 In April 2018 BeyondTrust asked security and IT leaders around the world about their cloud adoption plans and the risks associated with those plans. (You can read the full report from the study’s June publication here.) What we learned from that study confirmed our assumptions and helped customers lay out a roadmap for delivering enterprise-level cloud security. Let’s look at what we learned and how it can help you.
In April 2018 BeyondTrust asked security and IT leaders around the world about their cloud adoption plans and the risks associated with those plans. (You can read the full report from the study’s June publication here.) What we learned from that study confirmed our assumptions and helped customers lay out a roadmap for delivering enterprise-level cloud security. Let’s look at what we learned and how it can help you.
Get these 8-steps to secure Cloud in this white paper: Protecting and Enabling the Cloud get the guide
How Enterprise Cloud Adoption is Changing
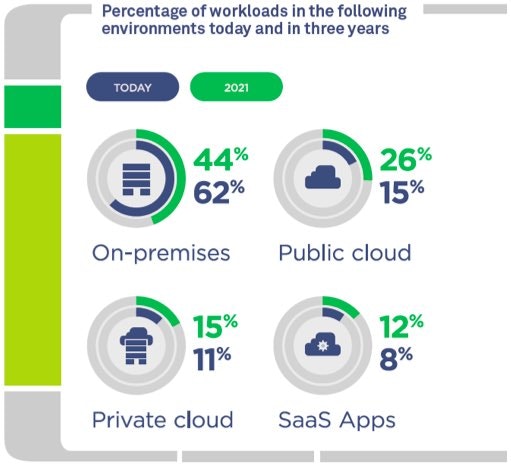 Respondents to our Implications of Using PAM to Enable Next-Generation Technologies survey indicated that – today – 62% of workloads are on-premises, with 15% in a public cloud, 11% in private clouds and 8% in SaaS applications.
Contrast that with three years from now: On-premises drops to 44%, public cloud jumps to 26 percent, private cloud increases to 15 percent, and SaaS moves up to 12 percent. With such an increase in cloud-hosted workloads in the next three years, it’s vital for organizations to address security issues in their hybrid environments. Check out the graphic from the study.
Respondents to our Implications of Using PAM to Enable Next-Generation Technologies survey indicated that – today – 62% of workloads are on-premises, with 15% in a public cloud, 11% in private clouds and 8% in SaaS applications.
Contrast that with three years from now: On-premises drops to 44%, public cloud jumps to 26 percent, private cloud increases to 15 percent, and SaaS moves up to 12 percent. With such an increase in cloud-hosted workloads in the next three years, it’s vital for organizations to address security issues in their hybrid environments. Check out the graphic from the study.
What Are the Risks?
As cloud ecosystems evolve, and IT perimeters vanish, it’s increasingly critical to ensure visibility and security across hybrid environments. Our study showed that 52% of the time, it’s trusted users doing inappropriate things for innocent reasons that cause the most problems. In 18% of the cases, it’s trusted insiders going rogue, and in 15% of the cases, it’s outsiders gaining privileged access to steal credentials. The question becomes: How can organizations like yours securely enable the cloud to achieve business agility goals, while unifying security controls for on-premise assets you already have in place?Cloud Security Best Practices Are On-Prem Security Best Practices
We devised five progressive steps you can take to get control of your cloud assets. (tl;dr – you can use these same steps to apply controls over your on-prem assets, too. Save time and money that way.) Take an objective look at your environment and determine how you measure up. 1) Perform a discovery and inventory of cloud assets Performing continuous discovery and inventory of assets across physical, virtual, and cloud environments ensures that only properly configured and approved assets are available and used in your environment. Just as important to cloud asset discovery is the management of supporting containers, for example Docker images deployed throughout the environment. Having this data will improve the visibility over Docker container usage and potential risks. Common attributes to scan for in Docker images and containers include:- Basic image data: OS identification, repository tag, image ID; and where available, image size, creation date, and image author
- Enumerations: Services, processes, ports, certificates, users and user groups, and the network stack
- Installed software packages
- Registry and system files
- Enterprise password management – Discover accounts, randomize, rotation, and check-in/check-out passwords.
- Session monitoring, management, and recording – Record privileged sessions in real- time via a proxy session monitoring service and enable dual control.
- Advanced workflow controls – Provide additional context to requests by considering the day, date, time, and location when a user accesses resources to determine their ability to access those systems.
- Advanced segmentation – Route all remote access sessions through the PowerBroker Password Safe proxy for management, reporting, and enforce segmentation from authorized connectivity and attack.
BeyondTrust Can Help
The BeyondTrust solution for secure cloud enablement discovers all cloud instances in the environment, groups cloud assets for consistent privilege management, and scans for security vulnerabilities and privilege-related risks. By unifying policy, management, reporting, and analytics across both on-premise and cloud environments, organizations can meet stringent security and compliance controls over cloud usage, while achieving business agility goals.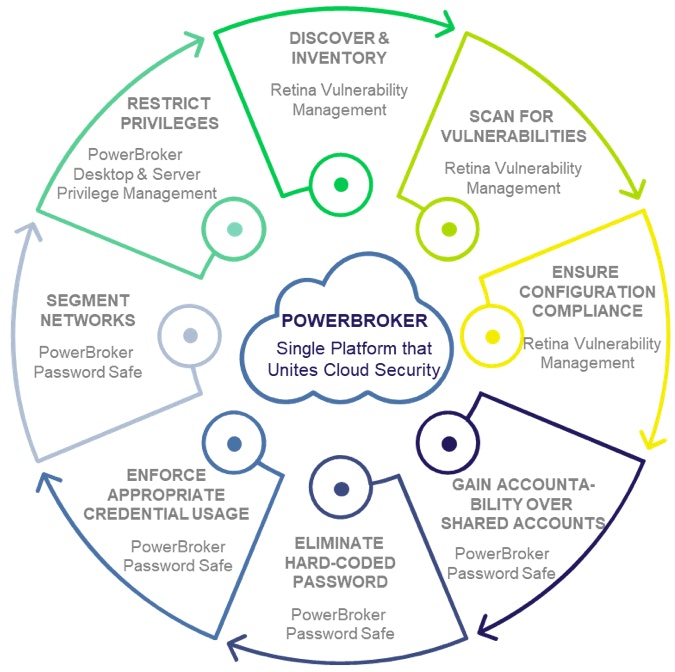 How prepared are you for the cloud? Want more detail on the five steps, including how to make them work in your enterprise? Download the white paper.
For more information on how BeyondTrust can help you accelerate your business transformation to the cloud through the power of privileged access management, contact us today.
How prepared are you for the cloud? Want more detail on the five steps, including how to make them work in your enterprise? Download the white paper.
For more information on how BeyondTrust can help you accelerate your business transformation to the cloud through the power of privileged access management, contact us today.
Get these 8-steps to secure Cloud in this white paper: Protecting and Enabling the Cloud get the guide

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








