 If the Melissa virus from 1999 taught us anything – macro viruses could self-propagate and infect millions of computers in a short period of time. In 2000, the birth of modern social engineering occurred with the “I Love You” virus. It leveraged Visual Basic scripts and caught unwitting users off guard with a simple message of “I Love You” from a secret admirer. The attachment was the payload. If a user tried to open it, the malware was copied to various hidden places on the computer, modified the registry, downloaded a payload to steal passwords, and then self-propagated itself to other users in your address book with the same provocative message of love. If the next person opened the attachment to see who their secret admirer was, the entire process would execute again and attempt to steal passwords and relay them via email. A simple message of love was preying on people and stealing passwords. Cybersecurity love, or XO, has not changed. Threat actors still want to steal your passwords and today they are even more creative than sending you an email with false hopes of love — or are they?
If the Melissa virus from 1999 taught us anything – macro viruses could self-propagate and infect millions of computers in a short period of time. In 2000, the birth of modern social engineering occurred with the “I Love You” virus. It leveraged Visual Basic scripts and caught unwitting users off guard with a simple message of “I Love You” from a secret admirer. The attachment was the payload. If a user tried to open it, the malware was copied to various hidden places on the computer, modified the registry, downloaded a payload to steal passwords, and then self-propagated itself to other users in your address book with the same provocative message of love. If the next person opened the attachment to see who their secret admirer was, the entire process would execute again and attempt to steal passwords and relay them via email. A simple message of love was preying on people and stealing passwords. Cybersecurity love, or XO, has not changed. Threat actors still want to steal your passwords and today they are even more creative than sending you an email with false hopes of love — or are they?
Social Engineering Hasn’t Changed, but the Tactics Have
The social engineering aspects of installing malware have been the same for the last 19 years. The goal is to convince an unsuspecting user to open a file, click on a link, or perform some action that executes malware or leverages an exploit. Once the deed is done, the threat actor has a beachhead. One thing that has changed is the nature of phishing emails. Preying on someone with “I Love You” seems trivial compared to a modern spear phishing email from a colleague asking you to review a document or wire money to an account. The difference is, 19 years ago these attacks were done for fun or to cause a disruption – just because a hacker could. Today, the goal is political, hacktivism, or to just plainly make money. That’s the difference. The love for an attack is for a purpose and no longer a gag or silly passion of gloating rights. Threat actors have changed the binary nature of an attack from “because I could” to “I did because”, and this is why as security professionals we need to remember the past in order to adjust for future threats. It is a simple history lesson. So where is this blog going? Most of us have a love for our country but loath paying taxes. It is one of those binary evils that is required to sustain our government and way of life. Threat actors however do not care and have preyed for years on IRS scams and methods to extort tax refunds and payments from individuals. The latest round is the exact opposite of love, fear or anger. Take a look at the voice mail transcription below from a threat actor posing as the IRS (a secret admirer):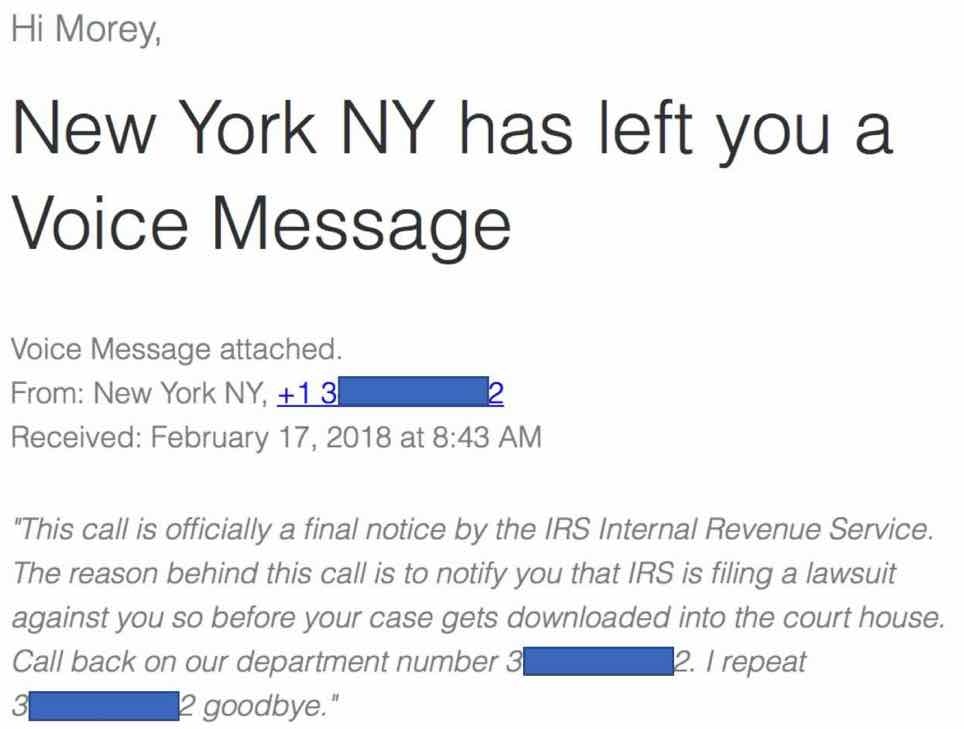 For this to succeed, there are several variations of the scam that leverage a message like this:
For this to succeed, there are several variations of the scam that leverage a message like this:
- Unexpected refund deposits to your bank account using compromised bank routing information
- Suspicious paper checks coming in the United States Postal Service (USPS) from fake sources claiming to be the IRS
- A fraudulent refund check being deposited by compromised or stolen smartphone

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








