 We’ve all seen the news. Federal agencies from the NSA to the IRS are being compromised by cyber criminals at an alarming rate. What’s going on? Why does this continue to happen? BeyondTrust recently commissioned a survey of senior Federal IT managers to find out.
We’ve all seen the news. Federal agencies from the NSA to the IRS are being compromised by cyber criminals at an alarming rate. What’s going on? Why does this continue to happen? BeyondTrust recently commissioned a survey of senior Federal IT managers to find out.
Federal IT Forecast: Old and Risky with a High Chance for Breach
In the Federal Cybersecurity Threat Survey, we found ample examples of aging infrastructure. Truly antiquated technology is still in use more often than you might think. A surprising 27% of respondents reported that paper tape is still in use in their organizations. 11% still have systems using floppy disks. 47% are still using Windows XP.81% of federal IT managers say aging infrastructure is concern with cybersecurity. Get this report and discover what to do when you can't modernize fast enough. GET THE REPORTWhy would agencies continue to use these outdated systems? 69% report that the concern over losing critical data in the conversion process makes the risk of modernization greater than the reward. On the flipside of that coin, an overwhelming majority of Federal IT managers (81%) say aging IT infrastructures have a somewhat to extremely large impact on their cybersecurity risk. Which risk is greater? The challenge of modernization or the very high risk of breach?
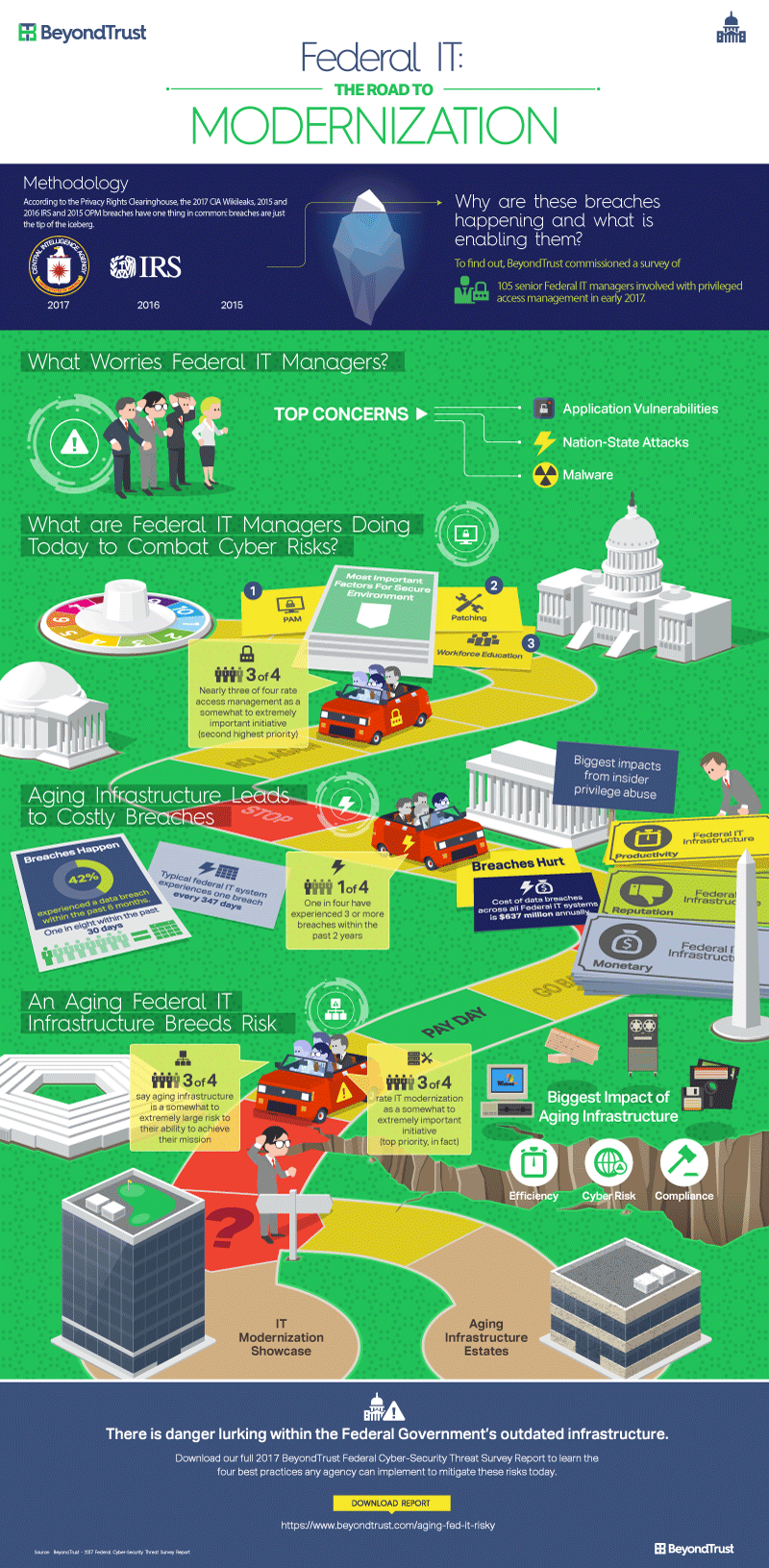
Federal IT Managers are Concerned about Antiquated Infrastructure
If you are a federal IT pro, this problem is no surprise to you or your peers. Modernization across the next 24 months is the top priority of survey participants. Unfortunately, three out of every four survey respondents report that modernization is hindered because “things take longer than expected”. Replacement of these legacy systems quickly is not a realistic probability. So, the threat of breach remains.How to Address the Risk Today
Implementing modern security practices in aging systems is tough. Although federal IT managers report that practices like privileged access management and vulnerability management are most important to securing their environments, they also report that many are not employing best practices in these areas. This puts critical federal agency information and systems at a very high risk for breach. In the Federal CyberSecurity Threat Survey Report, there are four recommendations that agencies can put in place today to dramatically mitigate risk in federal legacy environments. These strategies will still be best practices when modern systems come on line.- Manage privileged credentials with greater discipline, eliminate admin rights and enforce least privilege
- Isolate legacy systems to reduce attack surfaces
- Improve the maturity of vulnerability management through automated patching
- Unite threat intelligence from multiple sources to better prioritize risks across the environment
Embed Infographic on Your Website
<a href="https://www.beyondtrust.com/resources/white-paper/federal-cybersecurity-threat-survey-report/"><img src="/assets/images/bt/infographic-federal-cyber-threat-survey-800.png" alt="Federal Cybersecurity Threat Survey Report" width="400px" border="0"; /></a><span>Please include attribution to BeyondTrust with this graphic.</span>
Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








