
5 Steps to Keep From Being a Statistic in Next Year’s Report
The 2016 Verizon Data Breach Investigations Report has been released, and as with prior years, it doesn’t disappoint. It continues to be the definitive – and entertaining – view of security incidents and data breaches. I’ll dispense with the blow-by-blow, so if you want a more complete write-up, please read Kelly Jackson Higgins’ Dark Reading article. Instead, I have summarized a few key takeaways here as they pertain to two of the most important solutions to mitigate data breach threats: privileged access and vulnerability management.
What are the Key Takeaways From This Year’s Report?
Let’s take a look at a few themes that emerged from the data in this year’s report.
Legitimate user credentials are more of a target
We have known that Privilege Misuse has been among the most common patterns of behavior in data breaches, but this year the biggest storyline is credentials. Legitimate user credentials were used in most data breaches, with some 63% of them using weak, default, or stolen passwords.
This really should not be a surprise for anyone. Our own study of privileged access management showed that more than a fourth of companies have no controls over privileged access.
People and User Devices both represented a greater percent of breaches in 2015
Why? Phishing and malware infections still lure in users who in turn infect the systems and applications they interact with. How does it happen? 13% of people click on phishing attachments, with the median time to the first click on the attachment being 3 minutes, 45 seconds. These insiders then become compromised.
From a Privilege misuse perspective we tend to focus on administrators and executives, however, the findings indicate that these two groups only represented 28%.
- Almost 1/3 were found to be end users who have access to sensitive data that they need to do their jobs.
- A smaller percentage (14%) were in executive roles or in high privilege jobs like admins.
- There were higher rates of collusion between internal and external parties in 2015. (see the Verizon chart below)
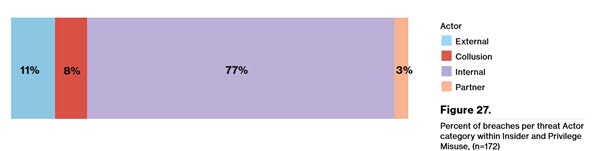 It’s getting more difficult to detect a breach
It’s getting more difficult to detect a breach
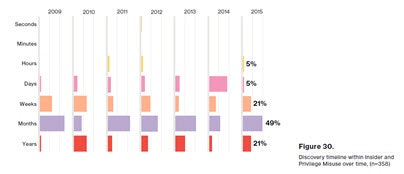 In nearly 82% of cases reviewed in the report, compromises happen in minutes, but in nearly 68% of the time data exfiltration (moving large volumes of data outside the organization) happens in just days. The gap between compromise and detection is increasing. For proof, look at the graphic to the right (courtesy Verizon). A lot of damage can be done in months.
In nearly 82% of cases reviewed in the report, compromises happen in minutes, but in nearly 68% of the time data exfiltration (moving large volumes of data outside the organization) happens in just days. The gap between compromise and detection is increasing. For proof, look at the graphic to the right (courtesy Verizon). A lot of damage can be done in months.
You’ve got 30 days to fix that vulnerability, and the clock starts ticking….now!
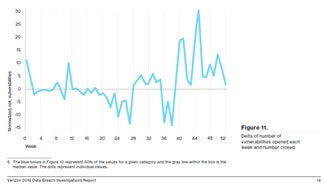 This year’s report indicates that half of all exploitations from system vulnerabilities happen between 10 and 100 days after the vulnerability is published, with the median around 30 days. Interesting, but if you look at the data on new vulnerabilities like what’s in the graph at left, it seems like no progress is being made despite having data on prioritizing the vulns. Why? Sometimes you just can’t fix a vulnerability—maybe it will break something or renders the system incompatible with other applications.
This year’s report indicates that half of all exploitations from system vulnerabilities happen between 10 and 100 days after the vulnerability is published, with the median around 30 days. Interesting, but if you look at the data on new vulnerabilities like what’s in the graph at left, it seems like no progress is being made despite having data on prioritizing the vulns. Why? Sometimes you just can’t fix a vulnerability—maybe it will break something or renders the system incompatible with other applications.
