Why You Should Implement OT Cybersecurity Best Practices
Operational technology (OT) refers to the software and hardware used for managing, monitoring, and controlling physical equipment. OT encompasses supervisory control and data acquisition (SCADA), industrial control systems (ICS), distributed control systems (DCS), and more. Emergency services, water treatment plants, traffic management, and other critical infrastructure rely on operational technology solutions to properly function. When connected to the internet, as these systems increasingly are, they become part of the cyber-physical world.
Cyberattacks on critical OT infrastructure have been on a steep upward trajectory. According to a new Fortinet report, 75% of those responsible for OT security say their organization had at least one OT system intrusion incident in the last 12 months, while 32% incurred a ransomware attack. And 32% of these cyberattacks impacted both OT and IT systems.
A breach of OT and cyber-physical systems may result in catastrophic consequences, even loss of human life. In recent years, OT attack targets have ranged from nuclear plants to water treatment facilities. Several years back, a poisoning attack at a Florida water treatment facility was particularly scary because of how easily an attacker gained sensitive access via inadequate password management. The attacker leveraged unsophisticated actions via a consumer-grade remote access tool within the environment to order the system to increase the amount of lye in the water to dangerous levels.
Why Cyber Risk to OT Systems is Increasing
For many years, industrial systems relied upon proprietary protocols and software, were manually managed and monitored by humans, and were not directly connected to the public Internet. In those days, the only way to infiltrate OT systems was to obtain physical access to a terminal—and this was no easy task. OT and IT (Information Technology) integrated little and did not share the same vulnerabilities.
Today, it's a starkly different story. The convergence of IT and OT is accelerating as part of digital transformation initiatives. We see more industrial systems brought online to deliver big data and smart analytics, as well as to adopt new capabilities and efficiencies, through technological integrations. This transition from closed to open systems creates a slew of new security risks. These are being actively targeted—often with success—by threat actors and need to be addressed.
In addition, many parts of OT infrastructure are comprised of specialized equipment and software that may not be engineered with much focus on withstanding cyberattacks. Non-traditional endpoints, such as internet of things (IoT) and industrial IoT may proliferate in OT environments. Such endpoints may even lack a viable operating system or the computing power to run security software, such as A/V and anti-malware.
As industrial systems become more connected, they become more exposed to vulnerabilities. Add legacy equipment, safety regulations to prohibit any modifications being made to equipment, and compliance regulations requiring sensitive data to be made available to third parties. This makes achieving the dual goal of operational uptime and IT security quite a challenge.
Additionally, remote vendors, employees (operators), suppliers, and other contractors often remotely access OT systems to perform legitimate maintenance and other actions. Remote vendors and employees complicate the situation even more by bringing in a BYOD / BYOT mindset, as well as by working from insufficiently hardened home networks. These remote connections further blur the IT-OT segmentation and expanded the attack surface of the cyber-physical world, providing new entry points for hackers to exploit.
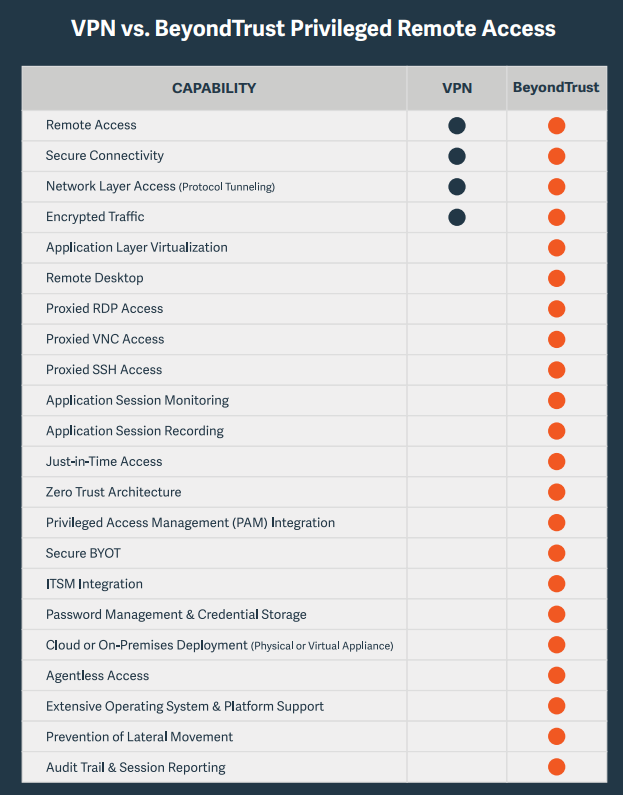
Organizations commonly use VPNs for privileged remote worker or vendor access, but VPNs lack granular access controls and cannot perform session monitoring or management, so this is a risky, and inappropriate VPN use case. While VPNs can provide a secure tunnel from one location to another, the access permitted by a VPN is unrestricted—which is dangerous for any sensitive environment, let alone OT systems.
Privileged users—whether employee or vendor—pose the most risk as an attacker can ride on whatever privileges the worker has to execute lateral movement from the IT network to the OT and ICS system on the production floor. Once in the ICS network, hackers can potentially monitor and manipulate operational components. Such alterations can cause dangerous conditions to the environment, jeopardize the safety of plant personnel or the community, and potentially cause monetary loss due to shut down or a disruption in production.
