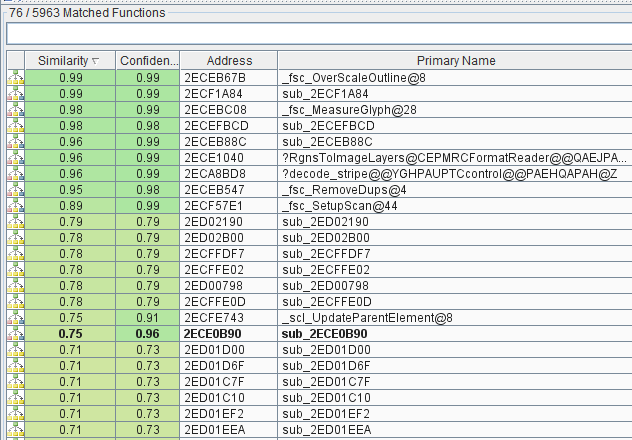
 The diff is ugly, many functions have changed and a few have been added/removed. So where do we go from here? Looking at the individual changes, we come across a few fixes that look security related, but after numerous dead-ends, one is more attractive than the rest – sub_2ECE0B90. A high level view of this function is seen below.
The diff is ugly, many functions have changed and a few have been added/removed. So where do we go from here? Looking at the individual changes, we come across a few fixes that look security related, but after numerous dead-ends, one is more attractive than the rest – sub_2ECE0B90. A high level view of this function is seen below.
 This function is somewhat big and has quite a few changes, but is interesting for a couple reasons:
First off, apart from some structural changes, there are several calls to memcpy in the unpatched function. Only one of these has been converted to a memcpy_s in the patched function, the count of which is now passed in as an argument to the function.
This function is somewhat big and has quite a few changes, but is interesting for a couple reasons:
First off, apart from some structural changes, there are several calls to memcpy in the unpatched function. Only one of these has been converted to a memcpy_s in the patched function, the count of which is now passed in as an argument to the function.
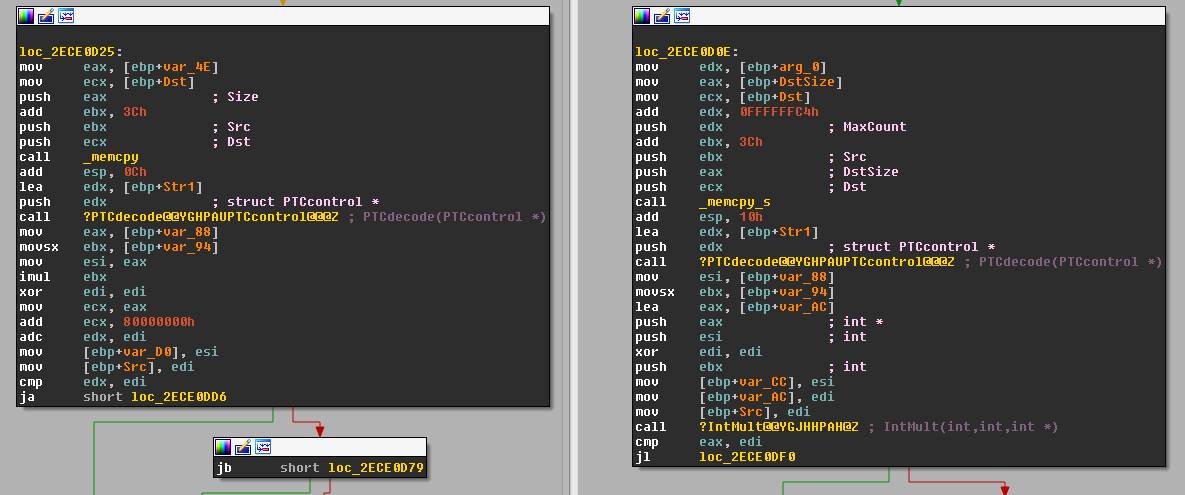 Secondly, the function looks like it contains some kind of magic value at the top. In the very first basic block, further processing is determined by a call to strncmp, searching for the string “PTC+MSHM”. Perhaps this could be a useful marker for which to search.
Secondly, the function looks like it contains some kind of magic value at the top. In the very first basic block, further processing is determined by a call to strncmp, searching for the string “PTC+MSHM”. Perhaps this could be a useful marker for which to search.
 Assuming that this string is in fact a marker for a path to the vulnerable function we perform a quick Google search.
Assuming that this string is in fact a marker for a path to the vulnerable function we perform a quick Google search.
 After digging around on archive-ro.com, we end up with a link to a journal file:
Popping this guy open in a hex editor, we get dozens of hits for PTC+MSHM on a free text search
After digging around on archive-ro.com, we end up with a link to a journal file:
Popping this guy open in a hex editor, we get dozens of hits for PTC+MSHM on a free text search
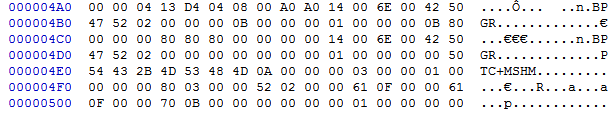 We now proceed dynamically, attempting to trigger a breakpoint in the affected function. We set one in the first block of the function of the unpatched DLL near the call to strncmp on “PTC+MSHM”. Upon hitting it the first time it, the str1 argument looks like this:
We now proceed dynamically, attempting to trigger a breakpoint in the affected function. We set one in the first block of the function of the unpatched DLL near the call to strncmp on “PTC+MSHM”. Upon hitting it the first time it, the str1 argument looks like this:
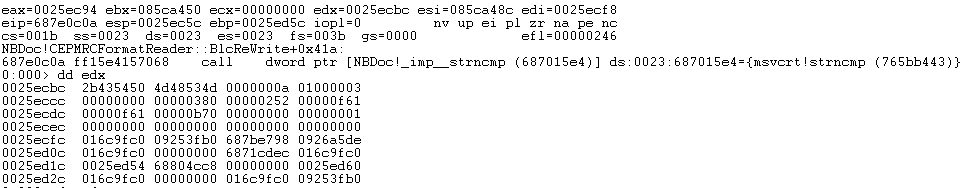 Grabbing all the bytes up till the second occurrence of 0f61 and flipping the endian, we get two hits in our hex editor, one at offset 0x04df and one at offset 0x2bcb.
