
Security and IT leaders walk a fine line everyday between protecting their organization’s critical data to ensure business continuity, and enabling users and administrators to be productive. Dial up security? Frustration goes up. Dial down security? Then you're the next security breach headline.
But why does it have to be a binary decision? Three limitations. First, security leaders and their IT counterparts often have to patch together multiple different point solutions that address only part of the problem, but this just leads to more cost and complexity. Next, good intelligence is often missing, causing challenges in meeting the needs of multiple different stakeholders – from security to operations to compliance auditors. And finally, the last thing security and IT leaders need is another point tool. Real partnerships are often lacking.
BeyondTrust commissioned a study of our customer base in early 2015 to determine how we are different from other alternatives in the market. What we learned was that there were six key differentiators that separate BeyondTrust from other solution providers in the market. We call it the PowerBroker difference, and in the next five weeks we will explore each of those differentiators in detail. Each of these differentiators address the big problems of what gets in the way of protecting data and enabling users: Patching together multiple solutions, a lack of good reporting, and shallow point tools. Up first: Flexibility.
Differentiator #1: Flexible Deployment Options
How important is deployment flexibility to your organization? Not every organization can deploy a closed appliance-based environment for their privileged account management solution, especially in cases where IT security may be outsourced to a partner. Therefore, many organizations demand the flexibility to deploy PAM solutions as physical or virtual appliances, as software only, or a hybrid. What really matters, however, is that you deploy a PAM solution that covers your entire environment, not leaving any gaps.
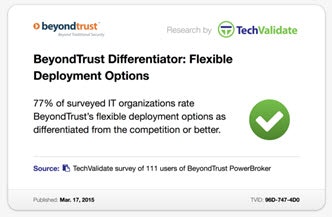
In a survey of more than 100 customers, those customers indicated that BeyondTrust’s deployment flexibility was a competitive differentiator versus other options in the privileged account management market.
This differentiator was important to Know-How s.r.l, an Italian systems integrator looking to secure and automate the process of managing and cycling privileged passwords, eliminate sharing, remove local admin rights from users, and elevate privileges only when needed. They turned to BeyondTrust. In the words of Claudio Montanari, Chief Information Officer, “With BeyondTrust’s PowerBroker there is no other option available that provides such robust choices.”
The PowerBroker privileged account management products can be licensed separately, or unified under the free BeyondInsight IT Risk Management platform used for central policy management, event aggregation, session playback, analytics and reporting. Products are delivered as software, as hardened or virtual appliances, or a hybrid. All products are integrated with the BeyondInsight console providing maximum deployment flexibility.
Interested in learning more about how PowerBroker can meet the flexibility requirements of your privileged account management project? Contact us today. If you are interested in learning more about all of the PowerBroker differences, check out the free white paper.
Author: Scott Lang | Senior Director, Product Marketing

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








