
Assessing for vulnerabilities on WANs and LANs is nothing new – after all, we should be performing these assessments on a regular basis to satisfy regulatory compliance requirements and achieve good cybersecurity hygiene. So, I think we can all accept that assessments and remediation for LANs and WANs is required by every organization, but what about PANs? If you are not familiar with the concept of a PAN, it is a Personal Area Network that is a typically a non-routable branch of an existing LAN or WAN. It may be the network hosted by your laptop connecting to headphones and mobile devices via Bluetooth, or a subset of cameras with their own WiFi network and SID connecting to your LAN via DVR (Digital Video Recorder) or NVR (Network Video Recorder).
While a typical vulnerability assessment may only detect the NVR, the PAN hosting the WiFi cameras could have their own vulnerabilities. Actually, I should state, they probably will have their own vulnerabilities not be detected during a typical network scan since the PAN is not routable. To that end, they do represent a significant risk and need mitigation because a threat actor can connect to many of these open PANs and leverage these devices, with lateral movement, to compromise your network.
Risk of Lateral Movement
Realistically, the risk is lower for PANs that connect via proprietary protocols or Bluetooth, but the concept is similar. If you can hack one device, the risk of lateral movement or surveillance increases to compromise a user’s identity or additional assets. If you need proof of this type of exploitation, take a look at the screenshot below.
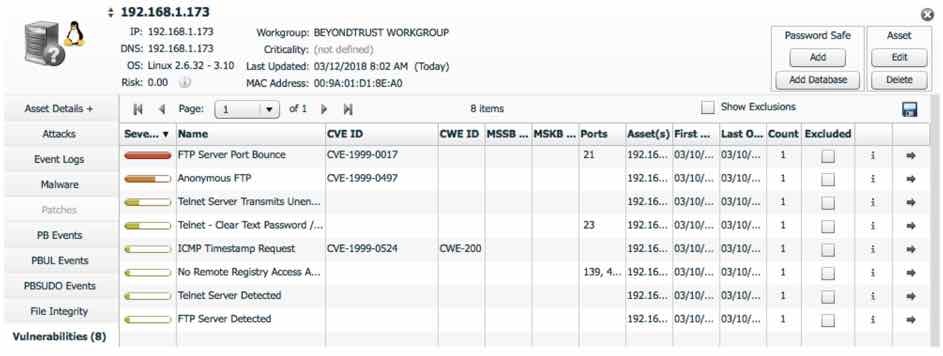
This is from a popular camera system available online for purchase (highest rated vendor). The firmware is up to date, but an assessment of the PAN did reveal some curious vulnerabilities. What is disturbing to me is the age of these vulnerabilities (old school) and the associated CVE’s from 1999 (top two entries). My first thought is that they could be false positives, but after a few manual pen tests, they in fact where very real with no simple path for mitigation. My common sense then asked, “Who uses Anonymous FTP anyways in a real-world environment anymore?” Well, a brand-new camera system designed for homes and businesses certainly does and it is just waiting to be hacked. And, for a standard vulnerability assessment tool scanning a LAN, it would be missed.
So, how does a security professional identify and mitigate this type of threat? It takes more than just reading a vulnerability assessment report.
Identification and Classification
One of the benefits of a good vulnerability assessment solution is asset identification and classification. It is important to identify all the assets within your environment and determine if they could be hosting a PAN. See the screenshot below for a representation.
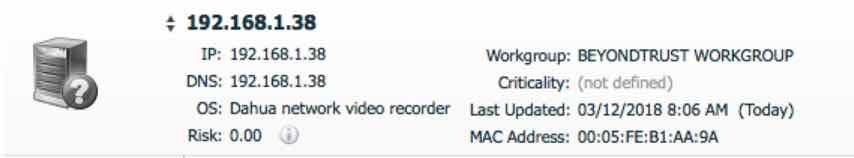
The NVR for this PAN is properly identified by the vulnerability assessment solution and with a little investigation, a security professional can determine it hosts a PAN full of cameras within the environment. The next step is to connect to the PAN (if possible – a threat actor will probably try harder than you), connect a camera via wired connection, or bridge the camera to an accessible network and perform a vulnerability assessment. The results will help determine all the assets on the PAN, and potentially which ones are vulnerable.
Remediation and Mitigation
Then comes the hard part. Can you remediate or mitigate the vulnerabilities sufficiently based on your organization’s security policy? If the vendor has no security updates or implemented the technology so poorly that anonymous FTP is required (like in this example), you might be SOL (Security Out of Luck). Then it becomes a business decision to replace the technology or accept the risk.
A Word of Caution
Now, just to be clear, the definition of a PAN does vary from one vendor to another, and some explicitly state the devices must be wearable. I find that definition too restrictive and that a PAN is more than mobile devices – any time a personal device or network subset is hosted by another technology for its own purposes. An NVR and camera as one example or mobile devices directly connected to a printer is another.
If your organization has these challenges, you are not alone. If you do not believe your business is hosting PANs, you are probably denying a simple fact and not aware they exist. They do any time one device can communicate to others over their own hosted network.
If you need help with a vulnerability assessment that can help uncover these types of threats within your environment, look no further than Retina CS. According to Forrester, the solution is a Leader with advanced capabilities to help perform these assessments and secure your network. For more information, contact us today.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








