
With nearly 30 billion connected devices set to be deployed worldwide by 2020, IoT adoption is growing rapidly as organizations better understand the value of the data, telemetry, and the improved control and communications that these devices can offer for themselves and their customers. However, sometimes growth can outpace processes, leading to gaps that can leave these devices open to exploit.
How secure is your IoT environment? Download the white paper, written by Rob Black, CISSP, and Fractional CISO, and learn how to tackle IoT security by managing identities and privileges.
It wasn’t just the Mirai botnet that brought this to light – there have been several other IoT-related exploits and breaches reminding us that security can’t be an afterthought for manufacturers—or for customers. And, when it comes to industrial IoT (IIoT), the stakes are even higher. Unfortunately, the Internet of Things is increasingly living up to the more cynical appellation it’s been given: the Insecurity of Things!
In April 2018, BeyondTrust asked cybersecurity and IT leaders around the world about their IoT adoption plans and the risks associated with those plans. (You can read the full report from the study’s June publication here.) The study generated useful insights for helping customers lay out a roadmap for deliveringenterprise-level IoT security. Let’s look at what we learned and how it can help you.
Enterprise IoT Adoption
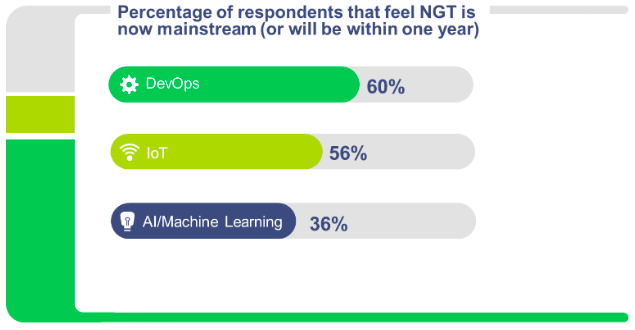
Respondents to our Implications of Using PAM to Enable Next-Generation Technologies survey indicated that 56 percent of customers believe IoT is now mainstream, and 40% say that IoT will have a somewhat to extremely large impact on their organizations.
What Are the Risks of IoT Adoption?
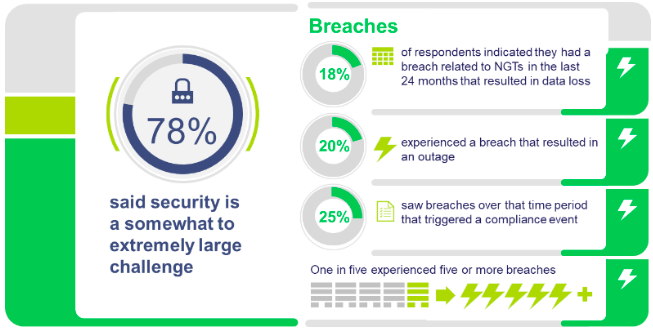
78% of our study respondents said that security was a somewhat to an extremely large challenge to adoption of next-generation technologies such as IoT. Drilling in a little deeper shows us that lack of visibility into sanctioned and shadow IoT devices, weak configurations, default or common passwords, unencrypted traffic, and excessive privileges are the culprits here.
The question becomes: How can organizations secure IoT devices to take advantage of new business opportunities, while leveraging the same solutions to address risks across the rest of their environment?
IoT Security Best Practices
We devised several best practices you can take to improve the control and visibility over your IoT devices. If you’re one of those 56% of companies where IoT has gone mainstream, take a look at your environment and determine how you measure up to these practices.
IoT Security Best Practice 1: Perform a discovery and inventory of IoT devices
Performing continuous discovery and inventory of IoT devices ensures that only approved assets are available and used in your environment. After all, you can’t manage what you can’t measure, and you can’t measure what you don’t see! Start with our free Retina IoT (RIoT) Scanner. It will help you identify high-risk IoT devices and safely check for default or hard-coded passwords. Reporting is a snap, and there’s no installation required. You have no excuse NOT to use this free scanner just to give you a baseline.
IoT Security Best Practice 2: Scan for vulnerabilities and misconfigurations
Once IoT devices are found and managed, continuous vulnerability assessment and remediation must be performed, as well as continuous configuration and hardening baseline scanning. While these resources are hardened to prevent security breaches and are inherently resilient to network-based vulnerability assessment scans, host-based security scanning provides a deep inspection into an instance and can report back any vulnerability or configuration anomalies. A best practice is to provision the agent as a part of the instance template to ensure the asset is secured and remains un-tampered with during its lifecycle. This is especially important for devices in an ICS/SCADA environment.
Having this capability reduces risk, ensures that no IoT devices are left unmanaged (even without network scanning), and ensures configurations are consistent and properly hardened against best practices from NIST, CIS, and Microsoft.
IoT Security Best Practice 3: Eliminate shared and embedded privileged accounts
Controlling and auditing access to shared device accounts ensures that all privileged activity is associated with a unique identity and ensures that all passwords are properly managed and rotated across IoT devices. Shared accounts are only part of the problem, though. Removing hard-coded passwords in scripts and files, and those embedded passwords that may interact with IoT devices should be prioritized. Embedded application credentials represent open backdoors to critical systems.
Securely storing privileged account credentials, requiring a simple workflow process for check-out, and monitoring privileged sessions limits lateral movement in the case of a compromise and provides a secure audit trail for forensic purposes.
