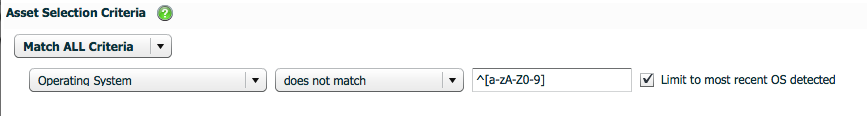
With the introduction of Retina CS 4.5 and PBW 6.0, PBW can receive policy from Active Directory Group Policy (GPO Based) or the Retina CS Threat Management Console. Policy from Retina CS is assigned via a Smart Rule / Smart Group. In order to have a PBW agent dynamically change policy based on location (IP Address), simply add the Address Group to the Asset Selection Criteria.
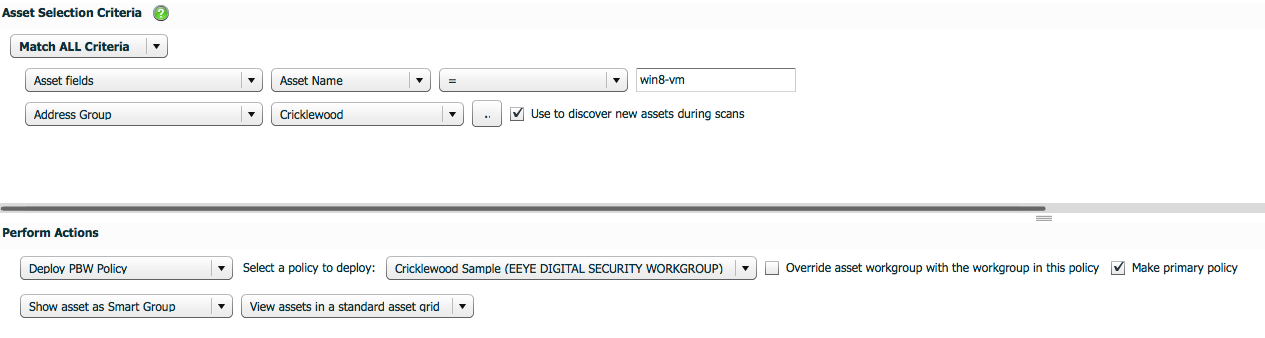
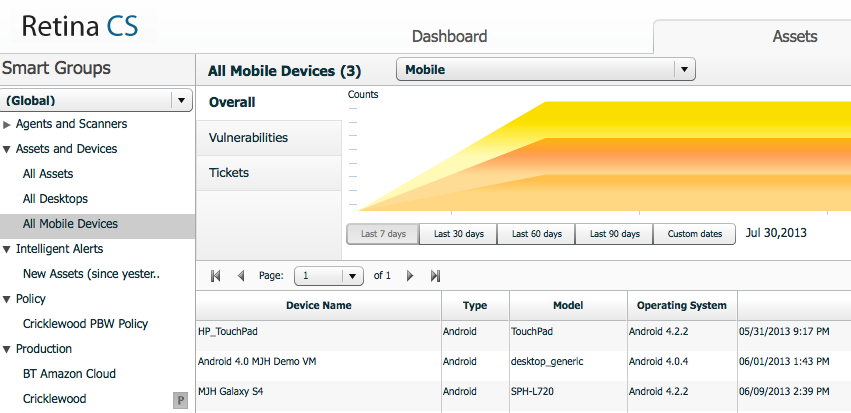
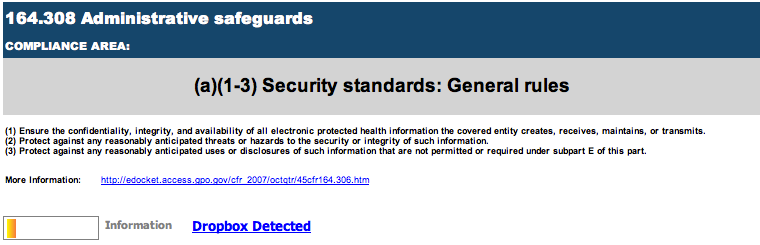
One of the coolest tips for the solution is that these Assets are stored just like every other Asset and can be used against every report in the system just like a Server or Workstation; including common regulatory reports like HIPAA and PCI. All an administrator needs to do is Run a Report on Existing Data against a mobile Smart Group and the results will appear just like any other Asset in the System. Below is a snippet from a HIPAA report against these Android devices:
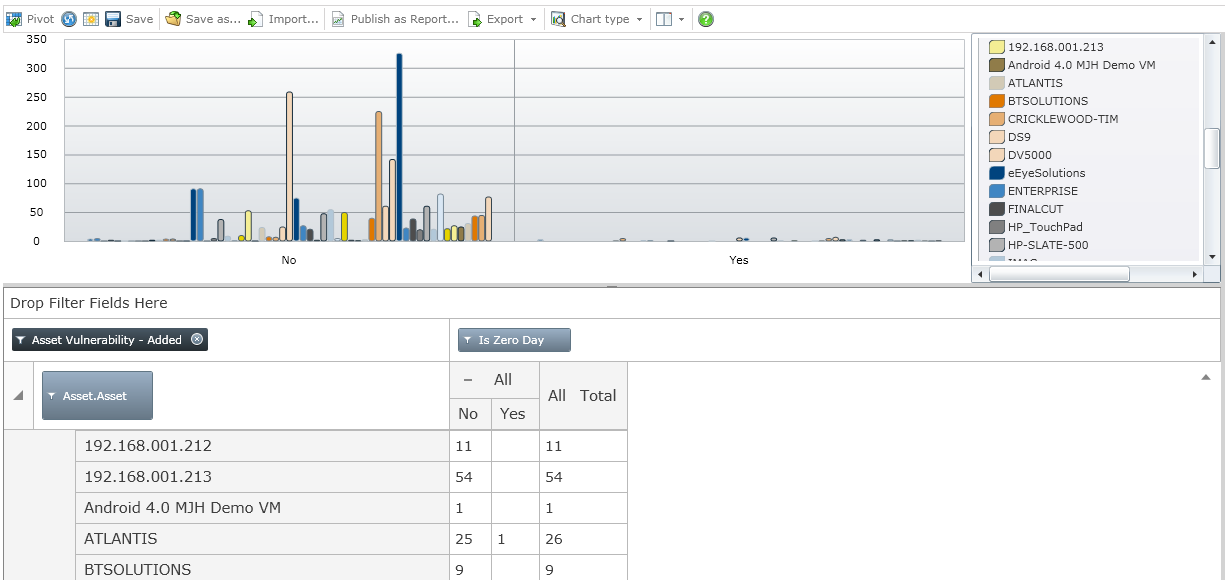
#5 – Retina Insight Pivot Grid
If you have seen a pre-sales demonstration of our technology, you have probably seen the Retina Insight Pivot Grid. This component of the technology allows users to build customized reports when none of the over 260+ canned reports meet their needs. Administrators can open the Pivot Grid and drag and drop Measures and Metrics for almost all of the data collected by Retina CS to create custom reports. Below is a sample of Assets and Vulnerabilities mapped to the presence of Zero-Day Vulnerabilities.
If you have found any other tips and tricks in your travels, please comment below. We would like to hear from you.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








