The retrieved credential is never exposed to the end user, but rather is automatically injected into the session to obfuscate the account being accessed. Not only does this workflow give you more control over privileged accounts and credentials, the credential obfuscation feature further reduces risks from privileged attack vectors.
Finally, since all of this operates from a central location (an appliance), access logs should always show the same source for all successful login attempts. Any foreign addresses that are granted access are potential evidence of compromise.
From an architectural perspective, BeyondTrust’s Privileged Remote Access solution can be deployed in the cloud as a SaaS or on premise (DMZ or on an internal network) as an appliance to broker the connection to Twitter. A Jump Point is installed utilizing a feature called a Web Jump Client to render the Twitter website as a service and auto-inject credentials based on storage in either Cloud Vault, Password Safe, or manual entry. This is illustrated in diagram below.
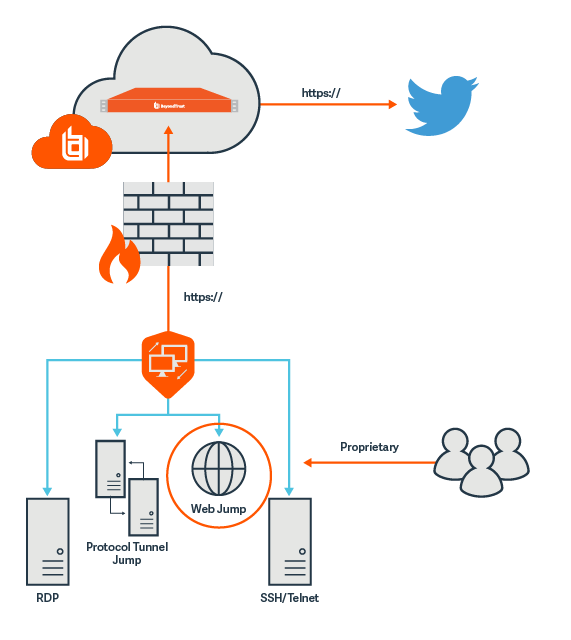
The result?—The end user experience is characterized by faster and more secure access to Twitter. The end user is not actually not connected to Twitter, but rather a rendering of the web page itself is displayed. In addition, all access is gated, session recorded, and session monitored by the Privileged Remote Access appliance to ensure all activity is appropriate. Any connection attempts identified in the Twitter logs outside of the appliance are considered as suspicious.
This implementation solves the four primary challenges with the Twitter for Business role-based access model:
- Obfuscated credentials are auto-injected into the session by the solution and never exposed to the end user
- Allows for one-to-many account access, without sharing credentials, by mapping multiple users to the same account and logging access by identity
- Enforces an IP-based access control list model by ensuring all legitimate access always originates from the same source; the BeyondTrust Privileged Remote Access appliance.
- Provides session monitoring and recording with extensive playback capabilities for training, regulatory compliance, and to prove a session was appropriate or inappropriate based on a user’s behavior.
Learn more about BeyondTrust Privileged Remote Access

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.










