
I'll get to that a bit later. First, let's talk about the world of acronyms and industry jargon we live in – every year the list grows. I recall a couple of decades ago (yes, I am that old), a conversation with a customer about LDAP. They were telling me how they needed LDAP support for a single sign-on product I was selling. When I pressed the customer for more information, it turned out that they did not understand what LDAP was, it was just a new concept his director learned about after reading trade magazines.
DevOps is the new kid on the block. I detect a similar misunderstanding around the term DevOps as I saw years ago with LDAP.
Let’s dig a little deeper into what DevOps actually is.
DevOps is an abbreviation of development and operations. DevOps is not a product, it is a cultural mindset change. DevOps is not something you can order on a menu, it is about breaking down barriers between teams. It is about the tools you use. It is about how apps are designed. DevOps is about high quality and increased speed of delivery.
There are a number of benefits to DevOps:
- Very frequent and small updates that get bugs fixed faster, and features to customer quicker.
- Large more complex architectures are decoupled into separate projects with a single focus. This is referred to as a microservices. This reduces the complexity of coordinating updates as each microservice operates independently.
- Continuous integration and delivery help address the challenges of frequent updates that traditionally present operational challenges.
As with all processes, DevOps comes with its own set of terms and components:
- Continuous integration – This refers to a development process where developers merge their code to a shared repository several times a day.
- Continuous delivery – Extending Continuous Integration, this is the automated process that takes developer code and turns it into finished applications.
- Continuous deployment – This builds on continuous delivery, and releases code to customers.
- Containers – Lightweight self-contained package of software that can be executed as an isolated process.
- Microservices – These are discrete application components that are generally used in combination to form part of a larger application.
- Immutable instances – A server that is never modified. If updates are required, a new instance replaces it. Typically, immutable instances have a life of 7-10 weeks.
DevOps seems so obvious once you think about it. Imagine you have a soccer team and the goalie is underperforming, you wouldn’t swap out the entire team. This is what happens with traditional monolithic applications. You deliver an entirely new application even though one element has been changed. In a container world, each player on your soccer team is a microservice. If the player needs to be replaced or needs help, we just replace that player or add more. Okay maybe that was not the perfect analogy, but you get my point.
The low hanging fruit for DevOps security is to provide secure storage and management of credentials used by orchestration products that automate the process of building containers and deploying microservices, but depending on how and where your apps are deployed, the story is a lot deeper.
Consider the entire delivery stack, from bare metal operating systems to container management. Secure password management is a given for all areas, but we need to make sure that we also look at vulnerabilities, least privilege, and session management.
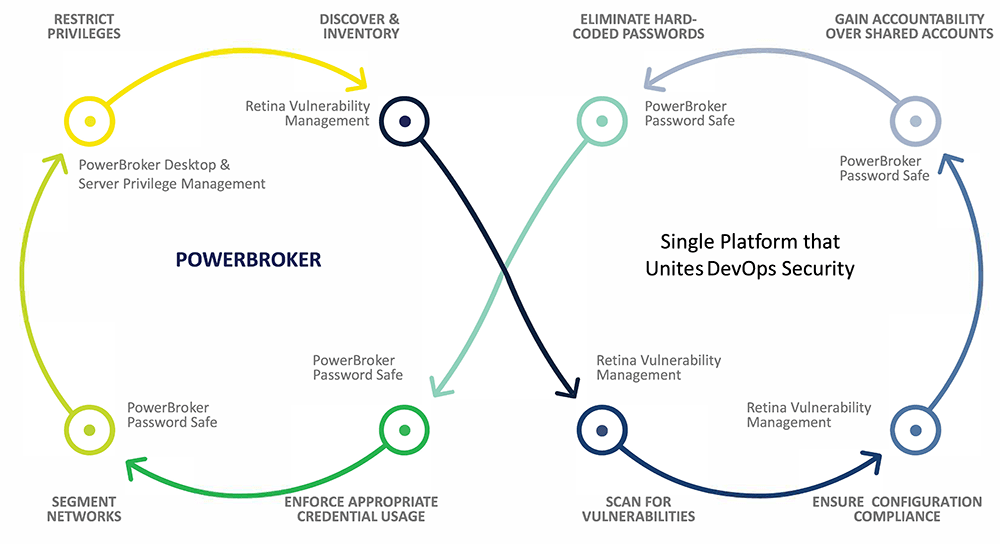
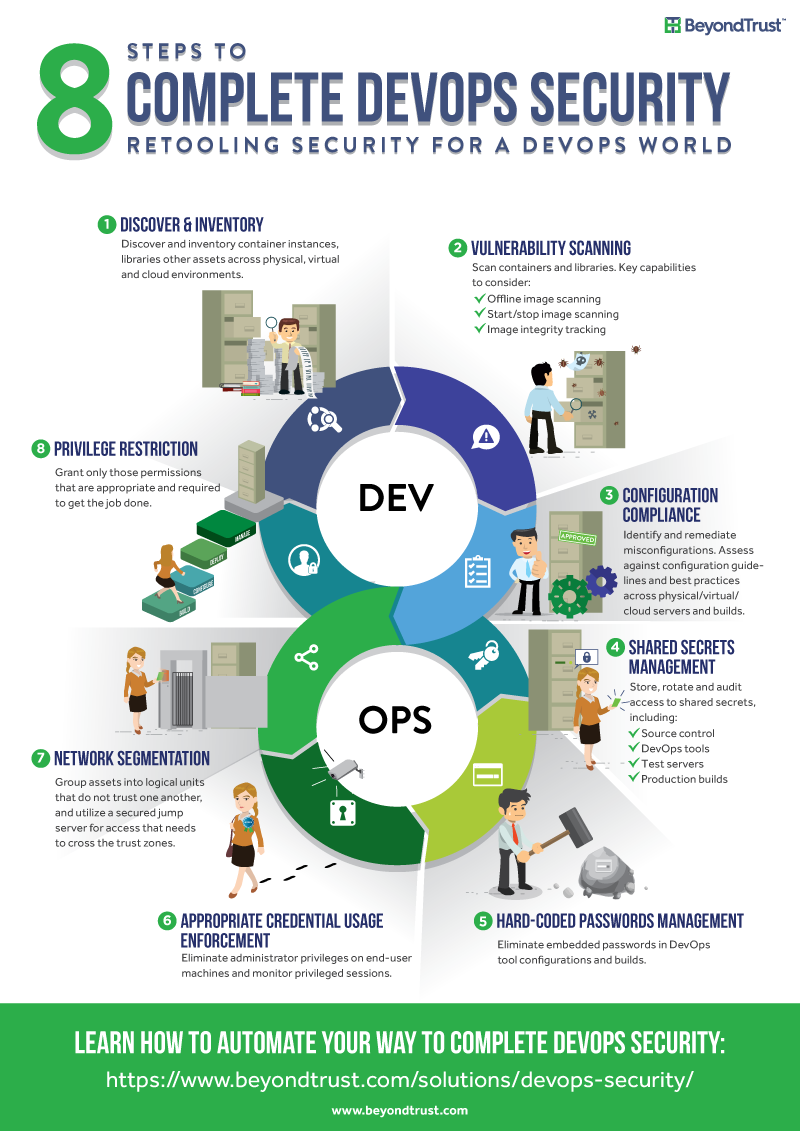
