 Editors note: This is the second of three use case blogs that describe how a BeyondTrust-orchestrated cyber defense can prevent or minimize an attack. To illustrate, we’ll use specific use cases available in the Verizon Data Breach Digest (full report). Read the first use case on State Actors Targeting Critical Infrastructure.
Editors note: This is the second of three use case blogs that describe how a BeyondTrust-orchestrated cyber defense can prevent or minimize an attack. To illustrate, we’ll use specific use cases available in the Verizon Data Breach Digest (full report). Read the first use case on State Actors Targeting Critical Infrastructure.
From the Data Breach Summary:
A strange pattern of escalating payment card fraud prompted a cyber insurance carrier to begin investigating one of its own clients – an oil and gas company – which owned and operated a chain of retail service stations, referred to as "Dixie Boys Truck Stop” (DBTS). A thorough inspection of both network and terminal data yielded no evidence of an external attack. And, with no malware discovered and no proof of card skimming at the cash registers or fuel pumps, investigators quickly turned their attention to possible insiders.
In an attempt to catch the bad guys in the act, investigators implemented keystroke loggers, file integrity monitoring, and playback recording of remote support sessions. Within a matter of days, the traps paid off and investigators were alerted to suspicious activity coming from DBTS’ IT and POS support vendor.
In the end, the investigation team’s efforts uncovered that one of the support vendor’s helpdesk staff was perpetrating the fraud. By modifying a configuration file, the perpetrator was able to capture clear text authorization requests from each fuel pump – including enough mag-stripe data to conduct fraudulent transactions – and all while using his boss’ computer to cover his tracks.
Want to take your vulnerability management game to the next level? Download our latest white paper, Change the Game in Vulnerability Management, Download now
How an Orchestrated Cyber Defense can Minimize Risks Like This
To help prevent or minimize risks associated with similar attacks, BeyondTrust recommends an integrated security approach that includes BeyondTrust and 3rd party solutions.
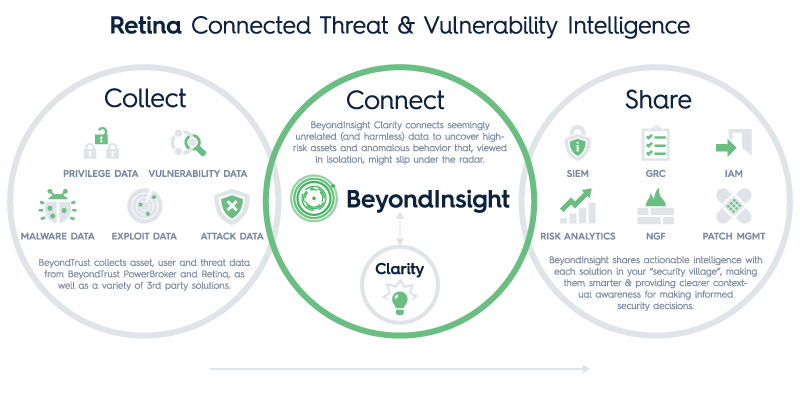
Technologies Integrated:
- Server Least Privilege
- Windows Least Privilege
- SIEM
- Vulnerability Management
- Password Management
For starters, if DBTS had implemented a password management solution, such as BeyondTrust PowerBroker Password Safe, on their payment processing server, the contractor would have had to request access, and by doing so, would not have been able to “sneak” onto the server unnoticed. Auto-onboarding of sensitive accounts into PowerBroker is made easy with the help of an integrated asset scanning engine like BeyondTrust Retina.
Even if granted access, the attacker would not have been able to perform the system-level changes required without administrator privileges, which should have been locked down by a least privilege solution like BeyondTrust PowerBroker for Windows or PowerBroker Unix Linux.
Moreover, the attacker’s aberrant behaviors including requesting access afterhours, altering the system clock, and querying individual fuel pumps should have added up to spell big trouble. An integrated threat analytics engine like BeyondTrust Clarity would have correlated separate events from PowerBroker and Retina, and alerted authorities early in the kill chain.
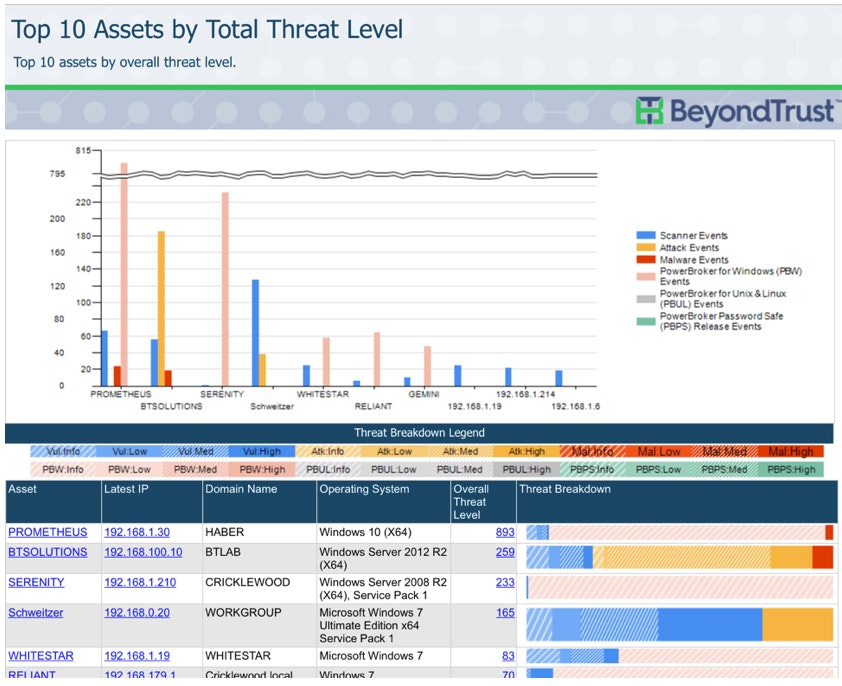 BeyondInsight Clarity: Top 10 Assets by Threat Level
BeyondInsight Clarity: Top 10 Assets by Threat Level
Finally, Clarity’s normalized event data could have been shared via certified connectors with a DBTS SIEM. This actionable intelligence would have raised the level of awareness of this emerging and ongoing threat.
It’s Time to Change the Game!
By mobilizing our “security villages” (yes you have one), and automating their interactions, we can collect data from a variety of trusted sources, correlate it into a clear picture of risk, and take swift and decisive actions to mitigate vulnerabilities and threats. That’s how we flip the game on our adversaries and take control of vulnerabilities that have been plaguing us for more than a decade.
Want to take your vulnerability management game to the next level? Download our latest white paper, Change the Game in Vulnerability Management, for more attack scenarios and to discover how orchestrating your cyber defenses can keep you steps ahead of the bad guys.
For more, contact us today!

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








