According to an IDC and HP study, 70% of successful breaches started at the endpoint. With the large-scale shift to remote working due to COVID 19, and the accompanying increase in BYOD and endpoints working outside the network, the endpoint will continue to be the focus of attacks.
Threats to endpoints can come in the form of external attacks (malware, ransomware, hackers, etc.) as well as insider threats, which may be either malicious or unintentional in nature. A compromised endpoint can give an attacker a foothold within an environment, enabling them to launch further attacks on systems to access data and compromise additional endpoints via lateral movement.
A strong endpoint security posture will confer a number of benefits including a condensed threat surface, a reduction in malware and other negative security incidents, a boost in endpoint performance, a clear path to auditability, and improved operations across the IT infrastructure.
"We have seen an increase of 30,000% in phishing, malicious websites, and malware targeting remote users—all related to COVID-19."
https://www.zscaler.com/blogs/research/30000-percent-increase-covid-19-themed-attacks
In this blog, I will highlight the key components of a modern, unified endpoint security program. For a more in-depth overview, you can also check out our new quick guide: The 5 Critical Steps in your Endpoint Security Strategy.
Modernizing Your Endpoint Security Strategy
Traditional endpoint security tools, like antivirus, prevent known attacks and known attack vectors, but miss an average of 60% of modern endpoint attacks. And, while Endpoint Detection and Response (EDR) solutions are a valuable safety net in a defense-in-depth security strategy, they rely on statistical analysis and machines models that may not always correctly recognize the difference between threats and acceptable behavior. This translates into false positives or unacceptable delays in response time.
On the other hand, Endpoint Privilege Management (EPM) solutions apply a different strategy to prevent attacks from breaching endpoints.. EPM solutions prevent threat actors from penetrating an
environment by removing the privileges needed to compromise a host. This mitigates risks at the application layer by controlling which applications are actually permitted to execute, and most importantly, with what privileges. This also solves a critical problem in preventing lateral movement across networks in search of sensitive data to compromise.
How can organizations shift to a more preventative approach to endpoint security?
Below, is a diagram of the 5 Critical Steps for Complete Endpoint Security, from our new white paper, which you may download here.
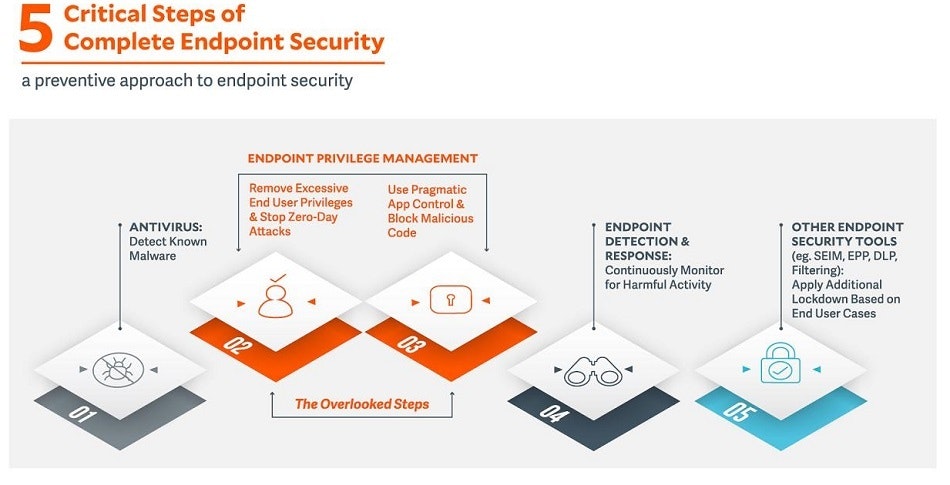
1. Antivirus – Detect Known Malware
Many companies still rely solely on antivirus to secure their endpoints. However, antivirus product only catch 40% of known attacks. For the threats that do bypass AV, some companies will utilize Endpoint Detection and Response (EDR) solutions to detect and then react to threats.
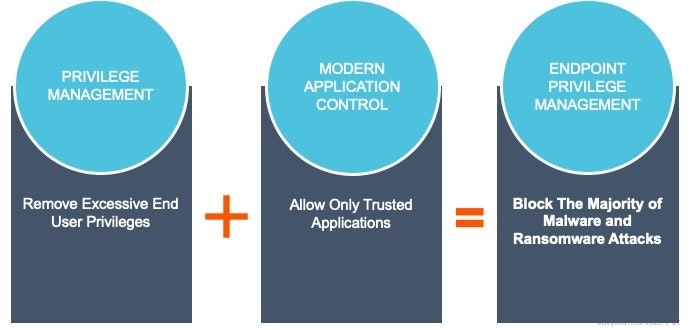
However, starting with a combination of Least Privilege and Application Control will enable you to block most malware and ransomware attacks at the outset.
2. Remove Admin Rights & Stop Zero Day Attacks [Endpoint Privilege Management]
With 40% of known threats covered by AV, it’s time remove admin rights from end users and give them just enough privileges to do their jobs
Another benefit of prioritizing privilege management before other steps is that it helps make the solutions implemented after it work better. For instance, modern EDR will be optimized and the noise reduced when layered upon a solid foundation of zero-admin rights
"Removing administrator rights from end users is one of the single most effective ways to improve overall security posture, but it's not always easy to do without impacting end user productivity. More granular privilege management can improve security posture without impacting productivity.”
3. Use Pragmatic Application Control & Block Malicious Code [Endpoint Privilege Management]
By layering modern application control on top of privilege management, critical functionality in the operating system can now be trusted, making application control easier, and greatly reducing the attack surface.
With application control you can control what applications a user can run regardless of privileges by defining good and bad applications. After all, not all malware needs admin rights. Application control improves security, compliance, and licensing management.
4. Endpoint Detection & Response – to continuously monitor for harmful activity
Now that you have successfully removed excessive admin rights and implemented and application control, it’s time to consider Endpoint Detection & Response (EDR).
EDR is designed to help organizations identify and react to threats that have bypassed their other defenses. These solutions run locally on user workstations or servers to monitor processes, applications, logged in users. EDR determines if malicious activity is present on the system.
Using EDR atop a foundation secured by endpoint privilege management allows EDR tools to focus on a smaller amount of endpoint data. This reduces EDR system noise and improves clarity and performance.
5. Other Security Tools
Endpoint security solutions are not one-size-fits-all. Depending on your industry, compliance mandates, and systems, there are dozens of other endpoint security tools that should be considered. It’s imperative that organizations review specific use cases based on their unique needs.
How BeyondTrust Endpoint Privilege Management Provides Preventative Risk Reduction
BeyondTrust Privilege Management for Windows & Mac is a preventative Endpoint Security solution that removes excessive admin rights, applies modern application control, enables passwordless administration, and gives users just enough privileges to do their jobs and be productive. The solution blocks the majority of malware and ransomware, and protects against both external and internal threats. Utilizing QuickStart policies, organizations receive rapid time-to-value whether deploying the solution on-premises or via SaaS.
To learn more about modernizing your endpoint security approach to withstand today’s threats and performance needs, download our new Quick Guide: The 5 Critical Steps to Endpoint Security

Lindsay Marsh, Senior Product Marketing Manager
Lindsay Marsh is a Senior Product Marketing Manager at BeyondTrust, focusing on Endpoint Privilege Management since 2015. She has over 20 years of experience in IT and cybersecurity. She holds a BA in Business Administration/Marketing from the University of Phoenix. She can be found on LinkedIn and Twitter.








