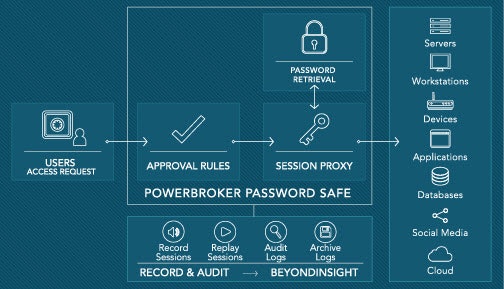
 There are several more enhancements and new features in this release of PowerBroker Password Safe – including live session monitoring and active-active infrastructure support for high-availability deployments. Check out the new features document for a complete rundown, and if you would like to learn more about PowerBroker Password Safe, let us know!
There are several more enhancements and new features in this release of PowerBroker Password Safe – including live session monitoring and active-active infrastructure support for high-availability deployments. Check out the new features document for a complete rundown, and if you would like to learn more about PowerBroker Password Safe, let us know!

Martin Cannard,
Martin has been helping organizations solve challenges in the privileged account management and identity and access management space for over 24 years. At Dell Software, Martin managed a team of Solution Architects, focused on designing and implementing solutions in the Privileged Account Management (PAM) space. Prior to joining Dell, Martin was Sr. Product Manager for Novell Privileged User Manager, a privilege management application acquired from Fortefi, an organization where he served as Vice President, Corporate Development. Prior to this, he was Program Manager of Client Technologies at Symantec where he was responsible for many ground-breaking field and channel enablement applications. Additionally, Martin managed the European QA group at Axent Technologies and has held various management positions in consulting, systems development, and operations. Martin is a regular speaker for security events, and webinars.








