
This year’s Verizon Data Breach Investigations Report has been published, and as with its prior nine incarnations, the report is packed full of insights (and humorous anecdotes) on the state of data breaches and attack patterns by industry. There’s much to learn from the report, but we’ve summarized our thoughts on the report below. Let me just ask up front…
Why are organizations focusing on the sexy stuff, while seemingly ignoring the basics?
The results in the report (as in the past years) make it exceedingly clear to us that organizations continually ignore the low-hanging fruit – patching, privileged access management, privileged password management, disabling macros in files, network segmentation, multi-factor authentication, etc. – and instead focus so much time, money and resources on breach prevention and remediation following the hot trends of the day. We’ve created this problem ourselves by rewarding the heroes – those who find and fix zero-days, bug bounties, etc. I would contend that we should reward the everyday heroes instead – the ones in the trenches who are patching, reporting and more. If you want real, meaningful improvements in data breach statistics, start there. Let’s look at how the report supports this conclusion.
Insider vs. Outsiders – the balance is shifting
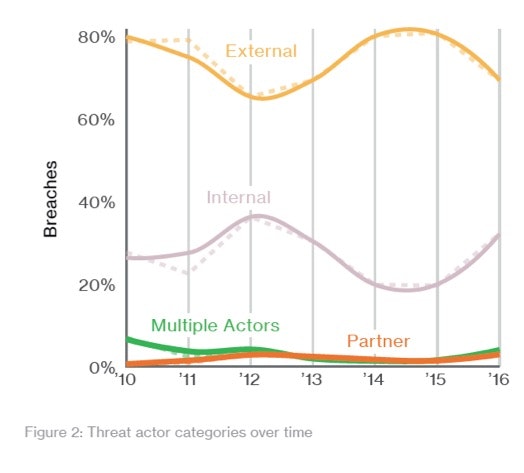 Breaches based on External actors is on the decline (~75% this year), and threats based on Insiders is increasing (~25% this year). While the gap is still wide, the trend has been consistent for the last three years indicating organizations need to more seriously consider the insider threat as an attack vector. Speaking of outsiders, 62% of them used hacking techniques targeting misconfigurations, vulnerabilities, and exploits.
Breaches based on External actors is on the decline (~75% this year), and threats based on Insiders is increasing (~25% this year). While the gap is still wide, the trend has been consistent for the last three years indicating organizations need to more seriously consider the insider threat as an attack vector. Speaking of outsiders, 62% of them used hacking techniques targeting misconfigurations, vulnerabilities, and exploits.
Our recommendations here are straightforward:
- Vulnerability and patch management must mature – and not just to prevent external attackers targeting vulnerable systems, but to mitigate the attack surface of external parties seeking to become insiders by leveraging credentials to move laterally throughout an organization.
- With only 3% of breaches coming from partners, but a whopping 25% including insiders, the evidence is clear: You must get your own house in order first by improving privileged password and privilege management across your environment. Limiting yourself to compliance requirements, or focusing solely administrators and third-parties isn’t enough.
Theft of credentials increasing
The theft of credentials (i.e. usernames and passwords) in 2016 represents a 5x increase verses previous peak years (2012). With potential issues like password re-use a factor, threat actors have easy-to-use methods to exploit personal and business accounts. Further, 81% of breaches leveraging hacking techniques (misconfigurations, vulnerabilities, or exploits) leveraged stolen or weak passwords as a tactic, up from 63% last year! This confirms that privileges are the primary method to conduct a successful attack and that the methods to get them are primarily through hacking techniques.
To combat against this increasingly troubling trend:
- Deploy an enterprise password management solution that discovers every account in the environment, securely stores them, requires an approval process for check-out, monitors activity while checked out, and rotates the credential upon check-in.
- Other alternatives might include instant provisioning – basically having an account created for a specific use. But you must not rely on this approach by itself; it should be part of a multi-layered approach that includes a gateway to the data center, fine-grained privileges to the target machine, multi-factor authentication for the user and more to prevent that one account from being compromised.
- Consider network segmentation or implement a secure enclave that ensures all privileged accounts (employees, contractors, and third parties) do not have direct access to manage devices. This model ensures that only approved devices and restricted network paths can be used to communicate with secured resources.
Privilege misuse – actual data breach losses up 61%!
This year’s report tells us that 14% of breaches were the result of privilege misuse, and it’s taking ever longer to detect the breaches (see a screenshot from the report, emphasis added).
