2008: Unifying Vulnerability Management + Endpoint Protection
It all started in 2008, when eEye Digital Security transformed its REM management platform into Retina CS, a solution that could do more than just vulnerability management. Retina CS (short for “Compliance and Security” – or, as we joke internally, for “Chris Silva” our Chief Architect) merged the concepts of vulnerability management and endpoint protection into a single security information technology platform. This was ground-breaking and revolutionary at the time, since it could not only identify asset vulnerabilities but also reveal how assets were being attacked.
2012-2013: Completing the Vulnerability Management Life Cycle
Just before BeyondTrust’s acquisition of eEye, Retina CS added Regulatory Reporting, Configuration Compliance, and Patch Management capabilities to the mix. These extended Retina’s coverage of the vulnerability management life cycle to finding vulnerabilities, analyzing attacks, providing mitigation, and reporting on the results. In addition, Retina CS introduced industry-first technology for cloud, virtual and mobile device assessment – plus an analytics and reporting engine dubbed “Retina Insight.” Even today, no other vulnerability management vendor ships a structured big data warehouse with their product. Ground-breaking and revolutionary to say the least – and centralized under the same installer, platform, and license key.
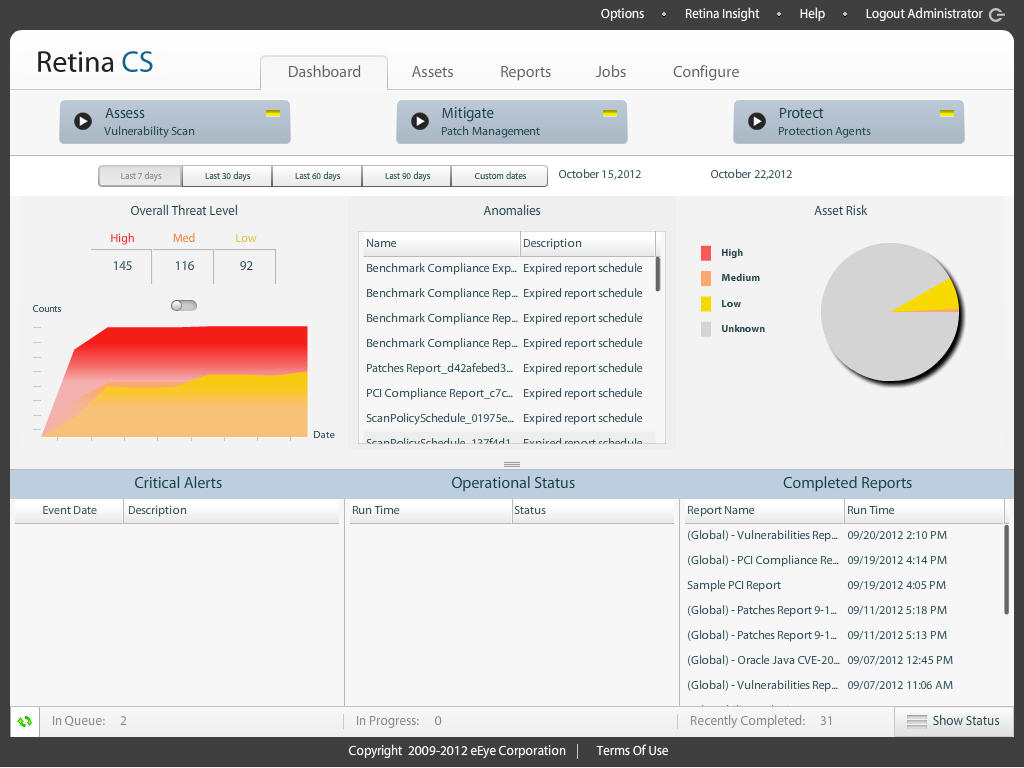 Retina CS vulnerability management interface
Retina CS vulnerability management interface
2014: Bridging Vulnerability Management and Privileged Account Management
Fast-forward to January 2014, when BeyondTrust released the BeyondInsight IT Risk Management platform, built on Retina CS technology. Why? It was clear that, in addition to reducing external risk to infrastructure, Retina CS could mitigate internal, user-based risk by incorporating privileged account management data. This concept merges asset risk management with least-privilege access monitoring on Windows, UNIX, Linux, and OS X devices.
A new revolution is being waged. Imagine knowing all the risks about an asset and how users are interacting with those assets. BeyondInsight can do that – Today!
