In this blog, I will parse through key findings of the just-released research report: Identity Security: A Work in Progress, published by the Identity Defined Security Alliance (IDSA). This new research builds on the findings of IDSA’s The State of Identity report, released in December, which explored the implications of the explosion of human and machine (application, service account, software robot, etc.) identities. In fact, according to the December IDSA report, 52% of respondents stated that identities have increased over five-fold in the past 10 years.
This past April, IDSA sponsored Dimension Research’s survey of 502 personnel who are directly responsible for IT security or IAM at a company with more than 1,000. The report based on findings of that survey focuses on the top identity-based threats and what makes some organizations more successful than others in protecting identities.
Why is this IDSA research important? Most cyberattacks today revolve around identities, and the credentials and privileges of those identities. In more recent months, the ongoing COVID-19 pandemic has compelled a mass migration to work from home. This sudden, largely unprepared, shift to supporting remote workforces generated a growth spurt in BYOD and shadow IT. It’s also further blurred boundaries between work and personal spheres. Already vulnerable prior to the pandemic, corporate identities are clearly at heightened risk in these times.
Absent rigorous identity-based security controls in place, such as enforcing unique, randomized passwords, the exposure of one account for an identity can lead to exposure of many accounts for that identity, crossing both corporate and personal boundaries. Of course, the implications are always far more serious when privileged identities and privileged access are at stake, since they can fast track access to the most sensitive resources and open up lateral access to an attacker or piece of malware throughout a network.
Here are some top-line findings from the new IDSA report:
- 94% of organizations have suffered an identity-related breach, 79% over the last 2 years
- Human identities are more likely to be compromised than machine identities
- Organizations that implement identity-based security controls are far less likely to incur breaches
- 66% succumbed to a phishing-related breach in the last 2 years
- 99% of the identity-related breaches are believed to be preventable
Here’s a breakdown of the types of identities behind the breaches:

While employees and privileged users were broken down separately in the survey question shown above, it’s important to remember that non-IT employees can, and often do, have privileges—even if they are not recognized as a traditional privileged user (such as an IT admin). Regular office employees often have admin rights to their local desktop computer, or have other sensitive/privileged access for certain business purposes. All of these privileged use cases, including for machine accounts, are within the purview of privileged access management (PAM), which falls within the broader space of identity and access management (IAM).
Recently, the Identity Defined Security Alliance (IDSA), of which BeyondTrust is a contributing member organization, developed a library of identity-based security approaches and outcomes, which can be found in detail on their site here. The question below asks how far along organizations are in implementing these approaches, which later in the report is used to correlate with security outcomes measured in number of breaches.
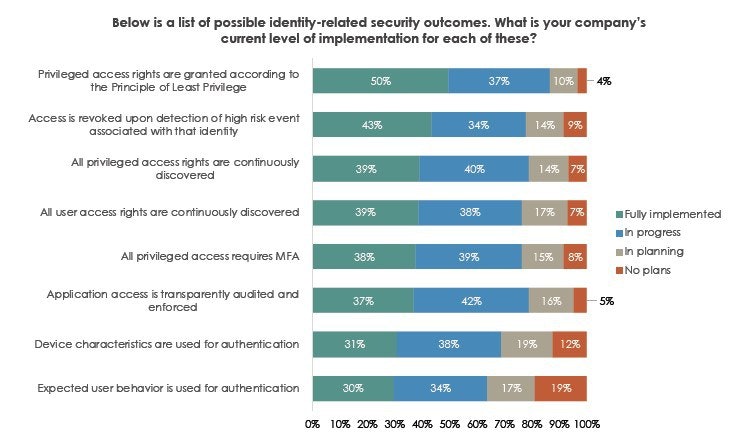
According to the findings displayed in the table above, less than half of organizations have fully implemented key identity-related security approaches. Again, many of these approaches—enforcing least privilege, continuously discovering privileged accounts, revoking access (for privileged users, etc.), managing application access—lean heavily on, or absolutely require, PAM solutions.
The report then goes on to categorize respondents into three security tiers: forward-thinking, practical, and reactive. Forward-thinking organizations were by far the most likely to have implemented the security approaches above, with reactive organizations falling at the other end of the spectrum. 59% of companies with reactive security approaches experienced a breach in the past year, and 48% of organizations with practical approaches experienced a breach, but that number plummets to only 34% of companies with forward-thinking approaches. This data clearly reveals a strong correlation behind identity-centric security maturity and an organization's overall security posture.
One other positive trend highlighted in the report is that organizations are making progress in better aligning security and identity, and this alignment is perceived to be measurably improving IT security outcomes.
Next Steps for Protecting Enterprise Identities
CDW Canada recently published research on security trends from the last year. While that report was more broad in scope than the identity-focused IDSA report, the one thread woven throughout all the trends of the CDW study was the pivotal nature of identity-based security on effectively managing today's cyberthreats. In fact, CDW survey respondents from mid-sized and larger organizations ranked IAM as their most effective security tactic/control, while smaller organizations had it ranked third (behind web content filtering and security awareness training).
Centralizing security around an identity makes more security sense than ever in this era characterized by the unrelenting proliferation of endpoints and identities, and the sharp ascent of remote work, BYOD, and shadow IT. Securing identities—especially privileged access and privileged identities, and controlling every privileged session (whether employee, vendor, remote worker, or on-premise) will continue be the most substantive approach to condensing the IT risk surface, shortenining attack windows, and hardening enterprise security against internal and external threats.
You can read the full IDSA report here: Identity Security: A Work in Progress
Morey J. Haber, IDSA Technical Working Group Member and BeyondTrust CTO and CISO, and Diane Hagglund, Founder and Principal of Dimensional Research will also explore implications of the IDSA report and how to best protect enterprise identities in this webinar: Trends in Identity Security webinar.
And, for those who want to really sink their teeth into grokking identity-based threats and how to defend against them, there’s perhaps no better resource than the book: Identity Attack Vectors: Implementing an Effective Identity and Access Management Solution. The co-authors, Morey J. Haber, and Darran Rolls (CTO at SailPoint), pair their decades of combined IT experience across identity-related disciplines (IAM, PAM, etc.) to explore everything from the fundamental definitions and structures of enterprise identities, to future-looking considerations, to practical implementation scenarios.

Matt Miller, Director, Content Marketing & SEO
Matt Miller is Director, Content Marketing at BeyondTrust. Prior to BeyondTrust, he developed and executed marketing strategies on cybersecurity, cloud technologies, and data governance in roles at Accelerite (a business unit of Persistent Systems), WatchGuard Technologies, and Microsoft. Earlier in his career Matt held various roles in IR, marketing, and corporate communications in the biotech / biopharmaceutical industry. His experience and interests traverse cybersecurity, cloud / virtualization, IoT, economics, information governance, and risk management. He is also an avid homebrewer (working toward his Black Belt in beer) and writer.