IoT Security Best Practice 4: Segment networks
Group devices into logical units that do not trust one another to reduce the “line of sight” access that attackers have into internal systems. For access that needs to cross the trust zones, utilize a secured jump server with multi-factor authentication, adaptive access authorization, and session monitoring. Segment access based on the context of the user, role, application, and data being requested.
IoT Security Best Practice 5: Privilege management when agents aren’t possible
Network devices are critical for organizations to function, yet present especially ripe targets for external attackers and malicious insiders if not properly monitored. To improve security on these devices, organizations must have granular control and detailed auditing of privileged user activity—but some network devices present a challenge to using traditional agent-based solutions. Simple command block listing doesn’t offer enough granularity to prevent unwanted commands from being run. And, most tools provide only minimal functionality and work only on a limited number of devices. Proxy-based command control and auditing monitors for commands that could indicate lateral movement, and provides a secure audit trail for digital forensic purposes. And, of course, end-user privileges should be limited in the first place!
BeyondTrust Can Help with IoT Security
The BeyondTrust solution for securing IoT devices discovers all devices in the environment, groups devices for consistent privilege management, and scans for security vulnerabilities and privilege-related risks. By unifying policy, management, reporting, and analytics across the environment, organizations can meet stringent security and compliance controls over IoT usage, while achieving business goals.
[caption id="attachment_26614" align="alignnone" width="706"]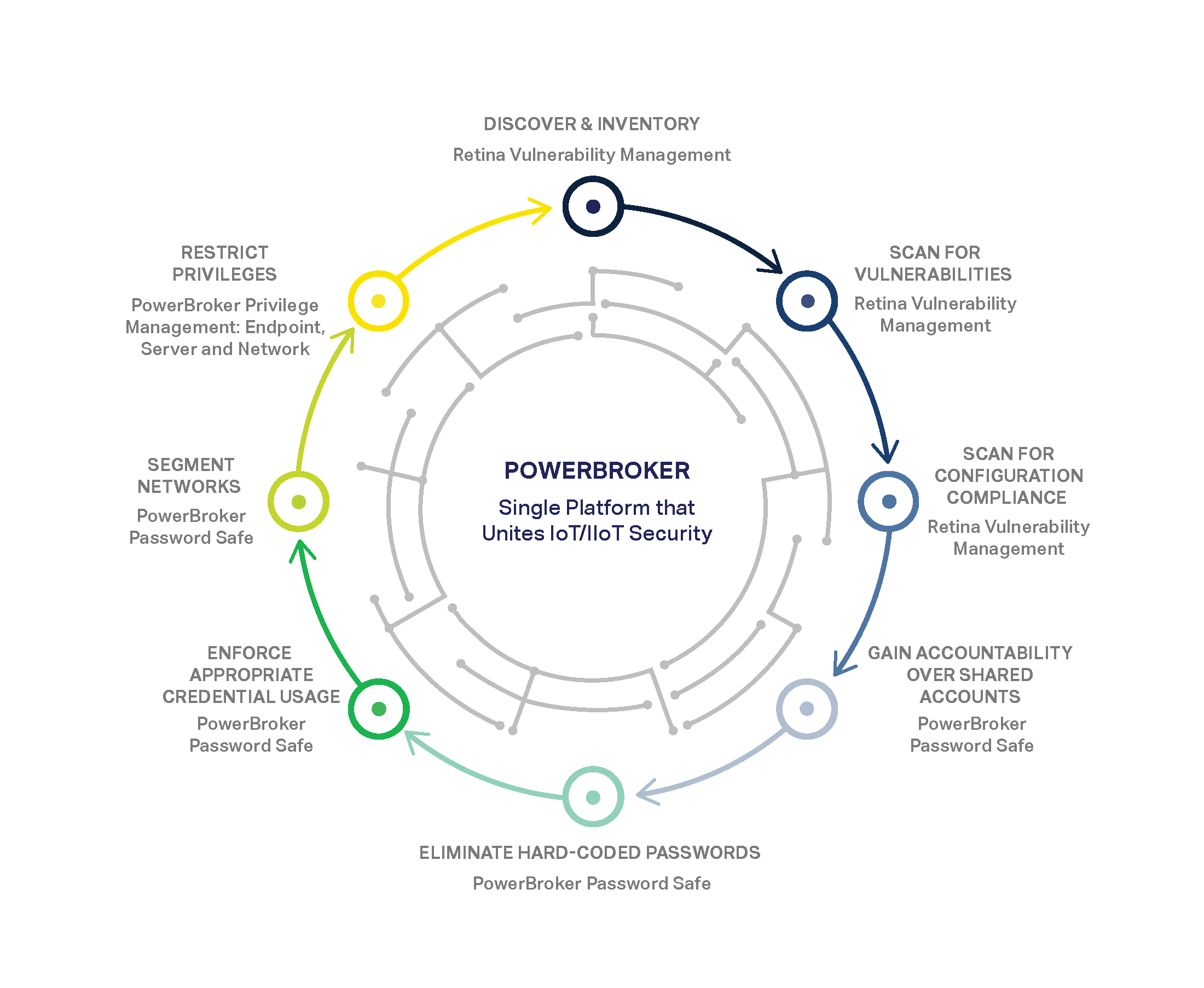 BeyondTrust’s proven 8-step best practices approach to securing IoT devices.
BeyondTrust’s proven 8-step best practices approach to securing IoT devices.
For more information on how BeyondTrust can help you accelerate your business transformation to IoT through the power of Privileged Access Management, contact us today.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








