Cloud privileged access management (PAM) has become more central to security architectures, as cybersecurity teams shift to adapt to pandemic-accelerated digital transformation.
As explored in my recent Why Cloud PAM Matters webinar, essential capabilities for cloud PAM include: enabling just-in-time (JIT) privileged access, cloud-native hosting, privileged task automation, and service account management.

Cloud Privileged Access Management: 5 Success Factors
The universe of IT privileges required to operate in a hybrid, multi-cloud environment is expanding. Yet, many organizations struggle to extend PAM into their cloud. Gaps have included limited cloud identity and access management (IAM) Integration, poor visibility, use of static or always-on privileged accounts (i.e. standing privileged access), and reliance on heavy server-side PAM agent software.
Here are five keys for building a strong foundation for PAM in the cloud:
1. Just-in-Time (JT) Access
JIT privileged access differs from traditional privileged access because it is OFF by default. Only when a user needs privileged access, and can get it approved through a business rule or workflow process, does the IAM or PAM system turn on the access by triggering an IT permission or calling a system API. JIT access greatly reduces standing privileges and the privileged user attack surface on-premise, in the cloud, and wherever it’s used.
2. Cloud-Native Hosting
PAM is vital for protection against cyberattackers in several ways—from gaining an initial foothold, to moving laterally and escalating privilege. However, poorly implemented controls around privileged access can also interrupt or slow down critical production IT work.
For PAM to work well in the cloud, it must have broad SaaS provider coverage and deep IaaS integration. Just as agility and scalability are two of the cloud’s main business benefits, PAM must work seamlessly with cloud security, management, and network processes so as not to interfere with normal IT operations.
3. PAM Must be Part of DevSecOps
IT operations in the cloud center around DevOps and continuous integration and continuous delivery/deployment (CI/CD) processes. IT teams must bake DevOps security steps, like static or dynamic code analysis, into the CI/CD pipeline. PAM capabilities – such as secrets or credential checkout and interactive session control and recording – must be part of DevSecOps. To do that, they must deliver seamless operations and administration and gain IT user and/or developer acceptance.
4. Privileged Task Automation
In the DevOps world, traditional PAM tends to be too slow for automated processes like CI/CD. We need privileged task automation to fully bake PAM into DevSecOps. DevSecOps teams can make PAM part of the release pipeline automation via two families of use cases, and two integration points as shown in the figure below.
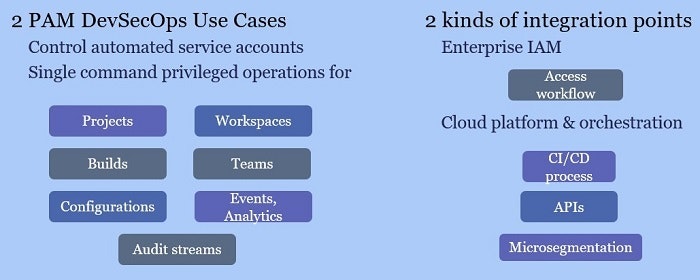
Cloud-native hosting, or integration, is also helpful for PAM in DevSecOps. Customers that consume PAM itself as a SaaS service get the benefit of the vendor’s partnerships or integration with key cloud service providers.
5. Service Account Management
The final piece of the cloud PAM puzzle to fully bring privileged access security into the DevSecOps model is service account management. PAM solutions can discover service accounts, remove hardcoded/embedded credentials, offer API support for credential management, enforce credential quality, and manage secrets for DevOps pipeline orchestration processes.
Customers should start managing privileged service accounts by first developing standards to classify and name the accounts. Consider managing the accounts through a PAM system. Focus on the highest-risk service accounts and/or the ones that are part of applications which integrate in a turnkey manner with your PAM solution.
Privileged Access Security Designed for the Cloud
Be aware of the need and opportunity to implement PAM differently in the cloud. It must support cloud native functionality, privileged task automation, JIT access, and service account automation. Begin evolving cloud PAM soon to avoid the greater risk of perpetuating systemic vulnerabilities from cloud gaps with traditional PAM (or a lack of PAM).
Understand the following practical considerations: Many of the IAM and/or CI/CD orchestration technologies underlying PAM in the DevSecOps world are still maturing. Work closely with IT teams per the DevSecOps model. Craft a phased approach, define a 6-12-month minimal viable product (MVP) target, and get started.
For more insights, check out my webinar: The Expanding Universe of Privileges: Why Cloud PAM Matters

Dan Blum, Cybersecurity Strategist and Author
Dan Blum is an internationally recognized strategist in cybersecurity and risk management. He was a Golden Quill Award winning VP and Distinguished Analyst at Gartner, Inc., has served as the security leader for several startups and consulting companies, and has advised 100s of large corporations, universities and government organizations. He consults with clients on identity management, PAM, risk management, and other topics. He's made his new book Rational Cybersecurity for Business: The Security Leaders' Guide to Business Alignment freely available for Open Access via Apress, or on Amazon.











