
Use Case: State Actors Targeting Critical Infrastructure
Editors note: This is the first of three use case blogs that describe how a BeyondTrust-orchestrated cyber defense can prevent or minimize an attack. To illustrate, we’ll use specific use cases available in the Verizon Data Breach Digest (full report).From The Data Breach Summary:
After an unexplained pattern of valve and duct movements affected both the chemical levels and flow of a regional drinking water supply, Verizon’s RISK team was called in by (who they refer to as) Kemuri Water Company (KWC), to investigate suspicious cyber activity. The initial investigation revealed several concerns; among them, that some of KWC’s internet facing applications contained high-risk vulnerabilities, as well as that several critical IT and operational technology (OT) functions were all run on the same AS/400 server. This single point of failure had direct connections to various networks, ran the water control application, and housed customer PII and billing information. Upon further review, it was determined that threat actors exploited vulnerabilities within KWC’s online customer payment application to steal 2.5 million unique customer records. Worse yet, since the payment application had a direct connection to the AS/400 server, and clear text credentials for that server were discovered on the payment application web server, threat actors now had access to the valve and flow control application.How An Orchestrated Cyber Defense Can Minimize Risks Like This
To help prevent or minimize risks associated with similar attacks, BeyondTrust recommends an integrated security approach that includes BeyondTrust and 3rd party solutions.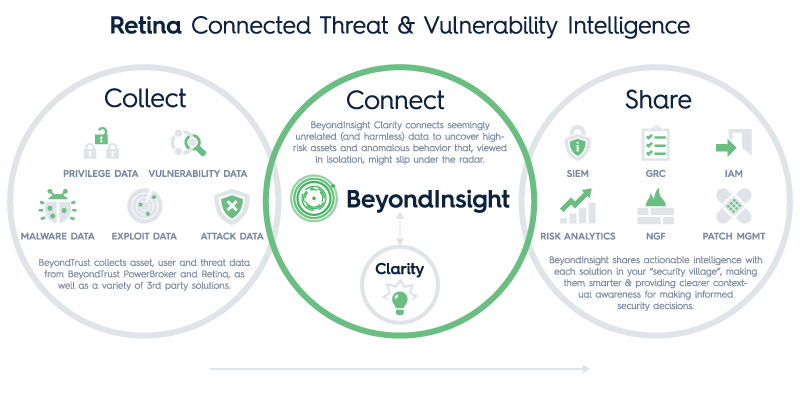 Technologies Integrated:
Technologies Integrated:
- Vulnerability Management
- Exploit Mapping
- Next Generation Firewall
- SIEM
- Password Management
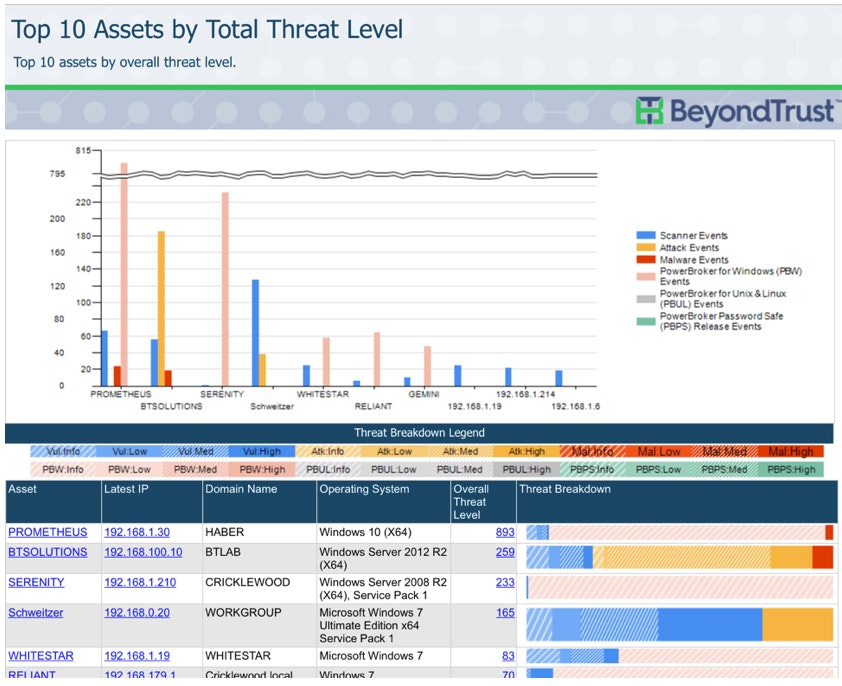 BeyondInsight Clarity: Top 10 Assets by Threat Level
Finally, Clarity’s normalized event data could have been shared via certified connectors with a KWC SIEM. This actionable intelligence would have raised the level of awareness of this emerging and ongoing threat.
BeyondInsight Clarity: Top 10 Assets by Threat Level
Finally, Clarity’s normalized event data could have been shared via certified connectors with a KWC SIEM. This actionable intelligence would have raised the level of awareness of this emerging and ongoing threat.
It’s Time To Change The Game!
By mobilizing our “security villages” (yes you have one), and automating their interactions, we can collect data from a variety of trusted sources, correlate it into a clear picture of risk, and take swift and decisive actions to mitigate vulnerabilities and threats. Connect threat and vulnerability intelligence. That’s how we flip the game on our adversaries and take control of vulnerabilities that have been plaguing us for more than a decade. Want to take your vulnerability management game to the next level? Download our latest white paper, Change the Game in Vulnerability Management, for more attack scenarios and to discover how orchestrating your cyber defenses can keep you steps ahead of the bad guys. For more, contact us today!
Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








