
There is a nasty new finding applicable to Windows hosts (tablets, convertibles, and some laptops) with handwriting recognition enabled. According to Techspot and B2dfir, Windows contains a file called WaitList.dat which has been found to contain exposed text from email, contacts, and written documents when processed using handwriting recognition. The data is used by the Windows Search Indexer Service so that handwriting recognition can also be included within search requests. But this is a nasty side effect associated with indexing. It also creates a single point – although in a locked file – for a variety of sensitive information and history to reside with no mitigation for cleanup, encryption, or protection.
The file itself is located at the following path:
C:\Users\%User%\AppData\Local\Microsoft\InputPersonalization\TextHarvester\WaitList.dat
Testing the Problem
If you would like to see the potential risk for yourself, handwriting recognition and indexing must be enabled in order for the file to populate. To do so, make sure these pre-requisites are enabled and open Word, OneNote, or your favorite text editor. Using the handwriting recognition function on your touch-enabled screen, write a few sentences or something uniquely identifiable. Then save the file. After a few hours, Windows will index the text and populate the WaitList.dat file. Then, open the file and you will see the processed indexed text. Simply shocking.
What are the Risks? What are the Steps to Mitigation?
Currently, there is no known malware or threats that target this file but with the recent public disclosure, it will only be a few weeks before something will show up in the wild. For those in highly secure environments, there are a few mitigation procedures to take until Microsoft devises a method to encrypt or protect this file:
- Using Group Policy, disable handwriting recognition on all affected devices: HKEY_CURRENT_USER\SOFTWARE\Microsoft\InputPersonalization.
- Educate team members not to use handwriting recognition when documenting sensitive information until a remediation is available.
- Implement File Integrity Monitoring with PowerBroker for Windows to restrict access from individual users and only allow the System to access the file.
To implement the last recommendation, create a rule similar to this example (it may vary based on your implementation):
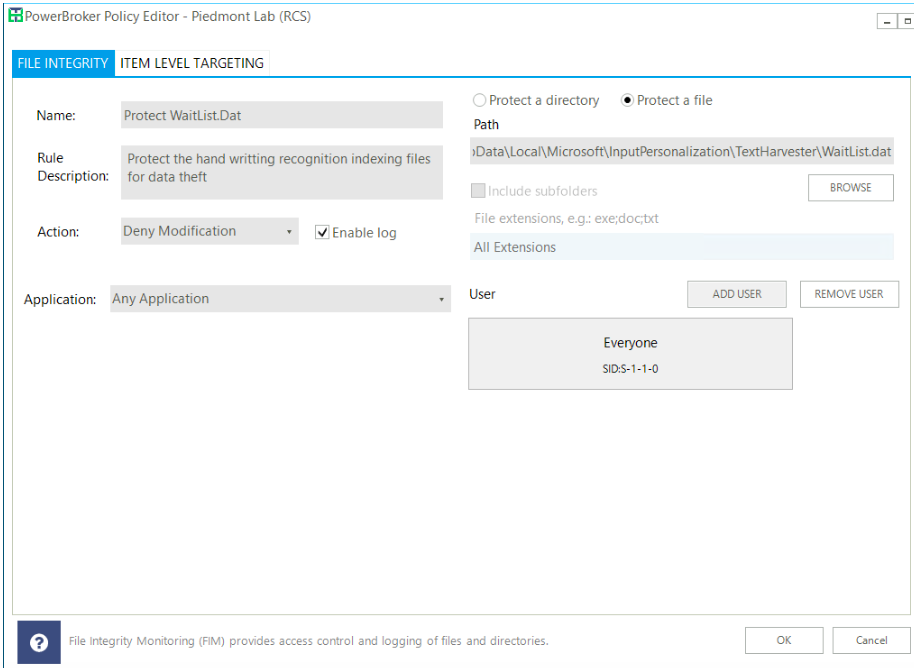
This will block all access (Everyone) and should allow the System to still process the file.
While this potential flaw appears all the way back to Windows 8 (and potentially earlier), the risks for data exposure should not be ignored. If you’d like to learn more about how PowerBroker for Windows can protect access to this file, or any other on your resources, contact us today.

Morey J. Haber, Chief Security Advisor
Morey J. Haber is the Chief Security Advisor at BeyondTrust. As the Chief Security Advisor, Morey is the lead identity and technical evangelist at BeyondTrust. He has more than 25 years of IT industry experience and has authored four books: Privileged Attack Vectors, Asset Attack Vectors, Identity Attack Vectors, and Cloud Attack Vectors. Morey has previously served as BeyondTrust’s Chief Security Officer, Chief Technology, and Vice President of Product Management during his nearly 12-year tenure. In 2020, Morey was elected to the Identity Defined Security Alliance (IDSA) Executive Advisory Board, assisting the corporate community with identity security best practices. He originally joined BeyondTrust in 2012 as a part of the acquisition of eEye Digital Security, where he served as a Product Owner and Solutions Engineer, since 2004. Prior to eEye, he was Beta Development Manager for Computer Associates, Inc. He began his career as Reliability and Maintainability Engineer for a government contractor building flight and training simulators. Morey earned a Bachelor of Science degree in Electrical Engineering from the State University of New York at Stony Brook.