Grabbing all the bytes up till the second occurrence of 0f61 and flipping the endian, we get two hits in our hex editor, one at offset 0x04df and one at offset 0x2bcb.
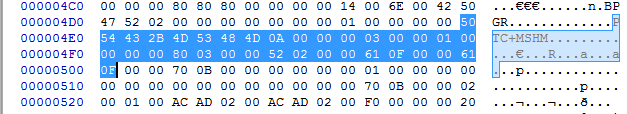 The second hit is different from the dump, lacking the next word 0b70. So it looks like we are handling this blob at offset 0x04df in the file during the first function call.
Continuing on, we set a breakpoint above the memcpy of interest at the top of the block. After some stepping we get to this situation:
The second hit is different from the dump, lacking the next word 0b70. So it looks like we are handling this blob at offset 0x04df in the file during the first function call.
Continuing on, we set a breakpoint above the memcpy of interest at the top of the block. After some stepping we get to this situation:
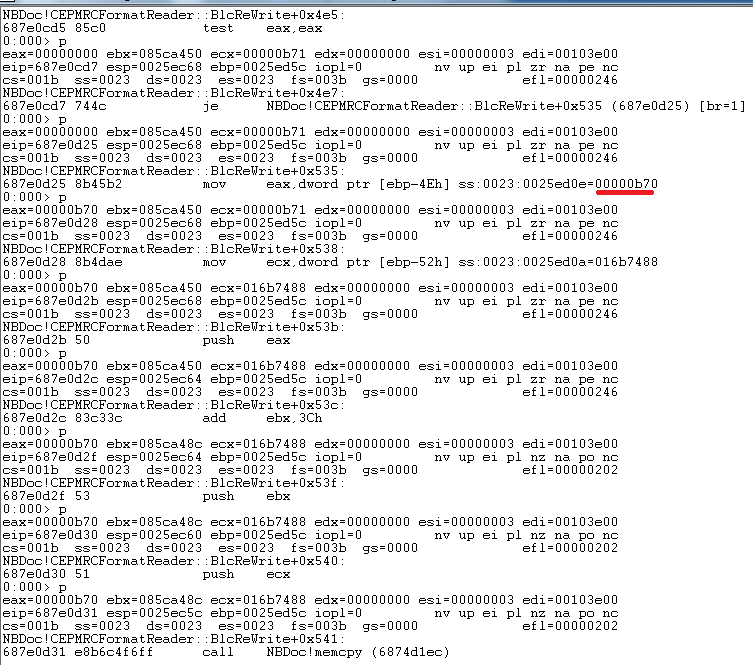 Well, that 0x0b70 looks familiar… Furtermore, it appears to be pushed as the size parameter to the memcpy. Let's modify the initial file, changing 700B to FFFF.
Well, that 0x0b70 looks familiar… Furtermore, it appears to be pushed as the size parameter to the memcpy. Let's modify the initial file, changing 700B to FFFF.
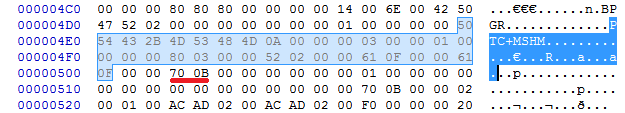 Restarting the application and opening our modified file, we receive an access violation.
Restarting the application and opening our modified file, we receive an access violation.
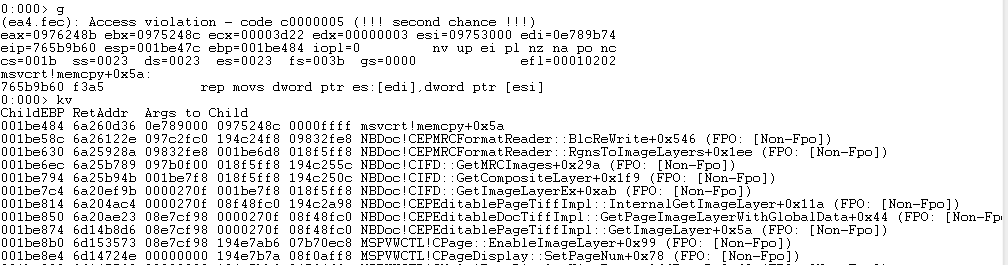 So as hoped, we crash in the memcpy and have exercised the vulnerable code. More than this particular vulnerability we are trying to isolate, this crash seems like it may be more indicative of less audited code then, say, MS Word.
With visions of unbounded memcpy’s in our eyes, we fired a dumb fuzzer at the current version of Journal – and as expected it fell over pretty quickly and in several unique ways -- we encourage you to do the same.
So as hoped, we crash in the memcpy and have exercised the vulnerable code. More than this particular vulnerability we are trying to isolate, this crash seems like it may be more indicative of less audited code then, say, MS Word.
With visions of unbounded memcpy’s in our eyes, we fired a dumb fuzzer at the current version of Journal – and as expected it fell over pretty quickly and in several unique ways -- we encourage you to do the same.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








