Workstyles
Endpoint Privilege Management for Windows Workstyles are used to assign Application Groups for a specific user, or group of users. The Workstyle wizard can generate Application Rules depending on the type of Workstyle you choose.
Workstyle Properties
To edit the advanced properties for a Workstyle:
- Expand the Workstyles node and select the relevant Workstyle.
- Right-click and select Edit Workstyle Options.
Privilege Monitoring
Endpoint Privilege Management for Windows can monitor the behavior of specific privileged applications and processes in Windows, a feature called privilege monitoring. Privilege monitoring is enabled as an auditing option in the properties of an Application Rule or an On-Demand Application Rule. When enabled, Endpoint Privilege Management for Windows records all privileged operations performed by the application or process that would fail under a standard user account. These include file operations, registry operations, and any interactions with other components such as Windows services.
The application must be running under a privileged account, such as an administrator or power user. Alternatively, an application could be running with elevated privileges because you added it to the Application Rules or On-Demand Application Rules section of the Workstyle and assigned it to run with admin rights.
Privilege monitoring logs are recorded on each endpoint, and the logs can be accessed using the Endpoint Privilege Management Reporting MMC snap-in. The configuration of privilege monitoring logs is applied to each Workstyle.
For more information about privilege monitoring contact your BeyondTrust consultant.
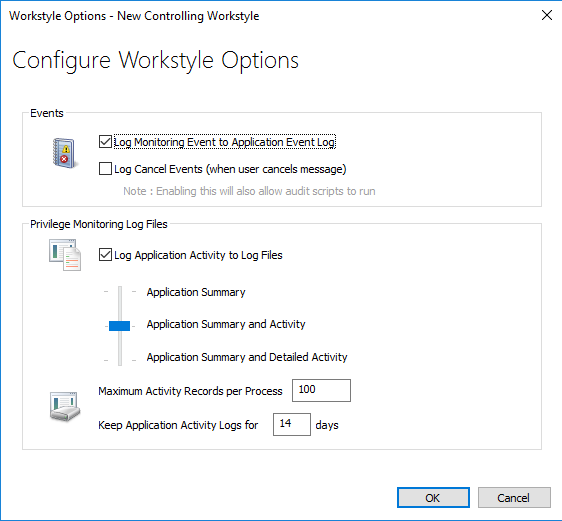
Privilege Monitoring Events
- Log Monitoring Event to Application Event Log: This option logs an event to the Application event log the first time an application performs a privileged operation.
- Log Cancel Events (when user cancels message): This option raises an event when a user cancels an End User Message, either by clicking the Cancel button, Email button, or clicking a Hyperlink. The action performed by the user is available as a Policy Parameter [PG_ACTION], which can be used by the script to perform different audit actions based on the user interaction. To log Cancel Events, enable Raise an Event for the rule that has been matched.
For more information, see Raise an Event.
Privilege Monitoring Log Files
The following Privilege Monitoring options are available:
- Log Application Activity to Log Files: This option enables logging of privileged activity to log files. The activity level can be set with the activity slider.
- Application Summary and Activity: This option logs information about the application and unique privileged activity (Default option).
- Application Summary and Detailed Activity: This options logs information about the application and all privileged activity.
- Maximum Activity Records Per Process: This option determines the maximum number of records that are recorded per process (Default 100).
- Keep Application Activity Logs for: This option determines how long activity logs are kept before they are purged (Default 14 days).