With news breaking on the CIA’s ability to listen in via Smart TVs, many will be alarmed by the breadth of the exploits WikiLeaks has uncovered. The security industry has been warning of the dangers of Internet of Things devices for a long time and just last week, a hack on internet-connected teddy bears was making the headlines.
Some of the best practices used on traditional Windows or Mac systems such as patch management, not logging in as an admin user and controlling what applications can run, are either not implemented or simply don’t exist on these ‘smart’ devices. When devices like these are connected to corporate networks, it is crucial to focus on securing other endpoints as much as possible to limit lateral movement and segregate the environment where possible.
It is clear from these leaked documents that intelligence agencies have not only built their own tools but also borrowed techniques used in malware by cyber criminals. This demonstrates how capable many cyber criminals now are. Once again, tools such as AV have fallen short – they can be easily bypassed or disabled entirely. In one case, they cite that “heuristic detection can be avoided by renaming the .exe to a common installer name such as setup.exe” and in others, they detail tricks to disable AV entirely.
Figure 1 https://wikileaks.org/ciav7p1/...
All too often attackers can easily launch unknown applications, exploit user privileges and remain undetected in a network. With the leak detailing numerous zero day vulnerabilities and ways to evade detection, it is now more important than ever to look at what proactive measures can be taken to reduce the attack surface of your endpoints. Endpoints are where the code executes and where the data is accessed from, so we must build our defences from the endpoint out.
One important thing to note is how frequently the techniques are exploiting admin accounts, using a variety of approaches to silently bypass the Windows UAC prompt and leverage the user’s privilege. As shown in the 2016 Microsoft Vulnerability Report, admin accounts represent a huge threat to any organisation and removing them will significantly reduce the risk of attack.
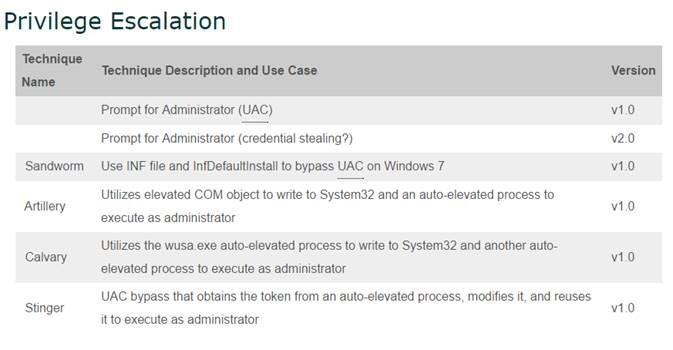
Figure 2 https://wikileaks.org/ciav7p1/...
Since the Snowdon revelations, there has been increased focus on secure communications -from projects like LetsEncrypt to secure website traffic to end to end encryption in messaging apps. This has caused both intelligence agencies and cyber criminals to renew their efforts in targeting endpoints to access data before it is encrypted and transmitted. This means that more than ever security strategies should start with protecting the endpoint.
When it comes to security in 2017 we need to assume the worst and think like an attacker. It doesn’t matter if the attacker is a nation state or a cyber criminal, the best defence is to reduce the attack surface as much as possible using layers of proactive defence.
Take a look at your endpoints from an attackers perspective, what could an attacker do if they exploited an application or convinced a user to run something? Once you’ve done this, think about what could be done to reduce this risk. Organisations who think like this are able to greatly reduce their risk and stay ahead of threats far more effectively.

James Maude, Field Chief Technology Officer
James Maude is the Field Chief Technology Officer (FCTO) at BeyondTrust. With his broad experience in security research, both in academia and industry, James has spent the past decade analyzing cyber threats to identify attack vectors and trends in the evolving security landscape. He is an active member of the security community and hosts Adventures of Alice and Bob, a podcast that shines a light on the people making a difference in security. As an expert voice on cybersecurity, he regularly presents at international events and hosts webinars to discuss threats and defense strategies.