Recommendations – How to Use This Data to Improve Security
Your head is swimming, right? All this data, what do you do with it? Let us give you 5 focus areas to help you mitigate the risks of insiders misusing their privileges, or outsiders seeking to become insiders.
1) Lock down all enterprise credentials in a password safe
- Scan, identify, and profile all users, accounts, and assets; automatically onboard systems and accounts under management
- Rotate each password automatically based on age or after each login by an administrator
- Provide context from workflow requests so you can granularly limit access based on hours, days, etc.
- Monitor sessions in real time, giving you true dual control over user activity
It seems that only 14% of privilege abuse was attributed to administrators – so what’s the point? The point is that in addition to these admin accounts having the golden keys, the other 86% of the accounts can be used as a launch point inside your organization. Take end user phishing, which is trending up in 2016. Once compromised, these accounts can be used to gain a foothold within the perimeter. This is where we can make it more difficult to move laterally. Attackers may target systems with static, weak and aged passwords on servers, networking devices, databases etc. For some example of privilege vulnerabilities that can expose your soft underbelly, here are a couple of our examples from our resource center:
2) Implement least privilege not only for admins but also for partners, contractors and end users
From an end user perspective hackers compromise these accounts to hunt for more highly privileged credentials, or they use those accounts to access authorized resources and applications (like banking apps to perform seemingly valid transactions).
- Enforce least privilege on all end user machines and servers, controlling root and admin access
- Elevate rights to applications, not users, using asset vulnerability data to make privilege elevation decisions
3) Multifactor, Multifactor, Multifactor
Removing access and embracing least privilege across end users is a valid way to minimize the internal attack surface. However, what if a user account actually has the necessary rights to access that sensitive resource or application? Multi-factor authentication raises the bar given the number of breaches that involve weak, stolen, or default credentials. Attackers need credentials to move laterally and multi-factor makes that movement more complex. When reviewing the need for multifactor focus on who has the access and what they are accessing.
4) Integrated threat and behavioral analytics to reveal what might be hidden in volumes of data
Monitor assets data as well as users and network activity in order to correlate, detect, and respond to inappropriate or suspect events:
- Aggregate and correlate users and asset data to centrally baseline and track behavior
- Identify potential malware threats buried in asset activity data
- Measure the types and velocity of asset changes to flag in-progress threats
- Isolate users and assets exhibiting deviant behavior
- Reduce false positives by viewing multiple perspectives across users, assets and network (command and control
- Generate reports to inform and align security decisions
5) Improve the discipline of vulnerability assessments and patching
It’s not new. It’s not sexy. But it’s absolutely required.
Implementing an enterprise vulnerability program that has complete visibility over your asset base is critical (desktop, server, network, application, physical, cloud, virtual, mobile… you get the point).
Prioritize patches based on real risk:
- Patch asset and privilege vulnerabilities – remember, from a privilege perspective removing excessive privileges on Windows mitigates 85% of security incidents.
- Target vulnerabilities based not just on business impact but how they are being exploited “in the wild”. Most scanners can map findings to specific exploits and exploit toolkits that are packaged to use these vulnerabilities in the wild. (oh yeah – Retina does this!)
- Address systems that can’t be patched through isolation or config changes.
Watch for more DBIR insights from BeyondTrust coming soon! In the meantime, if you would like to speak with a security specialist on how you can reduce data breach threats with privileged access management and vulnerability management, contact us today!

Brad Hibbert,
With over 20 years of experience in product strategy and management, Brad leads BeyondTrust’s solution strategy. He joined BeyondTrust via the company’s acquisition of eEye Digital Security, where Brad led strategy and products. Under Brad’s leadership, eEye launched several market firsts, including vulnerability management solutions for cloud, mobile and virtualization technologies. Prior to eEye, Brad served as Vice President of Strategy and Products at NetPro before its acquisition in 2008 by Quest Software. Formerly, at FastLane Technologies, which was sold to Quest Software in 2001, Brad worked extensively with key Microsoft business units on product direction and go-to-market strategies.








