
This week’s revelation that hackers working for Russia gained access to the control rooms of certain US electric utilities in the last year is a stark reminder that our daily lives are dependent, in some situations, on outdated, difficult-to-upgrade vulnerable systems that pose life-or-death risks if those systems suddenly go offline. Let’s review the anatomy of this attack and controls that can mitigate these risks going forward.
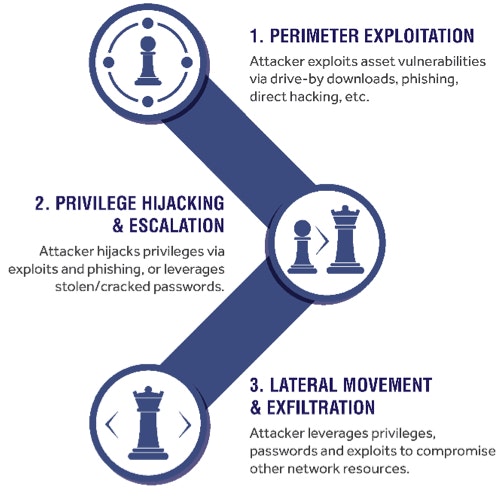 Method of Cyber-Attack
Method of Cyber-Attack
The Department of Homeland Security (DHS) reports that the hackers utilized third-party vendors that had relationships with the power companies, sending spear-phishing emails and using watering-hole attacks to target a specific group of users (very similar tactics publicly-reported in the now-infamous 2013 Target breach). Once they gained access to the third-party vendor networks, hackers sought out the highest-level privileged credentials available to access the utility networks and move laterally. The Wall Street Journal reported that since the attacks used legitimate credentials to gain access to the networks, it’s possible that some utilities don’t know they’ve been compromised. This is a very common method of attack that we call the Cyber Attack Chain.
The Problem – Outdated, Interconnected Systems
Critical infrastructure systems that span transportation, water supply, and energy have historically relied considerably on physical separation as the primary means for security. However, modern control system architectures, management processes, and cost control measures have resulted in increased integration of corporate and ICS/SCADA environments. While these interconnections increase operational visibility and control, they can also increase risks that previously did not occur with isolated ICS/SCADA. Through an interconnected network, the ICS/SCADA system can be exposed to threat actors who have already exploited and compromised the Internet and corporate networking, or by insiders misusing their privileges (like in the 2015 Ukraine blackout).
Eliminating as Many Attack Surfaces as Possible
ICS-CERT (Industrial Control Systems Cyber Emergency Response Team) provides ICS-CERT alerts to assist owners and operators in monitoring threats and actions that could impact ICS/SCADA systems. To address these risks, ICS-CERT encourages sound security practices using “defense-in-depth principles.” A brief summary of the controls and recommendations include:
- Secure Passwords: Remove, disable, or rename any default system accounts wherever possible.
- Strong Password Management: Establish and implement policies requiring the use of strong passwords.
- Reduce Risks of Brute-Force Attacks: Implement account lockout policies to reduce the risk from brute-force attacks.
- Minimize Network Exposure: This activity includes the implementation of firewalls and network segmentation. This can reduce the attack surface as well as the risk of lateral movement within a compromised environment.
- Secure Remote Access: This activity includes deployment and appropriately updating remote access solutions, such as VPN, if required.
- Third Party Vendors: Monitor the creation of administrator-level accounts by third-party vendors.
- Vulnerability Management: Apply patches in the ICS environment, when possible, to mitigate known vulnerabilities.
- Threat Detection: ICS-CERT recommends that organizations monitor for suspect activities, and to report their findings to ICS-CERT for incident response support and correlation with other similar incidents.
10 Ways BeyondTrust Can Help
By integrating the disciplines of vulnerability management, privileged access management, and threat analytics into a single solution, BeyondTrust can help organizations meet the requirements recommended by ICS-CERT.
- Prioritize and patch system vulnerabilities that can serve as gateways into your environment, utilizing a large ecosystem of security solutions integrated for more insights
- Ensure systems are properly configured against industry-standard benchmarks and best practices
- Eliminate the sharing, insecure management, or re-use of privileged accounts and their passwords, enforcing a workflow-based approach that uses context to determine access
- Eliminate embedded or hard-coded passwords in applications
- Enforce least privilege across all desktops, laptops, servers, or other network endpoints in your environment, controlling the use of applications and elevating privileges by exception only
- Use the vulnerability status of a target asset to help you make decisions on whether or not to elevate privileges to it
- Enforce proper network segmentation, setting up a secure enclave where third-parties have only controlled access that you allow, with a complete monitored audit trail in real-time
- Monitor all user sessions when privileges are employed for access to critical systems
- Monitor for unauthorized changes to files and directories
- Analyze behavior to detect suspicious user, account and asset activity
For more on how our solutions map to the recommendations in ICS-CERT, check out the white paper, Securing Industrial Control Systems (ICS) with BeyondTrust Solutions. Employing this framework will reduce risk and provide a stronger, more flexible security foundation that will enable organizations to prevent and respond effectively to these threats.

Scott Lang, Sr. Director, Product Marketing at BeyondTrust
Scott Lang has nearly 20 years of experience in technology product marketing, currently guiding the product marketing strategy for BeyondTrust’s privileged account management solutions and vulnerability management solutions. Prior to joining BeyondTrust, Scott was director of security solution marketing at Dell, formerly Quest Software, where he was responsible for global security campaigns, product marketing for identity and access management and Windows server management.








