Create and edit directory credentials
A directory credential is required for querying Active Directory (AD), Entra ID, and LDAP. It is also required for adding AD, Entra ID, and LDAP groups and users in BeyondInsight. Follow the steps below for creating each type of directory credential.
Before you can create an Entra ID credential, you must first register and configure permissions for an application in the Entra ID tenant where the user credentials reside. For more information, please see Register and Configure an Application in Entra ID.
To create a directory credential in BeyondInsight:
- Navigate to Configuration > Role Based Access > Directory Credentials.
- Click Create New Directory Credential.
- Follow the steps in the applicable section below, based on the type of directory you are creating.
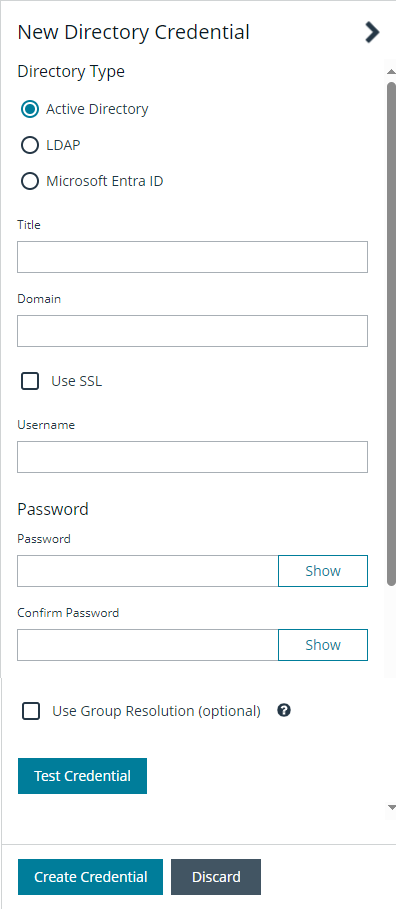
Create an Active Directory credential
- Select Active Directory for the Directory Type.
- Provide a name for the credential.
- Enter the name of the domain where the directory and user credentials reside.
- Enable the Use SSL option to use a secure connection when accessing the directory.
If Use SSL is enabled, SSL authentication must also be enabled in the BeyondInsight configuration tool.
- Enter the credentials for the account that has permissions to query the directory.
- Enable the Use Group Resolution option to use this credential for resolving groups from the directory.
Only one credential can be set for group resolution per domain or server.
- Click Test Credential to ensure the credential can successfully authenticate with the domain or domain controller before saving the credential.
- Click Create Credential.
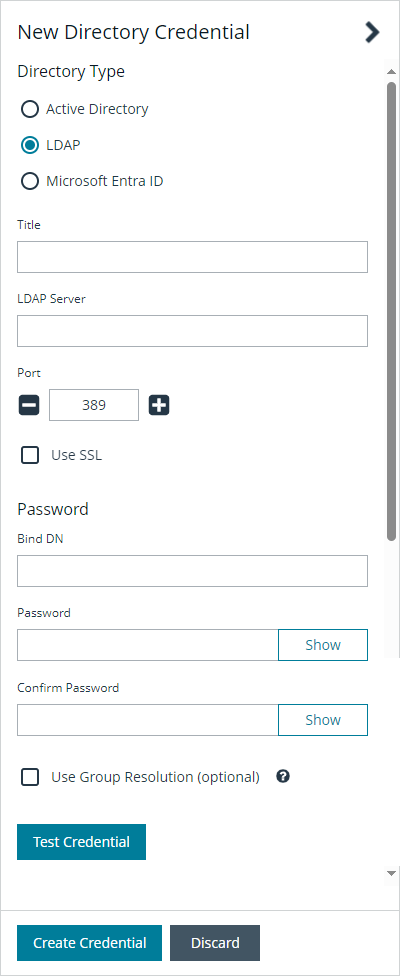
Create an LDAP credential
- Select LDAP for the Directory Type.
- Provide a name for the credential.
- Enter the name of the LDAP server where the directory and user credentials reside.
- Enable the Use SSL option to use a secure connection when accessing the directory.