4 OT Security Best Practices
How can organizations implement OT cybersecurity best practices to address a large volume of operators, contractors, and vendors connecting remotely into their network? This needs to be accomplished without the use of a VPN and without compromising processes, operations continuity, or inhibiting business agility or productivity.
At minimum, you need to always know who (identity) is doing what on your network, from what device, and when. OT security should entail complete, granular control over access —whether it is for an employee or vendor, and whether they are on site, or connecting remotely.
Here are four best practices for protecting Operation Technology environments from cyberthreats:
#1 Implement a Zero Trust Framework
Securing any network begins with understanding every connected user and device and every bit of data they are trying to access. This is a basic premise of any security framework—including zero trust. To embrace zero trust across your OT network, implement the following security controls:
- Apply network segmentation: Provide application access independent of network access. This entails enabling contractors and vendors to access only the applications and systems they need—without requiring complex firewall configurations or VPNs.
- Provide application-level micro-segmentation to prevent users from discovering applications they are not authorized to access. In addition to protecting against malicious insiders or external threat actors, this step also helps protect the environment against human errors—one of the leading cause of breaches and system downtime.
- Establish a centralized point of visibility and accessibility for different systems requires various connectivity methodologies. As more integrations between OT systems and IT systems drive automation, efficiency, and lower costs, keeping these systems known and available on the internet only for authorized users eliminates the biggest attack surface.
- Monitor and record all activities performed over remote access via on-screen video recording. Session monitoring is essential both for security and for compliance.
- Exert granular control over the sessions by enforcing least privilege and restricting commands that can be executed by identity/user.
- Implement API Security - Protecting APIs is essential to safeguard the integrity of data communicated between IoT devices and back-end systems. Only authorized devices, developers, and apps should be permitted to communicate with specific APIs.
#2 Align the Right Remote Access Tools with the Right Use Cases
As digital transformation continues its sweep across all facets of technology, industrial systems and plant operators are less likely to be hands-on operating OT systems directly on site. While VPNs and RDP are often a go-to technology for remote access, they are often an inadequate match for OT and zero trust environments.
In particular, eliminate use of VPNs and RDP from usage in those instances involving privileged access and third-party access.
While adequate for providing basic remote employee access to non-sensitive systems (i.e., email etc.), VPNs lack the granular access controls, visibility, scalability, and cost-effectiveness demanded of third-party and remote worker access to OT/IoT devices. VPNs cannot enforce the granular least privilege access or monitoring / management over sessions imperative for security and oversight of privileged user access.
#3 Understanding IT Security Versus OT Security
In most organizations, the policies and service agreements to manage IT systems do not extend to the operational technology environment, creating a security and management gap. Managing security and risk in OT environments isn’t as simple as porting over IT security best practices into the OT system. Relying on consumer-grade remote access / support and other such IT solutions is certainly not adequate when it comes to protecting the most sensitive environments.
OT technology obsolescence periods are much longer than IT. Legacy systems may be in place for 20-25 years at some OT environments. Compare this to the IT world where equipment rarely lasts more than five years. This results in outdated, diverse endpoints where patches aren’t available, or updates can’t be made due to system resource constraints.
IT has had decades to mature security practices and minimize exposure. But the need to manage risk is universal, and organizations must adopt solutions and strategies to secure their OT environments based on their specific needs.
The convergence of IT/OT however means that just as OT equipment that was never designed for a hyperconnected world are vulnerable to threats, the IT environment is also at risk from infections or breaches of OT networks.
#4 Apply Robust Privileged Identity & Credential Management Practices
Password malpractice abounds in OT environments and continues to be a leading cause of breaches. Credentials are often shared internally and externally, and access is not limited to specific network devices or segments.
Reduce the OT risks associated with privileged credential compromise by implementing strong governance over access to privileged account passwords and SSH Keys. Implement an enterprise-grade privileged credential management solution for full control over system and application access through live session management, allowing administrators to record, lock, and document suspicious behavior with the ability to lock or terminate sessions. Such a solution should also eliminate default and embedded passwords, and bring them under active, centralized management.
OT Security from BeyondTrust
BeyondTrust Privileged Access Management (PAM) gives OT security managers the tools they need to secure access, harden endpoints (IoT, IIoT, user devices, servers, etc.), and audit access in a challenging OT environment.
Customers leverage BeyondTrust products to secure OT environments and enable a zero trust architecture by:
- Providing complete visibility and control over OT remote access
- Enabling network segmentation and micro-segmentation to limit lateral movement risk
- Onboarding and managing all privileged identities, accounts, and credentials (passwords, SSH keys, secrets, etc.) for humans and machines
- Enforcing least privilege over access, endpoints, and sessions (including for OT ‘controller’ servers and workstations_.
- Implementing security best practices for vendor access, including credential management, least privilege, and session management
This blended approach secures OT access, hardens the environment, vastly minimizes the attack surface, and helps mitigate internal and external threats.
To learn more about BeyondTrust can help you, check out our OT security solutions page, or contact us today.

Adam White, Sr. Director, Technical Marketing
Adam White is the Director of Technical Marketing and has been with BeyondTrust for 20 years in a variety of technical and operations roles. Originally starting in support and spending over a decade in solutions engineering, Adam brings that technical lens to the BeyondTrust marketing team. He is a vintage electronics and hi-fi nerd (think vacuum tubes); collector of too many amplifiers, guitars, and effects pedals; husband; and father of three teenagers.









