Remote Support Jumpoint Guide: Unattended Access to Computers in a Network
With BeyondTrust Jump Technology, authorized users can securely access and control remote computers, attended and unattended, as well as switches and other network devices in any network. Jump Technology is integral to the BeyondTrust software offerings. All sessions are logged for reporting and auditing. Because BeyondTrust Remote Support is licensed per active representative and not per remote system, Jump Technology is a cost-effective way to reach every device in your enterprise.
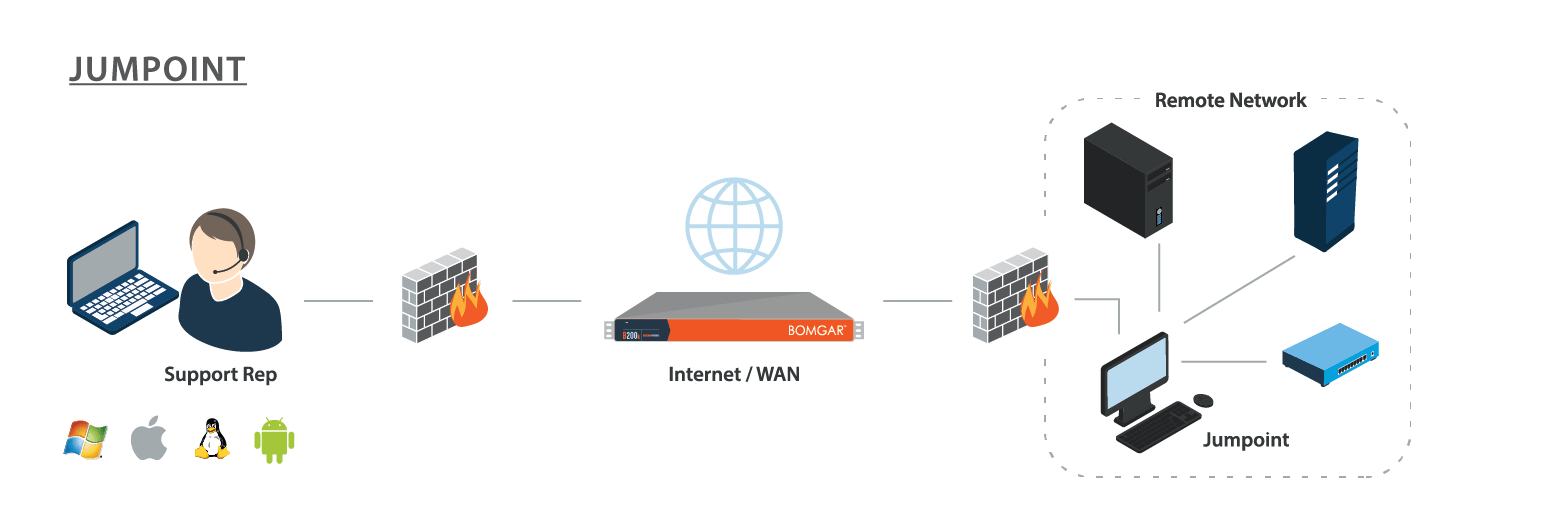
A Jumpoint acts as a conduit for access to computers on a known remote network. A single Jumpoint installed on a computer within a LAN is used to access multiple systems, eliminating the need to pre-install software on every computer you might need to access.
Within a LAN, the BeyondTrust user's computer can initiate a session to a system directly without using a Jumpoint, if appropriate user permissions are enabled. This is called a Local Jump. A Jumpoint is needed only for a Remote Jump when the BeyondTrust user's computer cannot access the target computer directly.
- Use Jump Shortcuts to Access Unattended Computers from the Android Representative Console
- Use Jump Clients to Access Unattended Computers from the Android Representative Console
- Use Jump Shortcuts to Access Unattended Computers from the iOS Representative Console
- Use Jump Clients to Access Unattended Computers from the iOS Representative Console