Editors note: This is the fifth in a series of blogs summarizing why customers choose PowerBroker to solve their privileged account management challenges, stemming from the study of our customer base that BeyondTrust commissioned in early 2015. The previous blogs focused on flexible deployment options, low total cost of ownership, better security context, and reporting and analytics. Watch for more in this series.
Nothing kills momentum, effort or results quite like complexity. This is especially true in IT security as over the course of time multiple layers of security are implemented to deal with new and diverse threats. Untangling that complexity has become the number one task of many IT administrators. But the same can be said for the end user. Too much complexity will result in either shadow IT or an avalanche of help desk calls for help on silly system tasks. Like any other organization, BeyondTrust customers struggle with mitigating the productivity-killing effects of IT complexity.
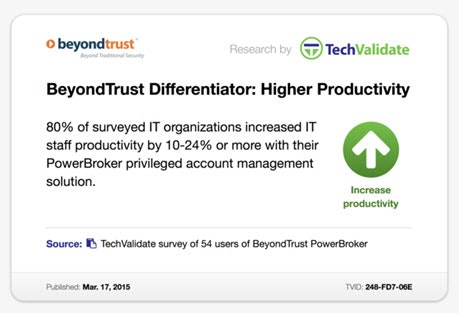
In a survey of more than 50 customers, those customers indicated that higher productivity as a result of using BeyondTrust solutions was a competitive differentiator versus other options in the privileged account management market.
This differentiator was important to RWE Supply and Trading, who was looking to secure and automate the process of managing and cycling privileged passwords, eliminate sharing, remove local admin rights from users, and elevate privileges only when needed. They turned to BeyondTrust. In the words of Loucas Parikos, IT Security Architect, "BeyondTrust PowerBroker has enabled us to eliminate local admin rights to workstations and servers which has resulted in lower support calls and reduced risk to our environment."
BeyondTrust seeks to eliminate complexity not just for the administrator, but also for the end-user. The more you eliminate complexity, the faster you are able to show value in your investment and the faster it will be for end users to adopt the solution.
This was important for Care New England, who were looking to reduce the threat posed by malware, and satisfy HIPAA requirements to restrict access rights to privileged users to a least privilege model. According to Keith Lee, End User Support Manager, “PowerBroker for Windows is transparent to users and gives them the ability to do their jobs safely, without administrator rights. It has eliminated the need to grant admin rights to end-users, and given us the ability to create a more secure, compliant and productive IT environment.”
Here are a few examples of capabilities we provide that are aimed at maximizing productivity:
- Our privileged password management solution, PowerBroker Password Safe, features a clean, uncluttered user interface. This modern, HTML-5 requester interface requires no JavaScript or agents so it’s much simpler for non-technical users. Password Safe also provides network-based asset discovery that scans, identifies and profiles all users and services; automatically onboarding systems and accounts under management.
- Our desktop least privilege solutions, PowerBroker for Windows and PowerBroker for Mac allow admin rights only where needed by proactively identifying applications and tasks that require administrator privileges and automatically generating rules for privilege elevation.
Interested in learning more about how PowerBroker can help you improve the productivity of your IT security team? Contact us today. If you are interested in learning more about all of the PowerBroker differences, check out the free white paper.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








