
Why do cybersecurity projects fail? Sometimes, the biggest stumbling block to rolling out a security isn’t how secure it is; it’s not down to the price; and it’s not down to compliance mapping. It’s how much the end user wants to adopt it.
Let’s face it. With a few exceptions, we are all human beings. We generally do not like change. If we have been doing a job the same way for the last 10 years, there is a certain reticence to change what we are doing. We naturally gravitate towards solutions that cause the least variance to the job that we do.
By way of example, imagine I am a production control technician at a bakery. I have been doing the same job for years, which involves logging onto production control servers, uploading new batch routines, and performing general maintenance tasks such as backup. My superiors tell me that they have to introduce a new system to manage the passwords that I normally keep on post-it notes under my keyboard, and they want to record what I’m doing for compliance.
A vendor is chosen (I have little input), and the backup job that used to take me less than a minute to set up, now takes me 4-5 minutes to start. Not only that, but the system has gone down 5 times in recent weeks, preventing me from doing my job. I want to go back to my post-it notes — they never went down!
One of the biggest hurdles to implementing IT security isn’t technical — it’s personal adoption. You can have the best security system in the world, but if it’s difficult to use, people will revolt against it and try to find workarounds - not what you want to happen.
Bearing in mind that every enterprise password security system meets certain security objectives, what we are left with is usability. I worked for a competitor in the privileged password management space a few years ago, and users used to tell me that password requests were akin to navigating the Starship Enterprise out of a space dock.
With that in mind, we’ve taken steps to add features that are meant to be intuitive and help speed our users’ productivity – starting with a new interface we released in Password Safe version 6.4 – Smart Rules, Smart Groups, and DirectConnect.
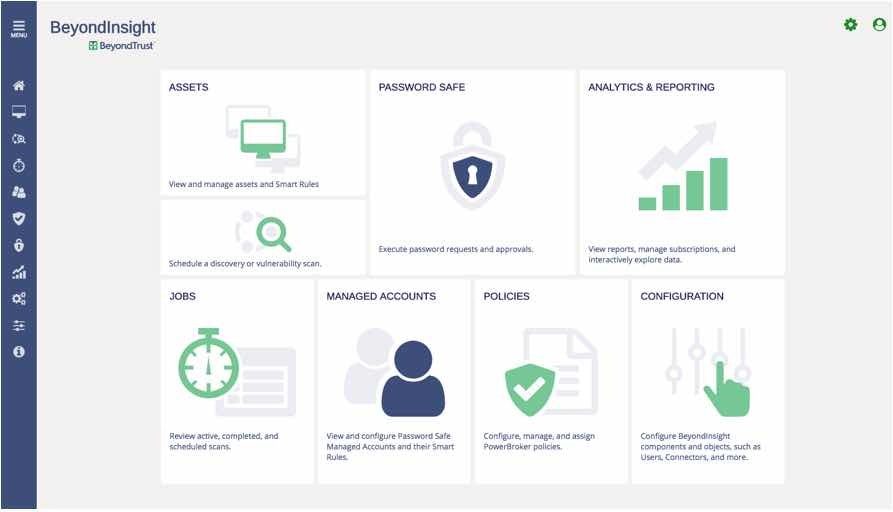 HTML 5 Dashboard: Unique to each user’s role-based access, the new dashboard provides quick access to view assets or generate reports.
HTML 5 Dashboard: Unique to each user’s role-based access, the new dashboard provides quick access to view assets or generate reports.
My New Year’s Resolution at BeyondTrust is to make the user experience as invisible as possible. In fact, rather than add any impact, my goal is to actually make a user’s job easier.
If you are used to logging on directly from PuTTY - great! MobaXterm? Sure thing!! If you’d like to learn more about our latest version of PowerBroker Password Safe, check out our new features document, or contact us for a personalized demo.

Martin Cannard,
Martin has been helping organizations solve challenges in the privileged account management and identity and access management space for over 24 years. At Dell Software, Martin managed a team of Solution Architects, focused on designing and implementing solutions in the Privileged Account Management (PAM) space. Prior to joining Dell, Martin was Sr. Product Manager for Novell Privileged User Manager, a privilege management application acquired from Fortefi, an organization where he served as Vice President, Corporate Development. Prior to this, he was Program Manager of Client Technologies at Symantec where he was responsible for many ground-breaking field and channel enablement applications. Additionally, Martin managed the European QA group at Axent Technologies and has held various management positions in consulting, systems development, and operations. Martin is a regular speaker for security events, and webinars.








