 Editors note: This is the third of three use case blogs that describe how a BeyondTrust-orchestrated cyber defense can prevent or minimize an attack. To illustrate, we’ll use specific use cases available in the Verizon Data Breach Digest (full report). Read the first use case on State Actors Targeting Critical Infrastructure and the second on Connecting Threat Data to Minimize Payment Card Fraud.
Editors note: This is the third of three use case blogs that describe how a BeyondTrust-orchestrated cyber defense can prevent or minimize an attack. To illustrate, we’ll use specific use cases available in the Verizon Data Breach Digest (full report). Read the first use case on State Actors Targeting Critical Infrastructure and the second on Connecting Threat Data to Minimize Payment Card Fraud.
From the Data Breach Summary:
What do pirates on the high-seas have to do with securing web servers and content management systems (CMS)? It seems as though cybercrime is not isolated to the digital world any longer, as old world, Blackbeard-type pirates turn to the web for information that will make their physical attacks more targeted and lucrative.
A global shipping conglomerate unfortunately experienced this new reality firsthand. It wasn’t the fact that pirates commandeered one of their cargo vessels, and stole valuable merchandise, but instead it was the precision in which they carried out the theft –the pirates knew exactly what they were looking for and precisely where to find it.
An investigation into the shipping company’s systems revealed that pirates exploited existing vulnerabilities within the shipper’s server to successfully upload a malicious web shell onto a server that was managing shipping routes. This enabled the threat actors to download detailed bills of lading that identified desired valuables, their associated crate numbers, and the ships that would transport them.
How an Orchestrated Cyber Defense can Minimize Risks Like This
Want to take your vulnerability management game to the next level? Download our latest white paper, Change the Game in Vulnerability Management, Download now
To help prevent or minimize risks associated with similar attacks, BeyondTrust recommends an integrated security approach that includes BeyondTrust and 3rd party solutions.
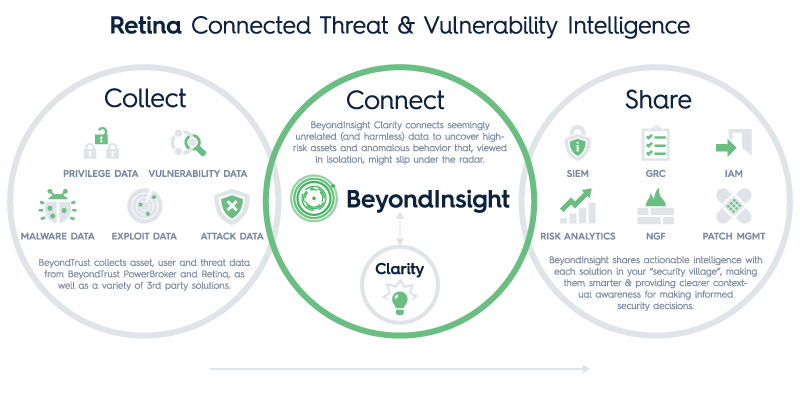
Technologies Integrated:
- Asset Management
- Workflow Management & Ticketing
- Patch Management
- Windows Least Privilege
- Vulnerability Management
A simple first step would have been for the Shipper to close its web server vulnerabilities via a continuous vulnerability management program using an enterprise solution like BeyondTrust Retina. To gain a holistic view of their assets the shipper could have imported detailed asset data from ServiceNow into the Retina database.
Once all of the assets had been enumerated and scanned for vulnerabilities, the Shipper could have streamlined the patching of these vulnerabilities with Retina’s direct integration with Microsoft’s WSUS and SCCM. Given the number of errors committed by these actors, closing these soft targets and raising the barrier to entry to something more challenging may have exceeded their skill level and served as a deterrent.
To ensure easy attack vectors were eliminated, Retina could have been connected to BMC Remedy or ServiceNow workflow management and ticketing systems, to enable the traceability of remediation tickets as well as to request on-demand vulnerability scans, to verify closed vulnerabilities.
Finally, since it’s not practical to close all vulnerabilities, Retina’s tight integration with BeyondTrust PowerBroker for Windows, would have allowed the Shipper to limit the scope of an attack by controlling access to applications based on their known vulnerabilities.
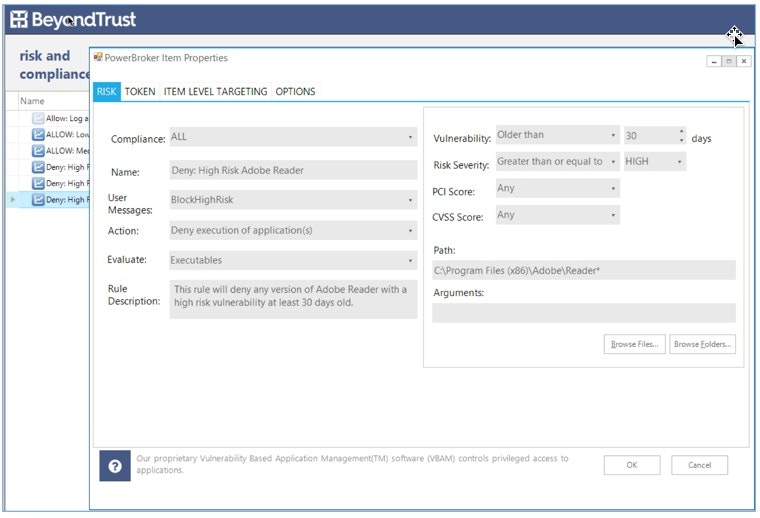 PowerBroker for Windows: Vulnerability Based Application Management (VBAM)
PowerBroker for Windows: Vulnerability Based Application Management (VBAM)
It’s Time to Change the Game!
By mobilizing our “security villages” (yes you have one), and automating their interactions, we can collect data from a variety of trusted sources, correlate it into a clear picture of risk, and take swift and decisive actions to mitigate vulnerabilities and threats. That’s how we flip the game on our adversaries and take control of vulnerabilities that have been plaguing us for more than a decade.
Want to take your vulnerability management game to the next level? Download our latest white paper, Change the Game in Vulnerability Management, for more attack scenarios and to discover how orchestrating your cyber defenses can keep you steps ahead of the bad guys.
For more, contact us today!

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