If Use SSL is enabled, SSL authentication must also be enabled in the BeyondInsight configuration tool.
- Enter the credentials for the account that has permissions to query the directory.
- Enable the Use Group Resolution option to use this credential for resolving groups from the directory.
Only one credential can be set for group resolution per LDAP server.
- Click Test Credential to ensure the credential can successfully authenticate with the domain or domain controller before saving the credential.
- Click Create Credential.
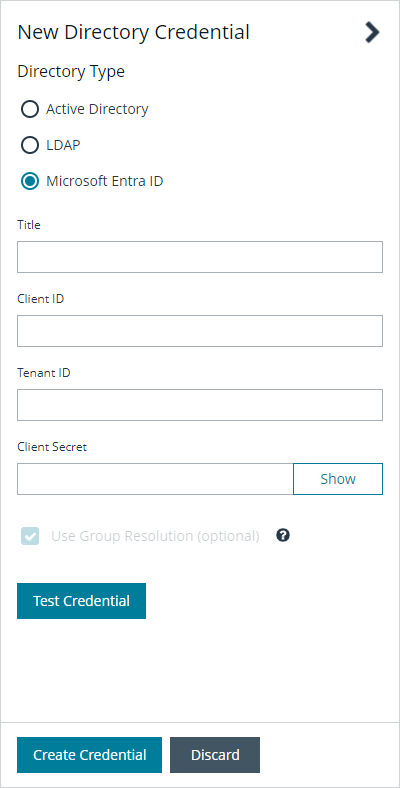
Create an Entra ID credential
- Select Microsoft Entra ID for the Directory Type.
- Provide a name for the credential.
- Paste the Client ID, Tenant ID, and Client Secret that you copied when registering the application in your Entra ID tenant.
- Enable the Use Group Resolution option to use this credential for resolving groups from the directory.
Only one credential is supported per Entra ID tenant.
- Click Test Credential to ensure the credential can successfully authenticate with the domain or domain controller before saving the credential.
- Click Save Credential.
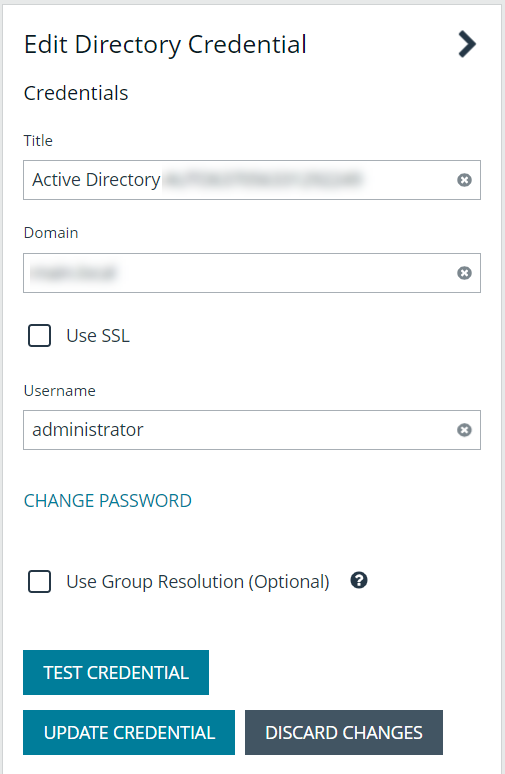
Edit a directory credential
- From the Directory Credentials grid, click the vertical ellipsis for the credential, and then select Edit.
- Make the changes required.
For AD or LDAP credentials, if you change the Domain or LDAP Server, enable or disable the Use SSL option, or update the Username or Bind DN, you must change the password. Click Change Password to display fields to enter and confirm the new password.
- Click Test Credential to ensure the edited credential can successfully authenticate with the domain or domain controller before saving the credential.
- Click Save Credential.
To use Entra ID credentials for logging into BeyondInsight, the accounts must use SAML authentication. For more information on configuring Entra ID SAML with BeyondInsight, please see Configure Microsoft Entra ID SAML with BeyondInsight SAML.