What is Cyber Threat Intelligence?
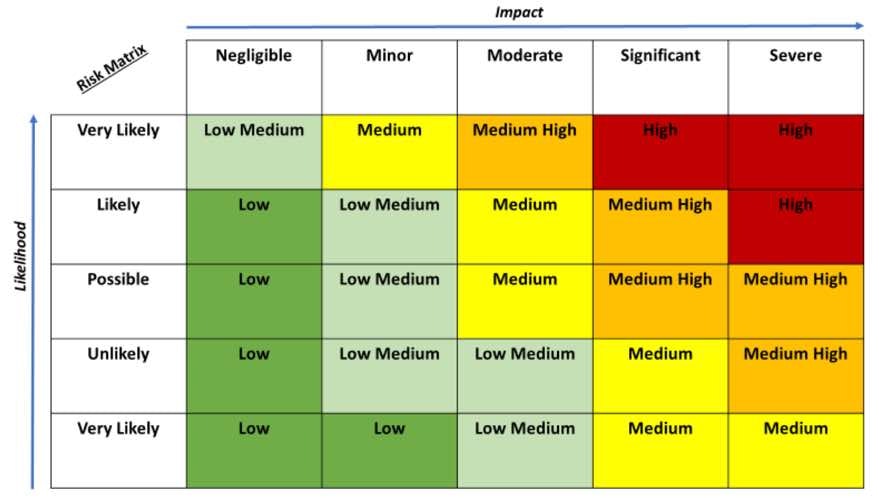
Cyber threat intelligence is more than just a data feed of user behavior, real-time threats in the wild, active exploits, and temporal data. It gains the highest value when it is merged with relevant information from your organization to provide a profile of the risk and threat; much like the sample risk matrix Impact versus Likelihood. Cyber threat Intelligence helps define the Likelihood in the matrix based on activity in the wild and within other organizations, while traditional non-tangible measurements define the Impact.
Performing a Risk Assessment
Whenever an organization performs a risk assessment, they try to consider multiple variables based on the user, asset, resource, location, and many non-tangible criteria like hardening, exploits, vulnerabilities, risk surface, exposure and mission. A complete risk assessment model is a daunting task to manually complete if you consider all the possible vectors and methodologies to actually quantify the risk. In general, risk assessments start with a simple model (as illustrated below) and each vector gets documented and a risk outcome assigned. When we are dealing with multiple risk vectors, the results can be averaged, summed, weighted, or used with other models to produce a final risk score. From a vendor perspective, many of these technologies are proprietary and even patented.
Why Automation is Essential
To make this process efficient and reliable, automation and the minimization of human interaction is of primary concern. Anytime human judgement is applied to a risk vector, the potential for deviations in the results is higher due to basic human opinions and errors. This implies that risk assessment models benefit the most when reliable and consistent data is readily available for interpretation verses just a user discretion.
The Role of Standards
When documenting risks for cybersecurity, the industry has several well-known standards for many of these vectors, including:
- Common Vulnerabilities and Exposure (CVE) – a standard for information security vulnerability names and descriptions
- Common Vulnerability Scoring System (CVSS) – a mathematical system for scoring the risk of information technology vulnerabilities
- Common Weakness Enumeration Specification (CWE) - provides a common language of discourse for discussing, finding and dealing with the causes of software security vulnerabilities as they are found in code
- Common Configuration Scoring System (CCSS) - a set of measures of the severity of software security configuration issues. CCSS is a derivation of CVSS.
Shortcomings of Standard Scoring Mechanisms
Unfortunately, these only focus on the non-tangible aspects of cybersecurity. They very loosely consider user behavior, exploits, and threat intelligence as a part of their risk assessment. In addition, the tangible aspects like physical location and user behavior do not quantify well in these models due to environment factors and time-based parameters like working hours, vacations, and age of the data.
For example, an application may have a vulnerability. It may have a CVSS score and have a security patch from the manufacturer, but the risk score is consistent when communicating the score. Tangible aspects like application usage, age of the vulnerability, exploits in the wild, companies or verticals being attacked, etc. all represent Cyber Threat Intelligence and are a dynamic risk assessment model that must be considered as a part of your risk assessment in order to truly understand the threat.
As an example, consider the recent WannaCry outbreak based on EternalBlue and DoublePulsar. It represented the highest and most extreme risk from a vulnerability and exploit perspective. That was true from day one and is still true today. However, without Cyber threat Intelligence there is no gauge to understand if the actual threat to the organization is the same today as when it was propagating through corporate networks several weeks ago. The risk is the same (vulnerability score), but the actual threat is lower due to the kill switch discovered and implemented on the Internet. Traditional vulnerability assessment solutions do not take this into consideration and still provide the same score.
Cyber Threat Intelligence Data
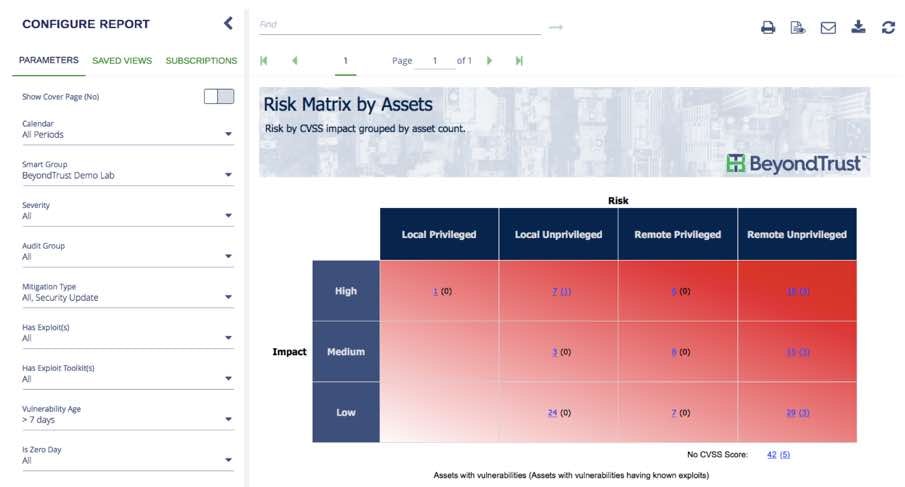
The BeyondTrust platform provides a vehicle to merge cyber threat intelligence data with well-established methods for application, user, and operating system risk assessments. It can calculate the risk of vulnerable applications, application usage (user behavior), and threat intelligence (exploits) in easy to use heat maps and charts. This provides a perspective over time, based on real-world problems and the threats your users and assets face as they use information technology to perform their daily business tasks. The screen shot below illustrates this mapping. It contains assets, exploits, and the temporal parameters to decide the highest risk (and threat) information for assets in your organization.
For more information on BeyondTrust’s solutions to mitigate cybersecurity risks, contact us today. Our cybersecurity solutions are designed to understand the threats and risk your organization faces and provide real world cyber threat intelligence to make smart decisions.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.









