What's with the Vulnerability Management Madness?
The end of year holidays are often a time for reflection. And with Black Friday only a little more than a month away, I thought it would be as good a time as any to stop and ask the question, “Are we winning or losing the vulnerability battle?”
Over the past 20 some odd years, tens of thousands of organizations have collectively spent hundreds of millions of dollars trying to eradicate dangerous vulnerabilities from their software and systems. “Find, fix, automate and repeat” has been the battle cry of many IT security pros as they march into combat hoping to come out unscathed or at least victorious over their vulnerability nemeses. However, despite widespread deployment of vulnerability management technologies, few seem to be able to decisively put a “✓” in the win column.
Some folks might say that we are effectively treading water, not gaining ground, but not losing any either. However, this argument mostly refers to new versus patched vulnerabilities, and doesn’t really consider how we are faring against those vulnerabilities that are being exploited in the wild.
To answer the question, let’s look at a few data points that will help us determine whether or not the good guys are keeping pace. After which, we’ll consider a few industry-wide realities that continue to plague existing vulnerability management programs.
It's time to get your vulnerability management under control. Download our white paper, 10 Reasons to Rethink Your Vulnerability Management, and discover how you can stay steps ahead of the bad guys. Or request a free trial today.
Breaches Continue to Rise
The following chart shows the number of reported data breaches from several well-known sources. And while the numbers may vary between sources, we can see from the data that the number of breaches continues to rise.
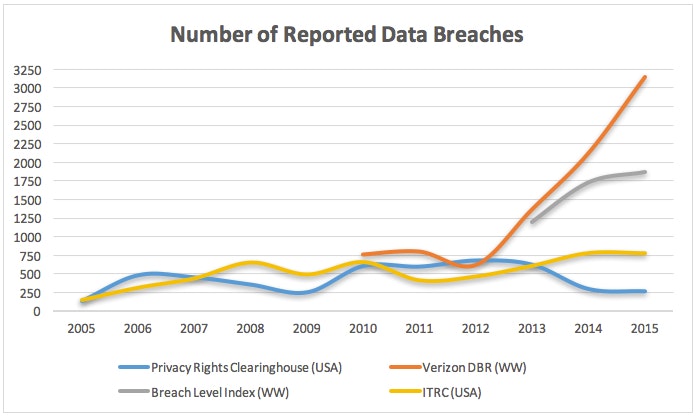
And while not every data breach results from an exploited vulnerability, it’s a safe bet that those are growing right alongside all the other breach types.
The Gap is Widening
Another metric to consider is how long it’s taking us to remediate vulnerabilities. While the numbers vary (HPE = 60 days, Kenna = 110 days, and Nopsec = 176 days), let’s assume that aggressively it takes an organization 30 days to close a known critical vulnerability. That’s reasonable right? And it’s what most compliance initiatives require.
Well, unfortunately for us, attackers have been getting faster at weaponizing exploits. IBM X-Force recently found that over the past ten years, the time it takes from when a vulnerability is publicly announced to when it’s first exploited has plunged from 45 to 15 days. That means, in the best case scenario many of us are sitting in the cross hairs of exploitable vulnerabilities for at least a few weeks.
Oldies but Goodies
Lastly, let’s look at how effective we’ve been at closing the security weaknesses we collectively know about. Last year, Verizon reported that 99.9% of exploited vulnerabilities had a CVE for more than one year – that hasn’t changed – and completely flips our best case scenario on its head.
In addition, the Verizon 2016 DBIR points to the fact that although millions of vulnerabilities exist, there are only about 900 that are actively being exploited in the wild. And while that could be construed as good news, the fact that almost one third of these are more than a decade old isn’t something to celebrate, but rather something to continue debating within security circles.
It’s a Big Ocean Out There
Everything from malware to Shadow IT can derail even the best laid vulnerability management plans. Here are a few realities that illustrate why many businesses continue to struggle with stamping out known weaknesses.
The sheer number of vulnerabilities makes it extremely challenging for most organizations to be able to determine which ones they should focus on fixing. And while only a small percentage of the millions of vulnerabilities ever actually get exploited, the number of new vulnerabilities continues to pile up year after year.
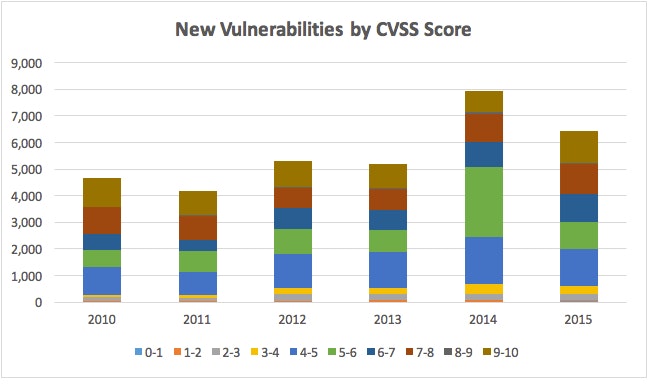
(Source CVE Details)
While it’s ludicrous for any organization to even attempt to fix just these estimated 35,000 vulnerabilities, the large cumulative number makes weeding through and identifying the few hundred, that pose the greatest danger, that much more difficult.
Evil Lurks in the Shadows
On top of what IT organizations are responsible for, Shadow IT continues to infiltrate organizations at an alarming rate. Cisco’s 2016 Cloud Consumption report recently concluded that on average organizations use twenty times as many cloud-based services than IT is aware of. And Gartner predicts that in less than five years approximately one-third of all successful enterprise attacks will occur against Shadow IT resources.
Let’s Change the Game
Despite the progress made within the past couple years, both reporting and patching vulnerabilities, it appears that we’ve been unable to turn the tide in our favor. For the better part of two decades, organizations have been treading water struggling to stay afloat. If we cannot address today’s known vulnerabilities, how can we as a security community expect to tackle the evolution of ransomware, malware for mobile phones, billions of defenseless devices and gangs of cyber mercenaries – lurking just offshore?
Let’s change the vulnerability game for ourselves and our adversaries by connecting the dots between our various IT and security solutions, to remove the enemies’ soft targets. It’s time to enlist the eyes and ears of your “security village”, automate their interactions, coordinate their intelligence and surround your foes to pinpoint and eliminate high risk vulnerabilities and uncover and track emerging threats.
Want to Win? Check out my blog, Managing Vulnerabilities Takes a Village, and download our latest white paper, 10 Reasons to Rethink Your Vulnerability Management, to discover how you can stay steps ahead of the bad guys. For more, contact us or request a free trial today!

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.