- Discover and inventory – You only know what you know. Continuously scan your environment to discover systems and privileged accounts.
- Scan for vulnerabilities – Continuously check those bare-metal systems, hypervisors, virtualized hosts, and containers are free of vulnerabilities.
- Ensure configuration compliance – Ensure configurations are consistent and properly hardened across the entire DevOps lifecycle.
- Gain accountability over shared accounts – Manage, control and audit access to shared accounts including developer access to source control, DevOps tools, test servers, and production build machines.
- Eliminate hard-coded passwords – Remove hard-coded passwords in DevOps tools configurations, build scripts, code files, test builds, and production builds.
- Enforce appropriate credential usage – Eliminate direct admin privileges on desktops and servers by storing and managing credentials. Workflow processes for elevating, and monitoring privileged sessions.
- Segment networks – Enable network segmentation through use of session management tools. Ensure access control is enforced based on the context of user, role, app, and data being requested.
- Restrict privileges – Enforce least privilege controls to lock down and audit administrative access to target environments, development workstations, and containers.
BeyondTrust’s PowerBroker and Retina solutions combine to provide continuous holistic protection across the DevOps environment.
The PowerBroker Privileged Access Management Platform for DevOps Security
BeyondTrust solutions for DevOps Security are part of the PowerBroker Privileged Access Management Platform, which delivers visibility and control over all privileged accounts, users. and assets. The platform integrates a comprehensive set of PAM capabilities across on-prem, virtual, and cloud to simplify deployments, reduce costs, improve system security, and reduce privilege-related risks. PowerBroker solutions include:
- Enterprise Password Security: Provide accountability and control over privileged credentials and sessions
- Server & Infrastructure Privilege Management: Control, audit, and simplify access to DevOps systems
- Endpoint Privilege Management: Remove excessive user privileges and control applications on endpoints
- Vulnerability Management: Scan networks, the web, cloud, virtual, and IoT infrastructure to pinpoint vulnerabilities and malware attacks
To learn more about how we can help you secure your DevOps environment using privileged access management solutions, download this free white paper, “8-Step Best Practices Guide for Using Privileged Access Management and Vulnerability Management to Secure DevOps”, and check out this nifty infographic!

Martin Cannard,
Martin has been helping organizations solve challenges in the privileged account management and identity and access management space for over 24 years. At Dell Software, Martin managed a team of Solution Architects, focused on designing and implementing solutions in the Privileged Account Management (PAM) space. Prior to joining Dell, Martin was Sr. Product Manager for Novell Privileged User Manager, a privilege management application acquired from Fortefi, an organization where he served as Vice President, Corporate Development. Prior to this, he was Program Manager of Client Technologies at Symantec where he was responsible for many ground-breaking field and channel enablement applications. Additionally, Martin managed the European QA group at Axent Technologies and has held various management positions in consulting, systems development, and operations. Martin is a regular speaker for security events, and webinars.








