- Setting up a secured enclave for sensitive systems to isolate management
- Requiring third parties to go through a proxy
- Recording all sessions with dual control capabilities to view, terminate, etc.
- Applying dynamic workflow (i.e. do not allow third party to access these servers during production periods, or after hours depending on their management function, etc.) to further tighten access and embrace behavior modeling to detect suspect activity
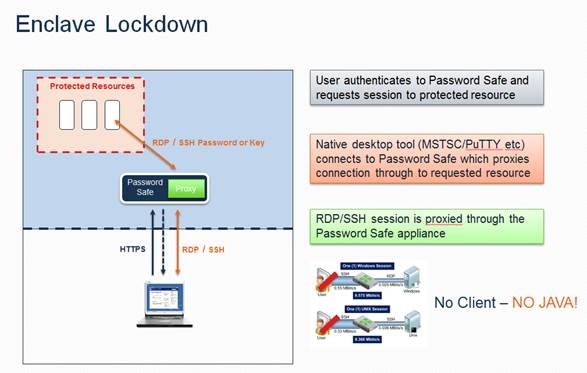 Even if a vendor has a set of credentials for the managed resource, you still need a gateway proxy capability in the same manner as providing access through a managed account.
A common practice is to set up VPN access directly to interact with an appliance which is used to proxy activities to a secured sever. The server is completely isolated using firewalls to only allow access from the appliance. Workflow approvals can be set up to require employee verification and approval of the session. All current sessions can be viewed by an employee with options to view, manage or terminate the sessions. See a screenshot of how we do that below.
Even if a vendor has a set of credentials for the managed resource, you still need a gateway proxy capability in the same manner as providing access through a managed account.
A common practice is to set up VPN access directly to interact with an appliance which is used to proxy activities to a secured sever. The server is completely isolated using firewalls to only allow access from the appliance. Workflow approvals can be set up to require employee verification and approval of the session. All current sessions can be viewed by an employee with options to view, manage or terminate the sessions. See a screenshot of how we do that below.
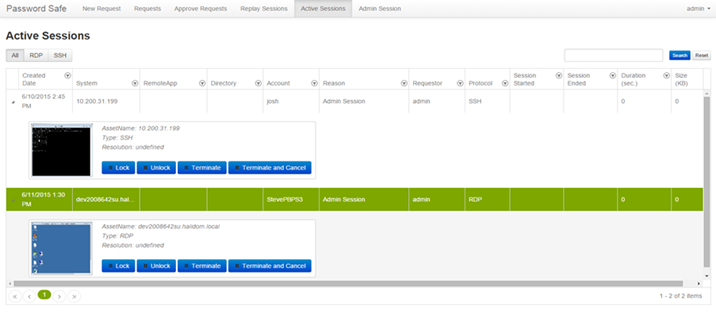 Recording and playing back sessions
The ability to force third parties through a password appliance where all activities are recorded is standard practice. The ability to record and playback the sessions at a later date is also standard. The frequency of the playback can either be using a sampling of the recorded sessions or the playback of the specific sessions depending on the specific activity and criticality of the assets being managed.
Don’t be the next victim
Nothing these breach victims has done to this point was enough. A change in attitude must accompany a change in leadership. Defaulting to a least privilege model with automated password management and privileged session management is the only path forward. When millions of records – and potential victims – is at play you have to assume you’re under constant attack and behave thusly.
If you are interested in taking the next step in maturing your privileged account management deployment, contact us today.
Recording and playing back sessions
The ability to force third parties through a password appliance where all activities are recorded is standard practice. The ability to record and playback the sessions at a later date is also standard. The frequency of the playback can either be using a sampling of the recorded sessions or the playback of the specific sessions depending on the specific activity and criticality of the assets being managed.
Don’t be the next victim
Nothing these breach victims has done to this point was enough. A change in attitude must accompany a change in leadership. Defaulting to a least privilege model with automated password management and privileged session management is the only path forward. When millions of records – and potential victims – is at play you have to assume you’re under constant attack and behave thusly.
If you are interested in taking the next step in maturing your privileged account management deployment, contact us today.

Brad Hibbert,
With over 20 years of experience in product strategy and management, Brad leads BeyondTrust’s solution strategy. He joined BeyondTrust via the company’s acquisition of eEye Digital Security, where Brad led strategy and products. Under Brad’s leadership, eEye launched several market firsts, including vulnerability management solutions for cloud, mobile and virtualization technologies. Prior to eEye, Brad served as Vice President of Strategy and Products at NetPro before its acquisition in 2008 by Quest Software. Formerly, at FastLane Technologies, which was sold to Quest Software in 2001, Brad worked extensively with key Microsoft business units on product direction and go-to-market strategies.