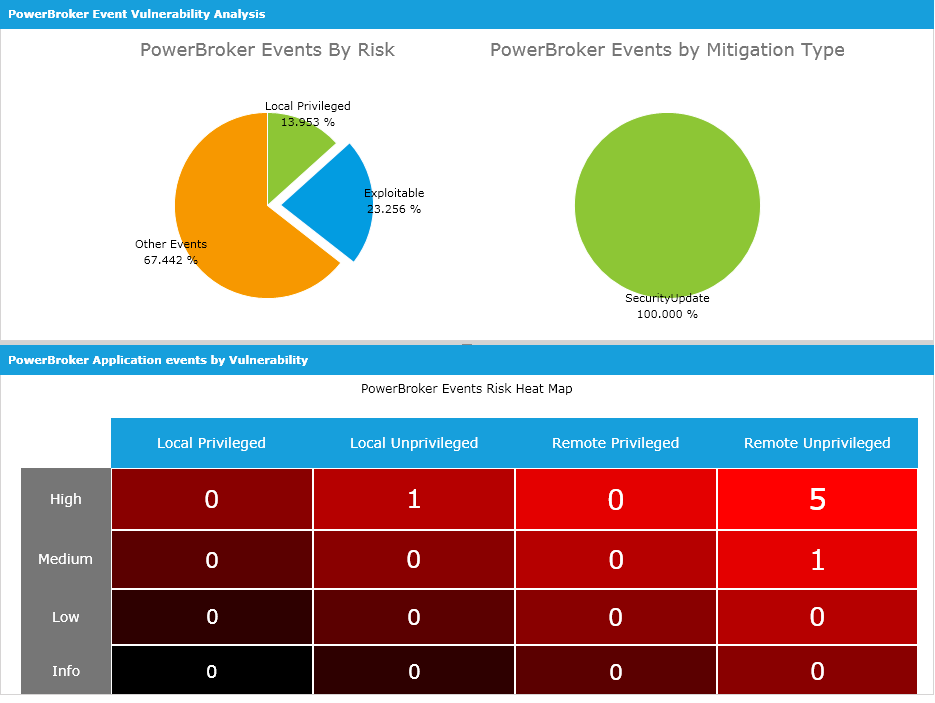 Windows endpoint risk analysis within the BeyondInsight platform
Windows endpoint risk analysis within the BeyondInsight platform
The Future of IT Risk Management
Another generation is in beta: All user accounts discovered and reported in BeyondInsight can now be managed with native PowerBroker Password Safe technology. This evolution enables a complete IT risk management workflow for assets and users. BeyondInsight customers can now not only uncovered asset risk, but also control user access via least privilege management and password vaulting for accounts, services and local access. Using a single platform for all these functions has huge implications for vendor consolidation, cost reduction and training efficiency – let alone risk mitigation.
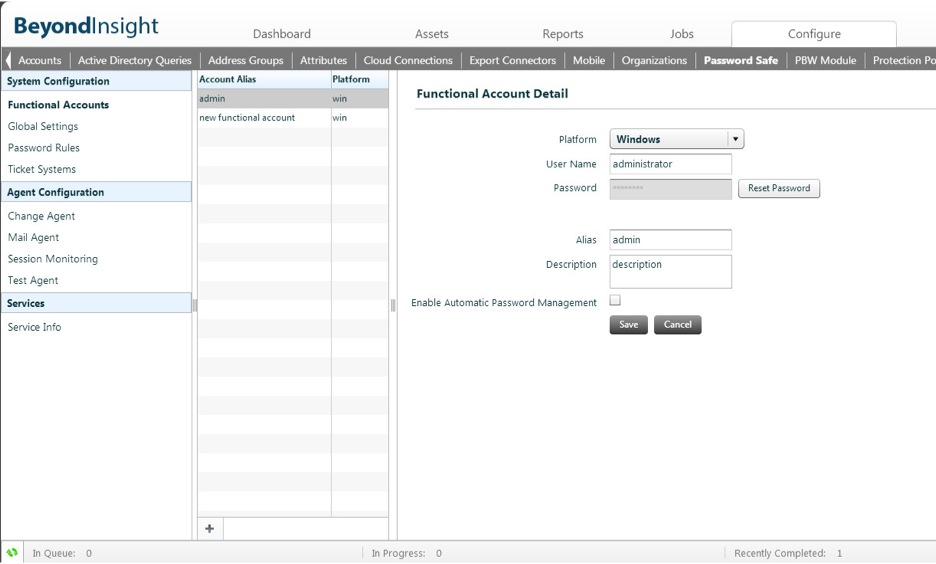 Password vaulting within the BeyondInsight platform
Password vaulting within the BeyondInsight platform
BeyondTrust is leading the way among security management platforms, not by just adding features, but by rethinking how teams manage modern threats and security. Security solutions have evolved. Welcome to the revolution!
> Learn more about the BeyondInsight IT Risk Management Platform
> Learn more about PowerBroker Password Safe

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








