- BeyondTrust PowerBroker Password Safe management updates: including expanded platform support, plus filtering and API enhancements
- Reporting support for NIST 800-53 Revision 4 and PCI Data Security Standard (DSS) 3.0
- Threat Intelligence Connector for ServiceNow: import BeyondTrust Retina vulnerability data, launch Retina vulnerability scans, and generate incident response tickets in ServiceNow service automation solutions
- Several additional usability and reporting enhancements
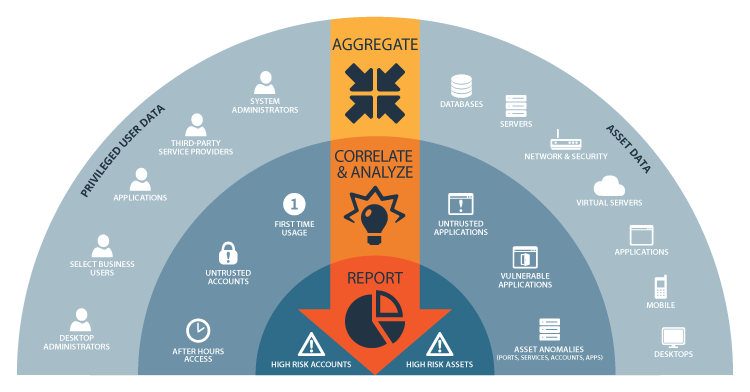 BeyondInsight Clarity correlates and analyzes diverse asset and user data to identify critical threats in your IT environment.[/caption]
Measure: Detect Changes Signaling In-Progress Threats
Examining an asset or user’s current state isn’t always enough to reveal risk, making it critical to constantly measure and compare profile data over time. For instance, today, an asset may be running a seemingly normal set of services. Tomorrow, it might be running a markedly different set of “normal” services, while similar assets remain unchanged. Clarity measures asset characteristics and user behaviors from one day to the next, noting the scope and speed of any changes. By comparing an asset or user’s “change velocity” to that of similar assets or users, Clarity enables you to see deviations that you may have otherwise missed.
Isolate: Spotlight Users and Assets Posing the Greatest Risks
BeyondInsight Clarity is deft at flagging any users or assets that deviate from the norm. Clarity constantly organizes users and assets into like groups based on their profiles and behaviors. Whenever changes occur that cause a specific user or asset to break from the pack, BeyondInsight shines a spotlight on the outlier and offers complete drill-down capabilities to speed investigation and remediation.
Report: Align IT and Security for Smarter Decision Making
BeyondInsight’s powerful reporting engine keeps IT security and IT operations teams aligned and focused on business goals – whether that means complying with industry regulations like PCI and HIPAA or simply reducing the risk profile by employing least privilege where it makes the most sense. With Clarity, BeyondInsight expands its reports library to over 270 templates, with new templates for pinpointing users, assets and activities with high threat levels. As a result, IT operations and security staff can quickly identify and remediate threats, while sharing vital risk and compliance data to both technical- and non-technical audiences within the organization.
Optimize: Increase the Value and ROI of Existing Security Investments
BeyondInsight Clarity adds value to existing security investments by revealing risks normally buried within volumes of data. Clarity collects, correlates and analyzes user and asset activity data from supported privilege and vulnerability management solutions, including:
BeyondInsight Clarity correlates and analyzes diverse asset and user data to identify critical threats in your IT environment.[/caption]
Measure: Detect Changes Signaling In-Progress Threats
Examining an asset or user’s current state isn’t always enough to reveal risk, making it critical to constantly measure and compare profile data over time. For instance, today, an asset may be running a seemingly normal set of services. Tomorrow, it might be running a markedly different set of “normal” services, while similar assets remain unchanged. Clarity measures asset characteristics and user behaviors from one day to the next, noting the scope and speed of any changes. By comparing an asset or user’s “change velocity” to that of similar assets or users, Clarity enables you to see deviations that you may have otherwise missed.
Isolate: Spotlight Users and Assets Posing the Greatest Risks
BeyondInsight Clarity is deft at flagging any users or assets that deviate from the norm. Clarity constantly organizes users and assets into like groups based on their profiles and behaviors. Whenever changes occur that cause a specific user or asset to break from the pack, BeyondInsight shines a spotlight on the outlier and offers complete drill-down capabilities to speed investigation and remediation.
Report: Align IT and Security for Smarter Decision Making
BeyondInsight’s powerful reporting engine keeps IT security and IT operations teams aligned and focused on business goals – whether that means complying with industry regulations like PCI and HIPAA or simply reducing the risk profile by employing least privilege where it makes the most sense. With Clarity, BeyondInsight expands its reports library to over 270 templates, with new templates for pinpointing users, assets and activities with high threat levels. As a result, IT operations and security staff can quickly identify and remediate threats, while sharing vital risk and compliance data to both technical- and non-technical audiences within the organization.
Optimize: Increase the Value and ROI of Existing Security Investments
BeyondInsight Clarity adds value to existing security investments by revealing risks normally buried within volumes of data. Clarity collects, correlates and analyzes user and asset activity data from supported privilege and vulnerability management solutions, including:
- PowerBroker for Windows: user and account activity data from desktops and servers
- PowerBroker for UNIX & Linux: user and account activity from servers
- PowerBroker Endpoint Protection Platform: IPS, IDS, anti-virus and firewall log data
- Retina CS Enterprise Vulnerability Management: vulnerability data
- Third-Party Vulnerability Scanners: imported data from Qualys, Tenable, and Rapid7

Chris Burd,
Chris brings over 20 years of technology sales and marketing experience to BeyondTrust, where he is responsible for corporate communications and digital marketing. Prior to BeyondTrust, Chris led marketing communications at Core Security, where managed the company’s positioning, branding, and inbound marketing initiatives.








