
I’m pleased to announce the 6.5 release of Retina Network Security Scanner, our solution for scanning, prioritizing and remediating vulnerabilities across the enterprise. This release significantly enhances BeyondTrust’s support for DevOps use cases by adding new scanning and reporting capabilities for Docker images, as well expanded host scanning capabilities. For these and other features, keep reading!
Docker Image Scanning Improves Security
As organizations continue to automate development pipelines to increase their agility and responsiveness to business needs, container-based technologies such as Docker are used to provide DevOps teams everything they need to build, test, run and deploy applications. However, many organizations struggle to know how many Docker instances are in their environments, causing potentially risky gaps in security. To overcome these risks, organizations must have the ability to quickly discover all Docker images in their environments and report on their attributes.
Retina Network Security Scanner version 6.5 introduces new scanning capabilities against Docker containerization technology. With these new capabilities, organizations can quickly discover and accurately enumerate the attributes of images (like software, packages, etc.).
Retina customers have two options:
- Performing network-based scans against both Linux and Windows hosts running Docker, with administrative credentials required; or
- Retina Host Security Scanner performing on-node scans against Windows hosts running Docker, with no credentials required.
Please see the summary table of capabilities by platform below.
| Docker Images on Linux | Docker Images on Windows |
| Basic Image data, OS Identification and Exposed Ports, Repository Tag, Image ID and where available, Image Size, Creation Date and Image Author Enumerations: Software, Users and User Group Software package auditing of Debian-based images (e.g. Ubuntu), Red Hat-based images (e.g. CentOS, Oracle Linux), Gentoo and Alpine images | Basic Image data, OS Identification and Exposed Ports, Repository Tag, Image ID and where available, Image Size, Creation Date and Image Author Enumerations: Software, Services and Users Registry and file auditing |
This new capability means that organizations can improve the control and visibility of Docker container usage, helping to support the further automation of DevOps processes.
New Docker Image Reporting Reduces Risks
Version 6.5 also introduces reporting for vulnerabilities and attributes (enumerations) of Docker images. Customers have the option to include vulnerability details about the associated host which provides greater visibility into the risk not only posed by the images but also on the host on which the images reside. For a representation of this reporting, please see the screenshot below.
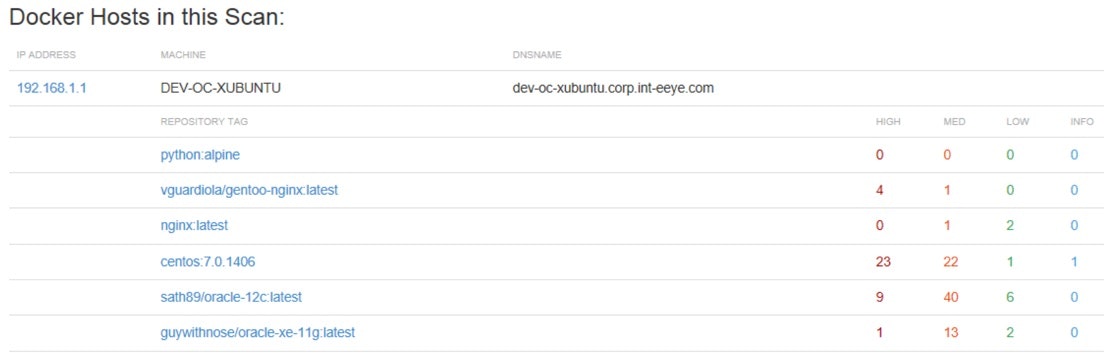
Watch for central management, scanning, normalization and reporting of Docker images in the forthcoming release of Retina CS/BeyondInsight.
Expanded Linux and Mac Platform Support
For many organizations, it can be complex and time-consuming to identify and scan remote Linux and Mac user computers, transient virtual platforms, hardened systems and cloud environments. Further complicating scanning is the need to perform fully authenticated vulnerability scans without the need to pass credentials, and to do it in a matter of minutes! Organizations must have host security scanning that supports Linux and Mac platforms.
With the latest release of the Retina Host Security Scanner, BeyondTrust has expanded platform coverage in beta to include several distros of Linux and Mac, including:
- Debian 8 (x64)
- Debian 9 (x64)
- macOS 10.12.x
- Oracle Enterprise Linux 7.x (x64)
- Red Hat Enterprise Linux 7.x (x64)
- Ubuntu 14.x
- Ubuntu 16.x
This enhanced capability will help organizations reduce their security risks by centrally reporting on and analyzing all host-based scan data.
Additional CIS Benchmark Certification
While previous versions of Retina have supported Security Content Automation Protocol (SCAP) benchmark assessments – along with CIS, DISA, Microsoft, and more – Retina 6.5 adds support for and certification of the following SCAP benchmarks released by the Central for Internet Security:
- CIS Benchmark for Microsoft Windows 10, v1.3.0, Level 1 Profile
- CIS Benchmark for Microsoft Windows 10, v1.3.0, Level 1 + BitLocker Profile
- CIS Benchmark for Microsoft Windows 10, v1.3.0, Level 2 Profile
- CIS Benchmark for Microsoft Windows 10, v1.3.0, Level 2 + BitLocker Profile
- CIS Windows 10 Release 1607 Benchmark v1.2.0
- CIS Windows 10 Release 1703 Benchmark v1.3.0
For more on this exciting release, please check out the new features document.

Alejandro DaCosta, Product Manager
As Product Manager, Alex DaCosta is responsible for designing the company’s Vulnerability Management solutions. Alex joined BeyondTrust via the company’s acquisition of eEye Digital Security, where he held senior positions as Security Engineer in both pre and post sales operations. As a Senior Security Engineer, Alex was responsible for the success of demonstrating, architecting and implementing the Company’s enterprise solutions. Alex graduated from California State University, Long Beach with a Bachelors of Science Degree in Management Information Systems.








