 Today, most organizations are now adopting a risk-based, multi-layered approach to cyber security. Yet, even with important solutions such as firewalls, IPS, AV, and anti-malware in place, data breaches and other crippling attacks continue to disrupt organizations and their customers across the globe with alarming regularity.
Today, most breaches originate via end users …
Today, most organizations are now adopting a risk-based, multi-layered approach to cyber security. Yet, even with important solutions such as firewalls, IPS, AV, and anti-malware in place, data breaches and other crippling attacks continue to disrupt organizations and their customers across the globe with alarming regularity.
Today, most breaches originate via end users …
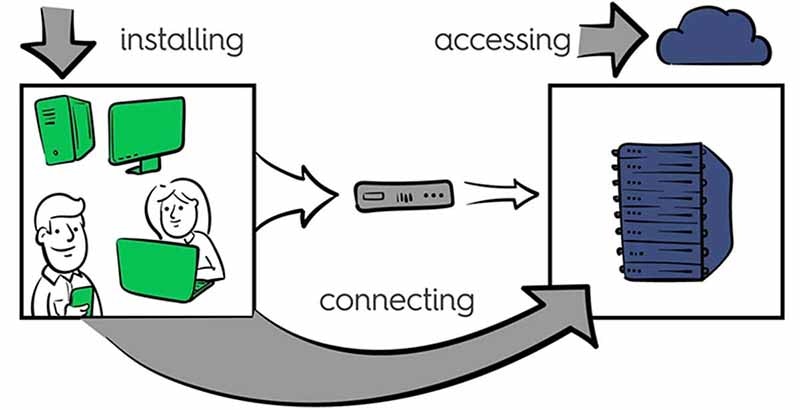
- installing something they shouldn’t,
- connecting to somewhere they shouldn’t,
- or accessing data they shouldn’t.

Matt Miller, Director, Content Marketing & SEO
Matt Miller is Director, Content Marketing at BeyondTrust. Prior to BeyondTrust, he developed and executed marketing strategies on cybersecurity, cloud technologies, and data governance in roles at Accelerite (a business unit of Persistent Systems), WatchGuard Technologies, and Microsoft. Earlier in his career Matt held various roles in IR, marketing, and corporate communications in the biotech / biopharmaceutical industry. His experience and interests traverse cybersecurity, cloud / virtualization, IoT, economics, information governance, and risk management. He is also an avid homebrewer (working toward his Black Belt in beer) and writer.








