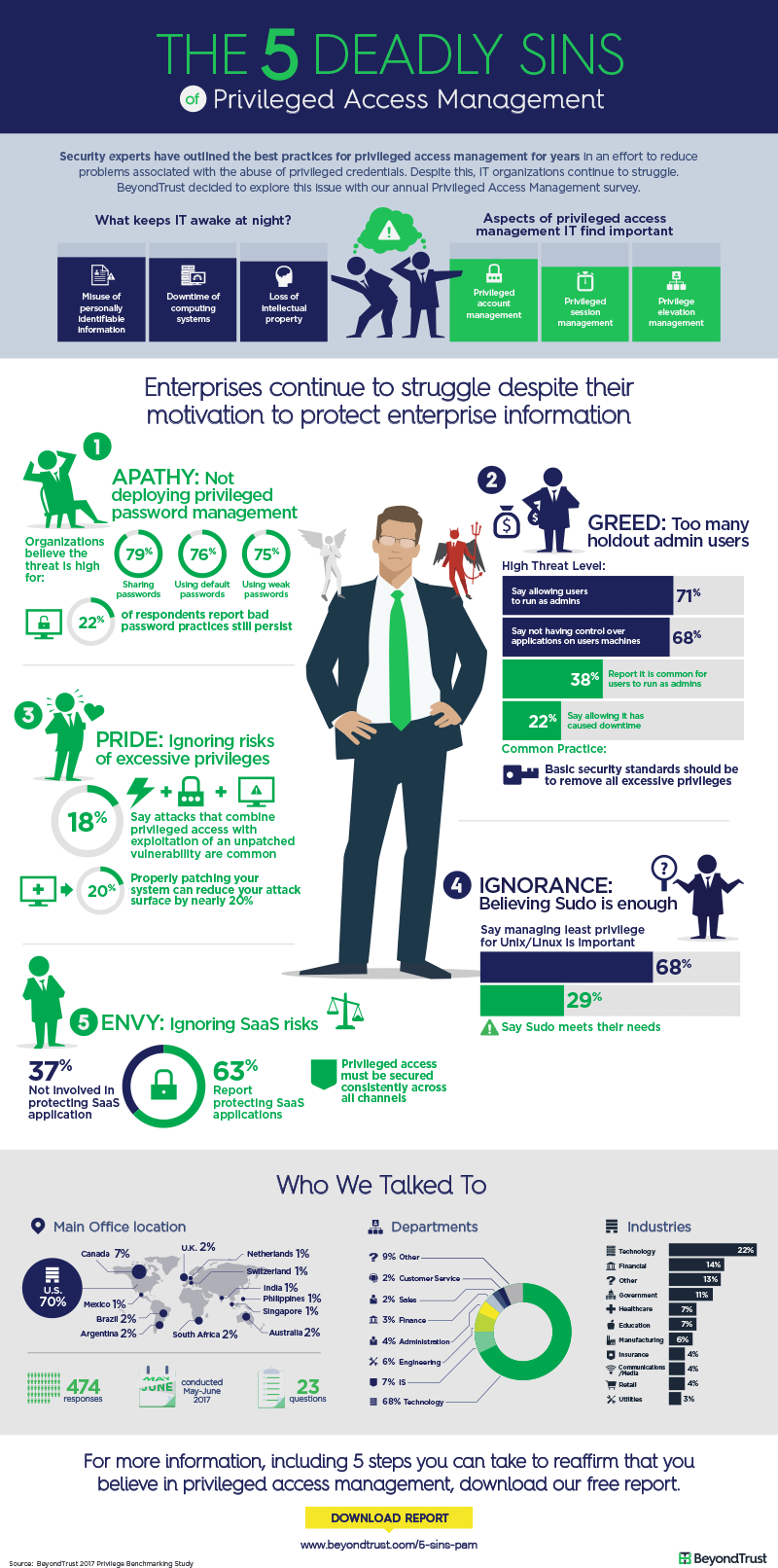
IT organizations still struggle with privileged access management (PAM). How? Enterprise passwords are still not under complete control. Users with admin privileges are running amok. There is untold risk from unpatched system vulnerabilities gone bonkers. SaaS applications lack the same protection as on-premise apps. But, what will it take for organizations to finally – once and for all – address all their privilege risks?
With an aim to answer this very question, we surveyed nearly 500 IT professionals with involvement in privileged access management in May and June 2017. The results were stunning. Before we get there, though, let’s review what organizations are most interested in protecting, and what the consequences are of not having the right privilege controls in place.
Get the full report now: The Five Deadly Sins of Privileged Access Management
Organizations believe it is most important to protect against misuse of personally identifiable information (86%), followed by downtime (85%), and against loss of IP (80%) This shouldn’t come as a surprise as malicious insiders and bad external actors are after what’s most important to you – your organizations’ data.