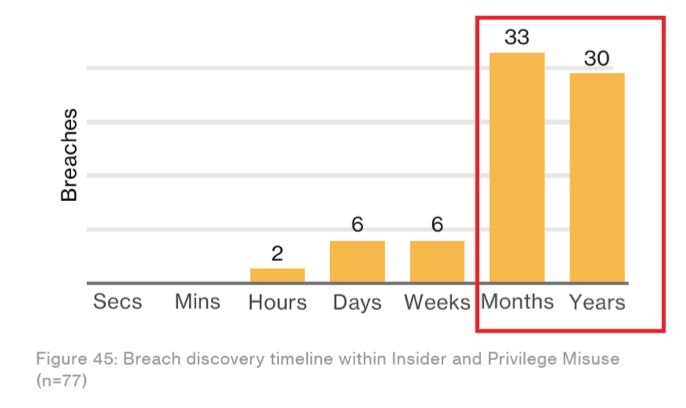
Privilege misuse was the #3 breach pattern, and #2 incident pattern in 2016, and although the number of privilege misuse incidents dropped 26% YOY, the number of confirmed data losses increased by 61% to 277 breaches! What does that mean? Fewer attempts, but greater success. Why could this be the case? Opportunistic targeting? Better disclosure? Regardless, there are basic steps every organization can take to limit this attack surface:
- Enforce least privilege across your entire environment by removing local admin rights from end users, and restricting the use of admin and root account privileges to servers in your datacenter. Elevating rights to applications on an exception basis, and employing fine-grained policy controls once access is granted can quickly limit the lateral movement of would-be attackers.
- Implement a workflow-based process for obtaining privileges. If requests happen during normal business hours and within acceptable parameters, set auto-approval rules to enable access without restricting admin productivity. But, if time, day, or location indicators point to something out of band, deny it and investigate.
Huge increase in ransomware begs for better protections on the endpoint
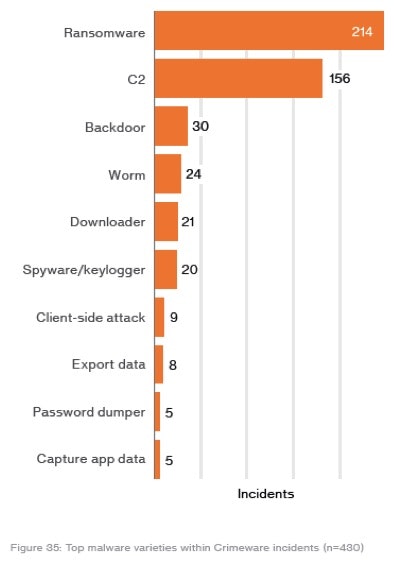
Let me drop a couple of wicked stats on you. First, just look at the figure on the left. 214 incidents involving ransomware. And the other stat: 95% of phishing attacks that led to a breach were followed by some sort of software installation.
These two stats are warning shots for organizations to do a much better job closing attack surfaces on end-user machines. This can be done through multiple mechanisms: least privilege enforcement, application control, disabling macros, limiting an application if it’s not signed by Microsoft, etc.
We’ve written extensively about ransomware, so check that out separately for a very complete list of tactics you can employ to mitigate that threat.
Verticals: Have data? Have money? You’re a target.
The Public Sector, Healthcare, and Financial Institutions saw the largest number of incidents and breaches for insider privilege misuse. Financial had 26 incidents alone. The time for identification took months or years in many cases to identify. The question is not in identifying a vulnerability but whether it gets remediated at all. For Educational Institutions, only 18% of identified vulnerabilities get remediated. For Information based verticals, 97.5% get remediated. This is a huge delta in mindshare and actual vulnerability mitigation efforts. Surprising, Financials are at 33% even though they are the highest targeted vertical in the report. What can be done here?
- Monitor user behavior though event logs, file integrity checks and session monitoring
- Implement session recording for all users that touch PII or financial information
- Utilize fine-grained policy controls for administrators accessing protected systems
- Make privilege elevation decisions based on the risk profile of the target asset
- Clean up old, stale accounts to prevent them from being utilized in an attack
How to be an everyday security hero: Do the basics first
Breaches show no sign of abating. The trends show that insiders are a greater threat. I would contend that chasing after the latest attack trends – which are edge cases – distracts from the everyday blocking and tackling necessary to reduce risk and improve security. That is our advice: Do the basics first well, then you will be in a stronger position to attack the edge cases. Sometimes you must invest in the infrastructure. Now is the time to do that.
For more on BeyondTrust’s privileged access management and vulnerability management solutions, or how we have purpose-built a platform to stop data breaches, contact us today!


Brad Hibbert,
With over 20 years of experience in product strategy and management, Brad leads BeyondTrust’s solution strategy. He joined BeyondTrust via the company’s acquisition of eEye Digital Security, where Brad led strategy and products. Under Brad’s leadership, eEye launched several market firsts, including vulnerability management solutions for cloud, mobile and virtualization technologies. Prior to eEye, Brad served as Vice President of Strategy and Products at NetPro before its acquisition in 2008 by Quest Software. Formerly, at FastLane Technologies, which was sold to Quest Software in 2001, Brad worked extensively with key Microsoft business units on product direction and go-to-market strategies.








