Malware is a certainty for most of us in the IT security community. Chances are your organization experiences new malware events by the second – or maybe 5 per second, according to the latest Verizon Data Breach Investigation Report. It’s therefore no surprise that just about every security incident has a malware component behind it.
To help our customers tackle the malware juggernaut, we’re unveiling new malware analysis capabilities as part of BeyondInsight version 5.5. For those of you just getting up to speed, BeyondInsight is our centralized management, reporting and analytics platform. It’s included with several of our privilege management and vulnerability management solutions, and it allows our products to work together to do some pretty cool stuff – like advanced threat analysis.
Advanced; it’s not marketing fluff
“What’s so ‘advanced’ about your threat analytics,” you ask? I’d start with its ability to make connections among highly diverse data sets to reveal risky users, accounts and assets. This capability (dubbed “Clarity”) correlates user, account and asset behavior; IPS, IDS, AV and firewall log data; and vulnerability data from our solutions and others. The idea is to make associations between security issues and events that otherwise would have been overlooked as blips on your SIEM radar. It spotlights where minor aberrations add up to big problems. You can learn more about BeyondInsight Clarity Threat Analytics in this post.
How malware analysis works in BeyondInsight
BeyondInsight Clarity adds malware analysis to the mix by correlating data on applications, services and processes running in your environment with a cloud-based malware database. The malware database contains a continuously updated compilation of hashes from all major AV vendors. If there’s a match, an alert is reported back to BeyondInsight and associated with the affected system.
The data that’s submitted for malware analysis can come from any or all of the following deployed BeyondTrust solutions:
- PowerBroker for Windows (PBW)
- PowerBroker Endpoint Protection Platform (PBEPP)
- Retina CS Enterprise Vulnerability Management (RCS)
To over-simplify things, it goes a little like this:
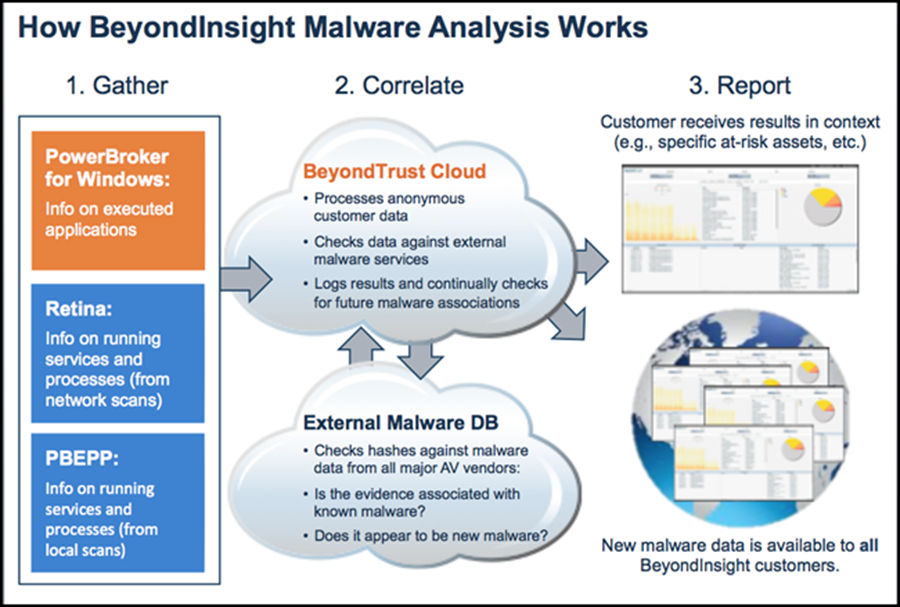
A few key things to point out about the malware analysis process:
1) All data sent to the cloud is totally anonymous. We only send the hashes themselves and validate you a valid user by license key. No system data, no customer data, nothing else.
2) If the hash hasn’t been seen before, the BeyondTrust cloud service will submit it for analysis. If it’s later associated with malware, you will find out about it.
3) The anonymous hash data and associated malware information is available to all customers the first time any other customer, anywhere experiences a new potential threat.
Ready for a quick video demo? I thought so…
Threat analytics beyond malware
It’s important to note that malware analysis is just a piece of the puzzle here. The real power of BeyondInsight Clarity is to factor potential malware alerts in with other environmental data for a better-informed view of risk. For instance, Smart Rules rules can alert when an asset:
a) has an overall risk rating of 7 or above,
b) has a combination of browser vulnerabilities; and,
c) has applications being launched as administrator that may have malware associated with them.
By correlating malware evidence with information about suspicious user and asset behavior, BeyondInsight equips you to quickly flag advanced persistent threats and other hidden risks that may have otherwise been lost in the security data “noise.”
Want to know more? We have an in-depth paper on this called, “BeyondInsight Clarity Tech Brief: How It Works.” Ask a BeyondTrust rep for a copy.
“But wait, there’s more!” Three more reasons to like BeyondInsight 5.5
In the spirit Ron Popeil, I can’t let you go without telling about three other new features in BeyondInsight 5.5:
1) Clarity Threat Analytics Support for PowerBroker Password Safe: BeyondInsight now supports data feeds from PowerBroker Password Safe, which enables the patent-pending Clarity Threat Analytics engine to analyze privileged password, user and account behavior.
2) New Third-Party Connectors: BeyondInsight doesn’t have to live in a vacuum. In fact, it’s design to share information with any solution that can benefit from privileged account management and/or vulnerability assessment data. Version 5.5 adds next-gen Syslog and SNMP connectors to share data with solutions for SIEM, GRC, help desk, inventory management and more.
3) New File Integrity Monitoring Reports: PowerBroker Endpoint Protection Platform and PowerBroker for Windows collects detailed file system monitoring activity and transmits the results to BeyondInsight. The reports depict file activity patterns, trends, usage and variations over long periods of time.
We’ll stop at these three, but there is indeed more good stuff in BeyondInsight 5.5. Read more in the new features overview.
Done with reading about BeyondInsight and ready to see it? Request a demo.

Chris Burd,
Chris brings over 20 years of technology sales and marketing experience to BeyondTrust, where he is responsible for corporate communications and digital marketing. Prior to BeyondTrust, Chris led marketing communications at Core Security, where managed the company’s positioning, branding, and inbound marketing initiatives.