…and if the data isn’t protected, it can cost you millions
Loss of productivity is the highest (66%) negative impact that organizations have experienced in the last two years in privilege-related attacks. And, since we all know time is money, every security incident related to the abuse and misuse of privileged credentials has the potential to significantly (negatively) impact an organization’s bottom line. By how much? Respondents report that the monetary value of security problems related to privileged access is nearly $4 million per year. This does not include the costs of remediation and potentially new systems and legacy resource replacements.
How did we get here? With sincerest apologies to Chaucer, we hereby present to you the Five Deadly Sins of Privileged Access Management (and some advice on how to atone for them immediately).
The First Deadly Sin: Laziness (or, Not Deploying Privileged Password Management Globally)
Specifically, among password practices, organizations believe that the threat level is highest for users sharing passwords with other users (79%). While organizations are generally well aware of the perils of sharing passwords, a relatively large number of respondents, 22%, report that bad password practices still persist.
The Second Deadly Sin: Greed (or, Too Many Holdout Admin Users)
Let’s reflect on your users for a moment. The practice of allowing users to run as administrators on their machines is recognized by study respondents as the highest threat level (71%) among privilege management malpractices. Although the risk is recognized, an astounding 38% of respondents report that it is still common for users to run as administrators on their machines, and 22% of respondents say this practice has caused downtime! Why do we still allow end users to have administrator rights when it is a basic security commandment to remove all excessive privileges?
The Third Deadly Sin: Pride (or, Ignoring the Link Between Vulnerabilities and Excessive Privileges)
18% of respondents claim that attacks that combine privileged access with the exploitation of an unpatched vulnerability are common. When combined with eliminating local administrator rights on end users’ machines, properly patching system vulnerabilities can close off most of today’s commonly-reported attack vectors – ransomware and others like it – which thrive on system weaknesses and excessive access rights in order to move laterally.
The Fourth Deadly Sin: Ignorance (or, Believing Sudo is Enough to Protect Your Important Unix/Linux Systems and Data)
68% of respondents consider least privilege on Unix/Linux an important PAM function. While 86% of respondents believe their Unix/Linux environments have the highest level of protection, 54% of respondents still run sudo on at least one Unix/Linux server, and 39% still run it on workstations. Respondents report that sudo shortcomings include that is time-consuming, complex, and lacks policy version control and synchronization. More than half – 52% -- are “meh” about it. If sudo were like a restaurant, and that restaurant had a Yelp rating of “meh” would you ever eat there? Nope.
The Fifth Deadly Sin: Envy (or, Not Prioritizing SaaS Applications and the Risks They Introduce)
The cloud? Everybody’s doing it, so why can’t we? A surprising 37% of respondents report that they are not extending protection to SaaS applications. Privileged access must be secured consistently across all channels – on-premise, IaaS, SaaS, PaaS, and through a bunch of other *aaS’s too!
Five Hail Mary’s
Here are five steps you can take today to reclaim your belief in privileged access management:
- Deploy enterprise password management globally across all data centers, virtual and cloud. A centralized password management solution that includes built-in session monitoring will ensure that both important capabilities are met, while providing an automated workflow that makes it easy to use across all accounts and applications.
- Remove local admin rights from ALL Windows and Mac end users immediately. Once all users are standard users, IT teams can elevate a user’s access to specific applications to perform whatever action is necessary as part of their role without elevating the entire user on the machine. The benefit? When the next ransomware variant breaks out, your end users’ machines will be contained, preventing further propagation.
- Prioritize and patch vulnerabilities. Consider the cyber-attack chain. Attackers exploit asset vulnerabilities, hijack elevated privileges, or compromised credentials, and move laterally until they achieve their objective. What’s the first step in that that chain? Right--vulnerabilities. As we mentioned earlier, better prioritization and patching of vulnerabilities gives you boosts your ability to execute smarter privileged delegation decision-making with regards to assets or applications.
- Replace sudo for complete protection of Unix/Linux servers. With pressure on budgets, some organizations may be stuck with sudo, but it doesn’t offer the industrial-strength capabilities that today’s security needs, for example, user behavior analytics, fine-grained policy controls, file integrity monitoring, and more.
- Unify privileged access management – on premise, in the cloud – into a single console for management, policy, reporting, and analytics. As organizations race to adopt *aaS to keep pace with business demands, IT must provide the same level of protection to cloud-based systems as for on premise systems.
BeyondTrust can Help
Want more detail on the five steps, including how to make them work in your enterprise? Download the paper.
For more on how BeyondTrust can help you repent your security sins and be reborn a Privileged Access Management Saint, contact us today!

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.